Appendix B: Enable PowerShell remoting using group policy
Thanks to Jan Egil Ring for contributing this section to the eBook. His blog was probably the first ever to post detailed steps on how to enable remoting using group policy.
This section will show you how PowerShell remoting can be enabled for Windows Vista, Windows Server 2008 and above. For Windows XP and Windows Server 2003, running Enable-PSRemoting in a PowerShell startup script would be the best approach.
Group Policy Configuration
Open the Group Policy Management Console from a domain-joined Windows 7 or Windows Server 2008 R2 computer.
Create or use an existing Group Policy Object, open it, and navigate to Computer Configuration>Policies->Administrative templates->Windows Components
Here you will find the available Group Policy settings for Windows PowerShell, WinRM and Windows Remote Shell:
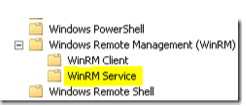
To enable PowerShell Remoting, the only setting we need to configure are found under “WinRM Service”, named “Allow automatic configuration of listeners”:
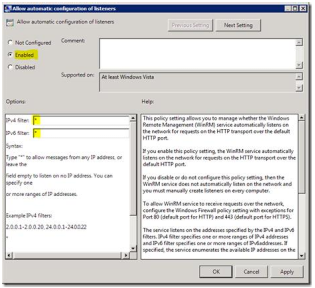
Enable this policy, and configure the IPv4 and IPv6 addresses to listen on. To configure WinRM to listen on all addresses, simply use *.
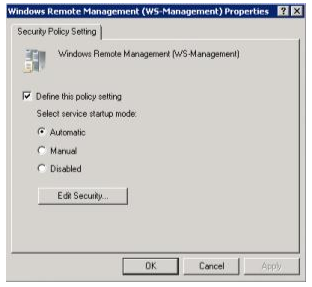
In addition, the WinRM service is by default not started on Windows client operating systems. To configure the WinRM service to start automatically, navigate to Computer Configuration\Policies\Windows Settings\Security Settings\System Services\Windows Remote Management, double-click on Windows Remote Management and configure the service startup mode to “Automatic”:
No other settings need to be configured, however, I`ve provided screenshots of the other settings so you can see what`s available:
There is one more thing to configure though; the Windows Firewall.
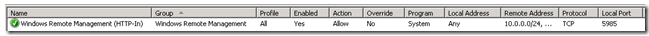
You need to create a new Inbound Rule under Computer Configuration->Policies->Windows Settings>Windows Firewall with Advanced Security->Windows Firewall with Advanced Security->Inbound Rules:
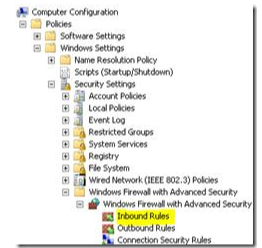
The WinRM port numbers are predefined as “Windows Remote Management”:
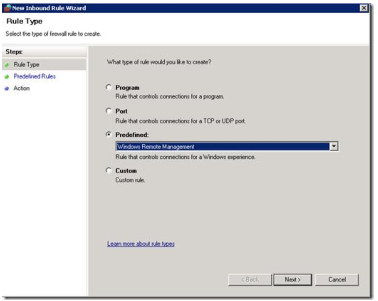
With WinRM 2.0, the default http listener port changed from TCP 80 to TCP 5985. The old port number are a part of the predefined scope for compatibility reasons, and may be excluded if you don`t have any legacy WinRM 1.1 listeners.
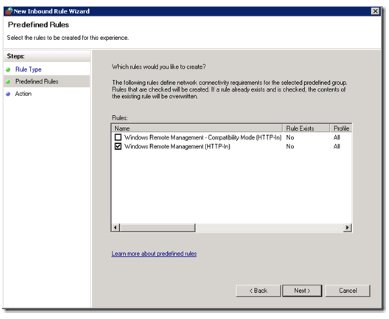
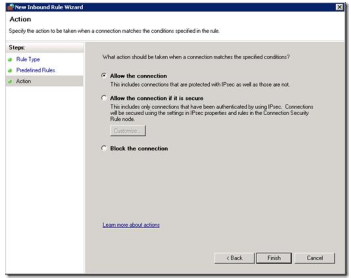
When the rule are created, you may choose to make further restrictions, i.e. to only allow the IP addresses of your management subnet, or perhaps some specific user groups:
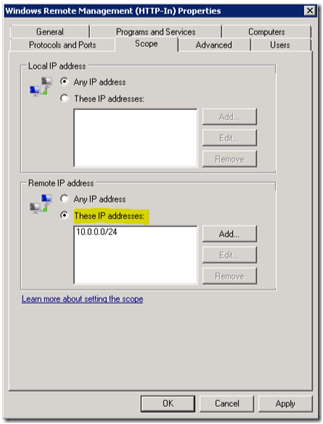
Now that the firewall rules are configured, we are done with the minimal configuration to enable PowerShell Remoting using Group Policy.
On a computer affected by the newly configured Group Policy Object, run gpupdate and see if the settings were applied:
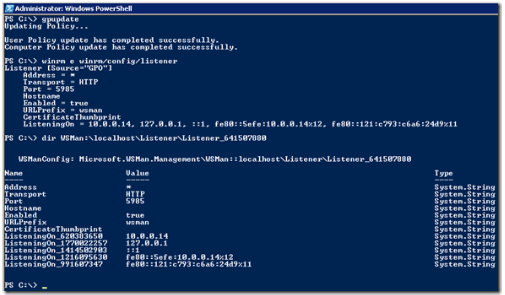
As you can see, the listener indicates “Source*”GPO”, meaning it was configured from a Group Policy Object.
When the GPO has been applied to all the affected computers you are ready to test the configuration.
Here is a sample usage of PowerShell Remoting combined with the Active Directory-module for Windows PowerShell:
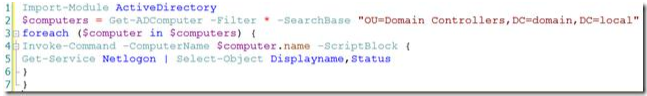
You can also use the Test-PSremoting (http://www.leeholmes.com/blog/2009/11/20/testing-for-powershell-remoting-test-psremoting/ ) script by Lee Holmes to verify that PS remoting is enabled on remote systems.

















