Research network
Figure 4.12 Example of a multi-server IP Telephony zone
This scenario is quite complex, but it is the most flexible. It allows individual users to move from the legacy telephony world to IP Telephony, eventually reducing the PBX to a minimal state. It is made robust by using redundant servers where necessary. Because routing decisions are made on the IP-side, this solution qualifies for communication with external targets via the Internet or through use of an IP Telephony provider.The decision for open standards (SIP, H.323) allows space for research initiatives and prevents dependency on specific vendors.
All these possibilities come at a price. Several servers must be bought and the complex structure makes it harder to trace errors.
~ 4.5 Setting up H.323 services
When setting up H.323 services, the basic component to install is a gatekeeper, in order to provide initial functionality to an installed base of H.323 clients.This basic functionality entails:
- in-zone calling among endpoints;
- out-of-zone calling (incoming/outgoing);
- access to local services (e.g., gateways, multi-point conference servers);
- name resolution during calls, by H.323 alias or E.164 number;
- zone management (authentication, bandwidth restriction, etc.).
In this section, guides will be presented for running the three most popular gatekeeper implementations that are available today. A comparison of these gatekeeper implementations, based on their capabilities and requirements, follows here:
P.84
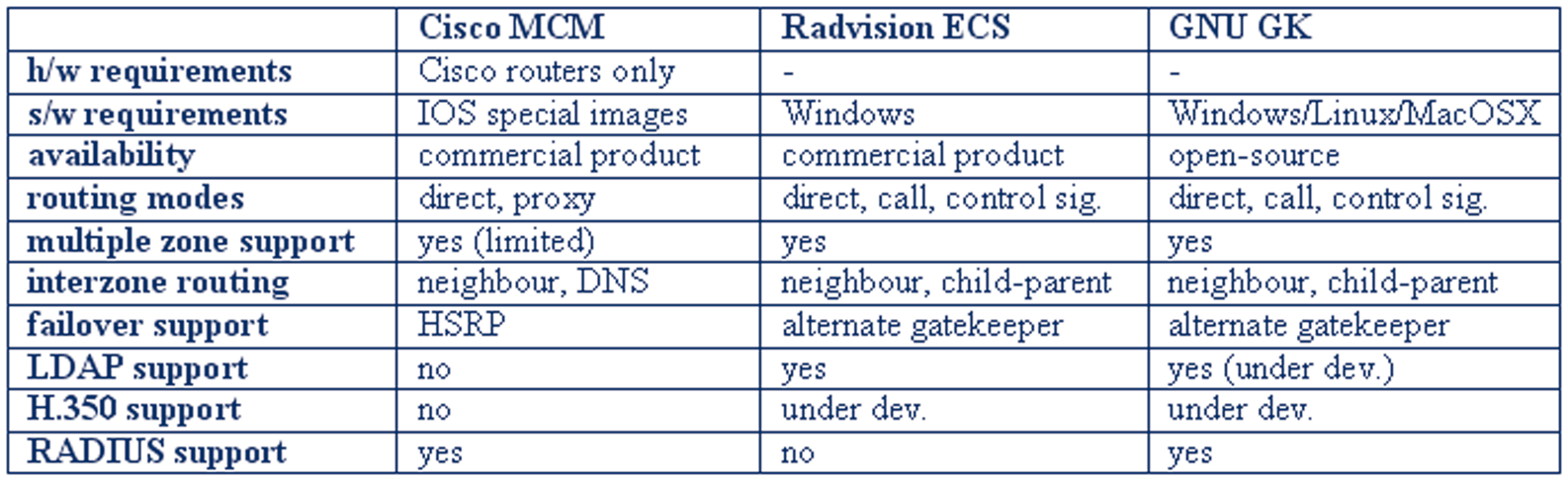
[IP Telephony Cookbook] / Setting Up Basic Services
Figure 4.13 Examples of gatekeeper features
Guides for basic operation of the above three gatekeepers follow, but official documentation for these products should be consulted when advanced functionality and features are required.
~ 4.5.1 Using a Cisco Multimedia Conference Manager (MCM Gatekeeper) The Cisco MCM is a software gatekeeper that runs only on Cisco router hardware with special IOS images (H.323 feature set). One the one hand, this makes it easy to find a hardware platform for running it within most organisations that use Cisco hardware, without regard for underlying operating system support. On the other hand, it does not allow the flexibility of installation on any available PC-based server. It is a commercial-grade implementation, mostly geared towards VoIP gateway services and less towards an open H.323 community of endpoints that possibly spans organisational borders.The MCM supports either direct mode dialling, or full routing mode, through the use of an included H.323 proxy server. Multiple H.323 zones can be configured and controlled on one MCM installation, but only in combination with subnet restriction rules for groups of endpoints.The MCM has good inter-zone routing features with DNS gatekeeper discovery as extra and performs well in a homogeneous Cisco environment, but has only basic support for RADIUS-based authentication (by H.323 alias or E.164 and proprietary piggy-back password mechanism) and no support for LDAP H.350 authentication.
Cisco MCM VC: Configuring H.323 Gatekeepers is online. 3
~ 4.5.1.1. Installation
Since the Cisco MCM Gatekeeper is only an IOS feature (IOS being the Cisco router operating system), basic IOS installation procedures are sufficient, assuming a correct IOS image with MCM
functionality has been chosen from the Cisco support site.Two tools can help you choose an appropriate IOS for your available router, but they are only available to registered users on the Cisco Website:
- Cisco IOS Upgrade Planner
- Cisco Software Advisor.
Look for ‘High-Performance Gatekeeper’ under features and for ‘IP/H.323’ under feature sets.
IOS versioning is a subject difficult to follow. Add to this the fact, that the MCM has been 3. http://sourceforge.net/projects/openh323proxy/
P.85
[IP Telephony Cookbook] / Setting Up Basic Services
undergoing changes during IOS development and gatekeeper features available on different IOS
versions vary significantly. Finding the right IOS-MCM combination to use for a specific hardware configuration can become time consuming. Always prefer the latest available IOS release for your hardware, assuming enough RAM is available to accommodate it.
~ 4.5.1.2 Configuration
Working with the Cisco IOS command line interface requires some experience with basic commands, modes of operation, loading software images and configuration files, none of which will be described here in detail. If you are not familiar with Cisco IOS basic commands, make sure you read an introductory guide by Cisco.To configure the Cisco MCM, you must establish command line access (telnet) to the router that runs the ‘IP/H.323’ feature set and enter privileged (enable command) mode, indicated by the # at the prompt, before you can enter configuration commands. Enter configuration mode (config command) and then specify the
‘gatekeeper’ section. In this section, you will need to enter the MCM configuration commands, as in the sample below, which merely initialises the gatekeeper operation: gkp#config
Configuring from terminal, memory, or network [terminal]?
Enter configuration commands, one per line. End with CNTL/Z.
gkp(config)#gatekeeper
gkp(config-gk)#zone local gkp.mydomain.org mydomain.org
gkp(config-gk)#no shutdown
gkp(config-gk)#^Z
The above sample is sufficient to start gatekeeper services on the router, but a more detailed configuration with comments for a basic gatekeeper set-up follows.We have dropped the command line prompt for simplicity.The following commands can be typed at the configuration interface, as shown above. Note that all user-specified fields are indicated as enclosed in brackets and you must customise/replace them appropriately for your site.
This section goes outside the gatekeeper configuration section as it relates to general AAA settings and RADIUS server communication. H.323 endpoint RAS registration will be checked against local IOS usernames first and then RADIUS-defined usernames. Accounting records will be sent to the RADIUS server.
!
aaa new-model
aaa authentication login h323 local group radius
aaa accounting connection h323 start-stop group radius
!
radius-server host [radius.mydomain.org] auth-port [1812] acct-port
[1813]
radius-server key [radius-server-key-as-defined-in-radius-host]
radius-server authorisation permit missing Service-Type
!
P.86
[IP Telephony Cookbook] / Setting Up Basic Services
! Gatekeeper section
!
gatekeeper
!
! Local zone info, as controlled by this gatekeeper
! The zone name "myzone" is for config purposes only and plays no role,
! while the domain is important for endpoints registering by e-mail alias,
! as endpoints that request to be registered by e-mail address must match
! the specified "mydomain.org" part.
! The zone prefix is important for recognising
! in-zone calls and endpoints, e.g anything beginning with 0030234
!
zone local [myzone] [mydomain.org]
zone prefix [myzone] [0030234*]
!
To set up connectivity with other zones and gatekeepers, specify the IP of the neighbouring gatekeeper with a ‘zone remote’ and the prefix it services with a ‘zone prefix’ for that zone.
For example, if you know a neighbour gatekeeper handles all calls with prefix 0030248, include the following two lines.
!
zone remote [neighb1] [neighb1-domain.com] [neighb1-gkp-ip] 1719
zone prefix [neighb1] [0030248*]
!
The VideNet Gatekeeper, for example, is the largest global network of H.323 zones, to which you can connect as shown below. Any calls beginning with 00, are routed to the VideNet Gatekeeper.
In order to accept calls from VideNet as well, you have to make your gatekeeper well known to the VideNet hierarchy of gatekeepers (see https://videnet.unc.edu/)
!
zone remote videnet3 videnet 137.44.172.248 1719
zone prefix videnet3 00*
lrq forward-queries add-hop-count
!
To force endpoints to register with a specific h323-id and password you can use H.235
(few endpoints support it) or the h323-id/password mechanism that the MCM provides.
!
accounting
security h323-id
security password separator /
!
Make sure no H.323 proxy services are unintentionally used, unless proxy functionality is needed for security or QoS reasons.
!
no use-proxy [myzone] default inbound-to terminal
no use-proxy [myzone] default outbound-from terminal
P.87
[IP Telephony Cookbook] / Setting Up Basic Services
~ 4.5.1.3 Operation
Immediately after configuration, the MCM may service endpoints, and you can verify this by making a couple of endpoints point to the gatekeeper for registration. As soon as the endpoints register, they can be listed with the following command:
- show gatekeeper endpoints
You may proceed with calling between the two endpoints by dialling from the one the registered aliases (name or number) of the other.The ongoing call can be listed with the following command:
- show h323 gatekeeper calls
As an administrator of the gatekeeper, you may disconnect the call, or even unregister an endpoint.
- clear gatekeeper call call-id . . .
- unregister . . .
A view of the operational status of the gatekeeper, such as zones defined, endpoints registered, neighbour gatekeepers defined etc. may be displayed by the following command:
- show gatekeeper status
Debug logs of the gatekeeper operations may be monitored with the following sequence of commands:
terminal monitor
debug gatekeeper main 10
debug h225 asn1
debug h245 asn1
The first command makes your terminal capable of displaying console-style logs and debugging output.The second command produces debugging output regarding basic gatekeeper actions.
Obviously, the last two commands display information on H.225 and H.245 protocols and the output can be overwhelming, but it may be the only debugging option when faced with an otherwise intractable problem. Each debugging option can be stopped by its equivalent no debug and all debugging output can be stopped with the no debug all command.
~ 4.5.1.4 Endpoint authentication
The MCM Gatekeeper implements H.235 authentication, but its use is limited to gatekeeper-to-gatekeeper and gatekeeper-to-gateway authentication, because of the very limited deployment of H.235 capable endpoints. Cisco has implemented an alternative method for endpoint authentication, which allows for an H.323 or E.164 alias to carry (piggy-back) both alias information and a password, separated by an administrator-defined special character, for example, a configuration for this feature is provided above and once activated, endpoints must be configured to use alias/password combinations to register with the gatekeeper.There are P.88
[IP Telephony Cookbook] / Setting Up Basic Services
shortcomings to this method that stem mostly from the fact that it is a proprietary solution, which, in some cases, exposes clear text passwords to neighbouring devices (MCUs, gateways, gatekeepers). Of course, the MCM includes RADIUS support, which might allow for an IP
address + alias identification method to be implemented on the RADIUS server side, but such a solution imposes restrictions to endpoint mobility.
~ 4.5.1.5 Advanced features
The Cisco MCM supports RADIUS authentication and accounting to a remote RADIUS server.
With the extensive support of RADIUS servers to a number of back-ends, such as databases and directory services, this can be an important feature when seeking a method of integrating H.323
access control with already deployed services (e.g., dial-up, LDAP), or a simple way of storing call-accounting information in a database. Also, the exchange of standard and vendor-specific attributes during the RADIUS negotiation process allows very fine control of some delicate parameters, such as call duration, which would otherwise be inaccessible to an external-to-the-gatekeeper application. Of course, only experienced RADIUS administrators and middleware developers can exploit the full potential of the RADIUS configuration files and its back-end interfaces.The Cisco MCM supports an alternative method to neighbour-discovery than static neighbour entries in the IOS configuration. A DNS-based gatekeeper discovery mechanism is in place that allows the MCM to find gatekeepers responsible for a specific domain by checking for the existence of a TXT record in the domain's DNS zone information.This can be useful if a large community of users in separate zones employs e-mail addresses for dialling.The gatekeepers serving them do not need to have static knowledge of each other, but can discover destination gatekeepers responsible for a domain through DNS. Multiple zone support is implemented on the MCM in a way that allows multiple instances of the gatekeeper to run within one router.This would have been an excellent feature, if it could have avoided a major handicap: endpoint registration to a specific gatekeeper has to be guided by administratively preset IP address subnet restrictions. Interestingly enough, Cisco gateways can utilise this functionality by indicating on their RRQ messages (by gatekeeper ID and not by IP address) which gatekeeper they request to be registered with.
~ 4.5.2 Using a RADVISION Enhanced Communication Server (ECS Gatekeeper) The RASVISION ECS is a software-only gatekeeper that runs on the WinNT or Win2000
operating systems, a fact that ties it to specific remote management techniques used with all other Windows-based servers. It is a commercial-grade implementation and it is considered top-of-the-line for the features it provides and its compatibility even with the latest H.323 specifications. It is servicing large organisations with a great number of endpoints and most notably, some of the VideNet global root gatekeepers.The ECS supports all three modes of routing: direct, Q.931
routing and both Q.931 and H.245 routing.The ECS has good inter-zone routing features with DNS gatekeeper discovery and neighbour gatekeeper LDAP support as extra. Authentication is very flexible, with the ability for ‘predefined’ endpoint settings enforced at registration time and LDAP H.350 support, but no RADIUS support.
P.89
[IP Telephony Cookbook] / Setting Up Basic Services
~ 4.5.2.1 Installation
Installing the ECS Gatekeeper is a very simple task, since it involves merely the execution a GUI setup wizard, which requires no configuration options.The only potential source of installation problems lies with the fact that the Windows SNMP service must already be installed, before any service packs and the ECS installer are applied. If this advice, which is listed in the ECS
documentation, is ignored, the ECS installer refuses to proceed and the only option is to reinstall the operating system itself.
Also, the administrator of the host must make sure that port 80 is free, since the ECS installs an HTTP service on this default port for configuration management over a Web interface.The documentation also calls for an FTP server to be running at the same host, but it only serves for downloading ECS log files, which is not a required functionality.
~ 4.5.2.2 Configuration
Once installed, the ECS is ready to run with default configuration options.The administrator can access the management interface (see Figure4.14) by launching a browser and requesting the local Web server (http://localhost).The interface presents a login page, where the default username and password can be entered (admin/null-no-password). After successful login, the administrator is made aware of the fact that the management tool can supervise the operation of a whole hierarchy of ECS Gatekeepers (Global picture), as well as the single ECS installation residing on this host (Local picture). Proceed with the Local administrator interface.
Figure 4.14 ECS local administration entry
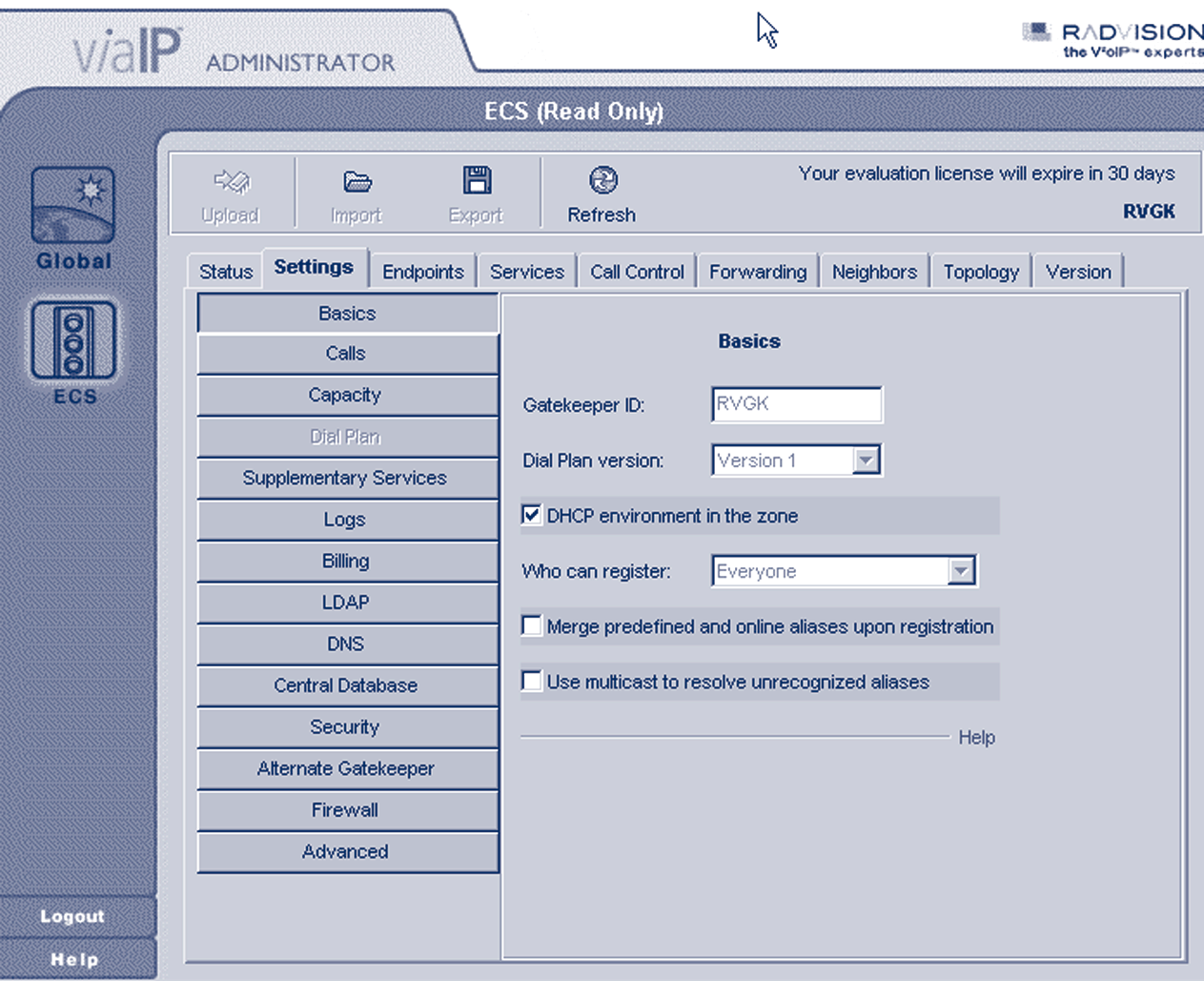
Immediately afterwards, the menus for the administration of the locally-installed gatekeeper are shown, as below.
There are four commands to allow configuration management.The Refresh button fills in the Web interface forms with configuration data from the currently-running ECS Gatekeeper configuration.The Upload button takes all the changes made on the Web interface and applies them to the currently-running ECS configuration.The Import and Export buttons are used to store and retrieve snapshots of the configuration at different points in time.
P.90
[IP Telephony Cookbook] / Setting Up Basic Services
Figure 4.15 ECS administration menus
The rest of the interface is fairly straightforward, with an array of configuration tabs (sections), the most important of which are listed below:
- Status tab: allows view of the current status of the gatekeeper by indicating the number of ongoing calls and registered endpoints, as well as bandwidth usage statistics for in-zone and out-of-zone calls;
- Settings tab: this is where most of the configuration options are specified, logically separated into a series of thematic categories (Basics, Calls, Dial Plan, Supplementary Services, Logs, LDAP, DNS, Security, Alternate Gatekeeper, Advanced);
- Endpoints tab: allows view and control of the currently-registered endpoints with details on their aliases (name and number), IP addresses and online time.This tab can be used to predefine endpoints, i.e. assign specific aliases to endpoints that may later be used for endpoint identification during authentication;
- Services tab: allows view and configuration of the currently declared services. By default, four services exist at installation time and they are not activated, since their prefix setting is null.
Therefore they merely exist as templates for defining basic services functionality;
- Call Control tab: allows view and control of the calls in progress and the setting up of gatekeeper-initiated calls between arbitrary endpoints, with the Make call option, assuming the gatekeeper runs in fully-routed mode (see the Signalling Models Section and the Settings tab, category Calls in the ECS interface);
- Forwarding tab: allows set-up of forwarding rules based on source and destination, for three cases: forward on busy, forward on no answer, unconditional forward;
- Hierarchy tab: allows set-up of a parent gatekeeper in order to forward Location Requests for cases of unresolved destinations. User-assigned filters may also be applied to specify and control the extent of the cases referred upstream to the parent gatekeeper.
P.91
[IP Telephony Cookbook] / Setting Up Basic Services
Even though the ECS Gatekeeper runs out-of-the-box, you may want to inspect some of its basic settings and decide whether they fit the needs of your application.There are three tabs that should be, at least browsed, through before proceeding with operation.
Under Settings tab, in the category Basic, make a note of the name of the gatekeeper (gatekeeper ID). Also, be aware of the setting who can register, where the choices are everyone for no authentication control, predefined endpoints only for some authentication control and no endpoints to turn down all endpoints for maintenance reasons only.The choice between ‘dial plan v.1’ and ‘dial plan v.2’ may not be obvious, but keep in mind that the second option allows more flexibility in hierarchically connected gatekeeper environments. Once chosen, it dynamically enables extra configuration sections.The option for DHCP environment may be used for authentication control, as it instructs the gatekeeper to identify endpoints by previously seen IP addresses and H.323 aliases (names) and authenticate them, based on this information.The last choice, merge predefined and on-line aliases upon registration is an interesting feature, because it allows the gatekeeper to apply extra aliases to well-known and identified endpoints, e.g., an endpoint may register with a name alias only, but the gatekeeper will attach an E.164
number to this endpoint as well.
Under the Settings tab, in the category Calls, be aware of the routing mode selection, as it alter the operation of the gatekeeper dramatically. Direct mode employs minimal communication between endpoints and gatekeeper (RAS messages only), while Call set-up routing mode forces call set-up messages to be routed through the gatekeeper as well (Q.931).The third mode forces all previous messages, as well as call control messages, to be routed through the gatekeeper and not directly between the endpoints.The setting of accept calls can be used for maintenance reasons to turn off all calling between endpoints.
Under the Settings tab, in the category Dialplan, assuming you have chosen dial plan version 2, you will be able to specify the stripping of zone prefixes from destination information of incoming calls.This feature may allow a more user-friendly dial plan, where in-zone endpoints use shorter dial numbers for dialling and out-of-zone endpoints use full-length dial numbers.
In passing, check the category Logs if you would like to enable logging for debugging purposes, and the category Billing to enable usage statistics and accounting. Category DNS will allow discovery of neighbouring gatekeepers through specially crafted DNS TXT records, but it seems to be compatible only with other RADVISION gatekeepers. Category LDAP will allow endpoint alias data and neighbour data to be retrieved from LDAP directory services, as well as LDAP-enabled endpoint authentication.
~ 4.5.2.3 Operation
Immediately after installation, the ECS may service endpoints, and you can verify this by making a couple of endpoints point to the gatekeeper for registration. As soon as the endpoints register, they appear at the Endpoints tab.You may proceed with calling between the two endpoints by dialling from one of the registered aliases (name or number) to the other.The ongoing call will appear in the Call Control tab. As an administrator of the gatekeeper, you may disconnect the call, or even un-register an endpoint from the respective tab sections. Logs of gatekeeper P.92
[IP Telephony Cookbook] / Setting Up Basic Services
operations may be started through the Settings tab, Logs subsection and can be inspected as text files from the
C:\Program Files\Radvision\ECS\Gatekeeper\Logs directory where they are maintained and rotated after they reach a certain size.
~ 4.5.2.4 Endpoint authentication
The ECS Gatekeeper implements H.235 authentication, but its use is limited to gatekeeper-to-gatekeeper and gatekeeper-to-gateway authentication, because of the very limited deployment of H.235 capable endpoints.The ECS implements a method of storing informational data for well-known endpoints (predefined endpoints).This feature allows for an IP address + alias identification method to be implemented, but such a solution imposes restrictions on endpoint mobility.
~ 4.5.2.5 Advanced features
The ECS Gatekeeper is able to support hierarchies of gatekeepers (child-parent relationships) in cases where many levels of prefixes must be supported by prefix stripping or prefix substitution.
For example, a country-level (parent) gatekeeper may need to know all dialled destinations by their 12-digit number, while an organisation-level (child) gatekeeper may be able to operate with just 4-digit numbers most of the time. In order for the child gatekeeper to support both long and short dial strings, it needs to implement prefix stripping.
The H.450 protocol provides the implementation framework for supporting, in H.323, a number of features common to conventional PBX systems.The ECS implements the H.450 protocol specifications, thus enabling many different types of forwarding: forward on busy, forward on no answer, forward on reject, etc.These features are supported only when the gatekeeper is in the full-routing mode (both call and control signal routing).
The ECS already has support for retrieving endpoint and neighbour data from LDAP, but it does so in a proprietary way. New developments in LDAP-enabled voice-over-IP services have given rise to H.350, the standardised protocol for storing and retrieving user settings and preferences regarding H.323 and SIP services. RADVISION is an active partner in the committee that developed the H.350 standard (previously known as H.LDAP or CommObject) and has made the commitment to implement it in the ECS Gatekeeper.
Until very recently, gatekeepers used to be single points of failure for voice-over-IP services, as endpoints in H.323 can only be registered with one gatekeeper.The ECS implements a special feature called ‘Alternate Gatekeeper’, where two identical ECS Gatekeepers on two different nodes can act in tandem, providing resilience in gatekeeper services transparently to the endpoints.This is achieved by constant exchange of information and status checking between a master and a slave gatekeeper, so that the second one can assume the role of the first in case of failure. In this case, some of the calls in progress may be disconnected, but at least redialling should be successful, without requiring the endpoints to register to a new gatekeeper.
P.93
[IP Telephony Cookbook] / Setting Up Basic Services
~ 4.5.3 Using an Open H.323 Gatekeeper - GNU Gatekeeper
The GNU GK is the most popular and active in the development of the open-source gatekeeper projects that stem from the OpenH323 project efforts. Being an open-source effort, it benefits from availability for many different operating systems and from flexibility in configuring a multitude of features and interfaces that are not usually available in commercial products, and all these with no licensing cost. At the same time, its initial installation is made problematic by lack of quality documentation and good versioning vs. feature-availability support, in contrast with a very active mailing list that users can seek help with.The GNU GK supports all three modes of routing: direct Q.931 routing and both Q.931 and H.245 routing. It has only basic inter-zone routing features, but authentication is very flexible, with very configurable RADIUS support and LDAP H.350 support in the works.
~ 4.5.3.1 Installation
Installing the GNU GK Gatekeeper is not a simple task, if you decide to compile the source of the gatekeeper and the two libraries it requires. However, this may be your only option, if support of MySQL and LDAP is required, since the provided precompiled binaries are lacking it.To avoid compilation of the code, please refer to the Pre-Built binaries downloads at the end of this section. In order to compile and build the GNU GK you will need both the PWLib libraries (ve






