1. SCOPE
Scope Analytics
Explore a set of digital technologies for sustainable development goals.
 Poverty control : Food security (zero hunger), Home security (disaster proof nano-housing schema), Garments and consumer goods security, Education security, Healthcare security (good health, well being, family planning, population control), Financial security (banking, financial services, tax, insurance, retirement planning, stock and derivative trading, economic growth), Energy security (clean and affordable renewable energy), Utilities security (clean water and sanitaion, gas, computing, internet, telecom), Communication security (internet, broadcast, satellite communication), Logistics security (travel, hospitalities, surface, water, rail, water, EVs and hybrid vehicles), Information, media and entertainment security;
Poverty control : Food security (zero hunger), Home security (disaster proof nano-housing schema), Garments and consumer goods security, Education security, Healthcare security (good health, well being, family planning, population control), Financial security (banking, financial services, tax, insurance, retirement planning, stock and derivative trading, economic growth), Energy security (clean and affordable renewable energy), Utilities security (clean water and sanitaion, gas, computing, internet, telecom), Communication security (internet, broadcast, satellite communication), Logistics security (travel, hospitalities, surface, water, rail, water, EVs and hybrid vehicles), Information, media and entertainment security;
 Social security (HR security, decent work, religious and cultural security, gender equality, child security, women’s empowerment, peace, justice, partnership, regulatory compliance, strong institutions)
Social security (HR security, decent work, religious and cultural security, gender equality, child security, women’s empowerment, peace, justice, partnership, regulatory compliance, strong institutions)
 Natural disaster security (climate change, flood, drought, storm, cyclone, earthquake, volcano, snowfall, rainfall, fire, bushfire, global warming, heat wave, epidemic, astronomical hazards) (attack of wild animals, insects, paste); artificial disaster security (defense, war, act of terrorism, bioterrorism)
Natural disaster security (climate change, flood, drought, storm, cyclone, earthquake, volcano, snowfall, rainfall, fire, bushfire, global warming, heat wave, epidemic, astronomical hazards) (attack of wild animals, insects, paste); artificial disaster security (defense, war, act of terrorism, bioterrorism)
 Responsible consumption and production (Enterprise Resource Planning, Supply Chain Management)
Responsible consumption and production (Enterprise Resource Planning, Supply Chain Management)
 Industry, innovation and infrastructure (smart cities, smart villages)
Industry, innovation and infrastructure (smart cities, smart villages)
 Life on land (environmental pollution, conservation of resources and forest, population control)
Life on land (environmental pollution, conservation of resources and forest, population control)
 Life below water (marine life, water pollution, global warming, oil leakage, nuclear explosion)
Life below water (marine life, water pollution, global warming, oil leakage, nuclear explosion)
Emerging innovative digital technologies:
 Communication technology: Satellite communication, mobile communication, broadcast communication, Sensor, global positioning system (GPS), Secure adaptive filter, RFID, IoT, IIoT, cloud computing, cloud streaming, edge computing;
Communication technology: Satellite communication, mobile communication, broadcast communication, Sensor, global positioning system (GPS), Secure adaptive filter, RFID, IoT, IIoT, cloud computing, cloud streaming, edge computing;
 Information technology: Information security intelligence analytics, adaptive security, dynamic data protection, cyber security, crash proof code, self healing smart grid; applied AI and machine learning : Deep learning, Robotics, Soft computing; Analytics – Deep analytics, Predictive analytics, Collaborative analytics; virtual and augmented reality, Digital twins, solar computing, Quantum computing, pervasive computing, wearable computing, Ray tracing.
Information technology: Information security intelligence analytics, adaptive security, dynamic data protection, cyber security, crash proof code, self healing smart grid; applied AI and machine learning : Deep learning, Robotics, Soft computing; Analytics – Deep analytics, Predictive analytics, Collaborative analytics; virtual and augmented reality, Digital twins, solar computing, Quantum computing, pervasive computing, wearable computing, Ray tracing.
Prof. Parker Smith and Prof. Pearson have started the session by exploring the scope of emerging digital technologies. With the significant advancement of information and communication technology, computing is perceived to be used as the next utility after water, electricity, gas and telecommunication. This session explores the classification of emerging digital technology through scope analytics. Digital technology can be classified into communication and information technologies. The scope of emerging communication technology is explored in terms of adaptive secure filters in adversarial environment, cloud computing, cloud streaming, cloud analytics, Internet of Things (IoT), Industrial IoT, Edge computing, next generation wireless and mobile communication (e.g.4G,5G,6G,7G,8G), broadcast and satellite communication, RFID and sensor networks. The scope of information technology is explored in terms of adaptive security, dynamic data protection, cyber security, crash proof code; applied AI and machine learning, soft computing, deep learning, robotics; deep analytics, predictive analytics, collaborative analytics, virtual and augmented reality, digital twins, solar computing, pervasive computing, wearable computing, secure multi-party quantum computing and ray tracing. This work also evaluates emerging digital technology in terms of system, structure, security, strategy, staff-resources and skill-style-support. Specifically, the technologies of adaptive security, dynamic data protection, solar computing, secure adaptive filters in adversarial environment and secure multi- party quantum computation have been evaluated in depth. The scope of deep analytics and deep learning have been outlined in sessions 1. Emerging digital technologies are useful in various application domains such as education, healthcare, information, media and entertainment, e-governance, manufacturing, retail, logistics, insurance, banking and financial services and development of smart cities and smart villages. Is it possible to apply digital technologies rationally and intelligently for the education of Dyslexia students by reducing their mental stress, information overloading and improving motivation, trust and commitment of the academic communities?
Figure 8.1 shows the classification of emerging digital technology. This is an interesting example of technology association. Level 1 shows the classification of digital technology. Level 2 shows the technology association of various types of communication technologies such as cloud computing, cloud streaming, cloud analytics, IoT and IIoT. It is possible to explore the scope of digital technology through Business Process Reengineering (BPR) approach (analyze as-is process and related IS, identify gaps and risks of as-is processes and IS and design to-be processes and system); top-down approach, critical success factor (CSF) analysis based on business objectives, constraints and requirements engineering, value chain analysis, bottom-up approach and inside-outside approach. One of the contributions of this session is scope analytics of emerging digital technology in figure 8.1. The scope analytics shows a set of information and communication technologies; among which the concepts of deep analytics, solar computing and adaptive security are unique.
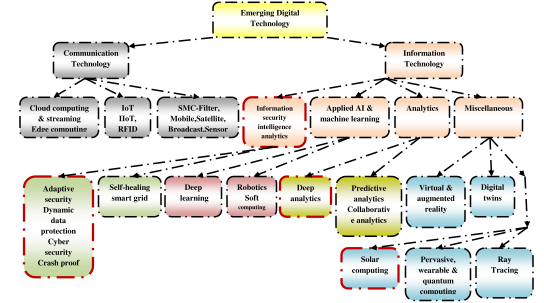
Figure 10.1 : Emerging Digital Technology Classification
Communication Technology : The scope of emerging communication technology may be explored in terms of cloud computing, cloud streaming, cloud analytics, Internet of Things (IoT), Industrial IoT and Edge computing next generation wireless and mobile communication, broadcast communication, satellite communication, RFID and sensor networks. The wireless technology is going through an evolution of a set of generations (1G 2G
2G 3G
3G 4G
4G 5G
5G G
G 7G
7G 8G). This session analyzes the technology of 5G, 6G, 7G, cloud computing, streaming and analytics and edge computing.
8G). This session analyzes the technology of 5G, 6G, 7G, cloud computing, streaming and analytics and edge computing.
This section performs SWOT analysis on the emerging 5G-6G-7G-8G wireless technologies. 5G is the fifth generation wireless technology for digital cellular networks with wide deployment in 2019. The frequency spectrum of 5G is classified as millimeter waves, mid band and low band. Low band uses a similar frequency range as 4G. 5G millimeter wave is the fastest having actual speeds 1–2 Gbit/s down. Frequencies are above 24 GHz reaching up to 72 GHz, above lower boundary of extremely high frequency band. 5G mid-band is the most widely deployed in over 20 networks; speed in a 100 MHz wide band is 100–400 Mbit/s down. 5G low-band offers similar capacity to advanced 4G; latencies between 25 -35 milliseconds. 5G networks are digital cellular networks in which the covered service area covered is divided into cells. Analog signals (e.g. sounds, images) are digitized by an analog to digital converter and transmitted as a stream of bits. All 5G wireless devices in a cell communicate by radio waves with a local antenna array and low power automated transceiver in the cell, The local antennas are connected with telephone network and Internet through a high bandwidth optical fiber or wireless backhaul connection. A mobile device crossing from one cell to another is automatically hands off seamlessly to the new cell.
6G (sixth generation) is the successor to 5G cellular technology; 6G networks are expected to use higher frequencies, higher capacity and much lower latency than 5G networks. 6G is a wireless technology that is beyond 5G. China has officially launched R&D works for 6G mobile networks. It would be about a decade before 6G comes along, NTTDoCoMo has presented the evolution of wireless technology from 3G in 2000s, 4G in 2010, 5G in 2020 and it is reasonable to expect 6G in 2030. It is not exactly known how fast 6G will be yet; it may be governed by the standards of International Telecommunication Union (ITU). If everything connects together using 5G, 6G with higher data speeds and lower latency makes instant device-to- device connection possible in various application such as autonomous cars, drones and smart cities, integration of our brains with computers and greatly improved touch control systems. 7G is the next generation communication technology. It is being adopted in Norway, China, Japan and other developed countries of the world. In Norway, Internet speed is fastest. Utilizing superior design and technology, 7G Network is expected to deliver millions of calls reliably every day, Let us exercise technology analysis of 5G. The air interface defined by 3GPP for 5G is known as New Radio (NR), and the specification is subdivided into two frequency bands - FR1 (below 6 GHz) and FR2 (mmWave) each with different capabilities. The next issue is frequency range 1 (< 6 GHz ); maximum channel bandwidth defined for FR1 is 100 MHz, the most widely band is around 3.5 GHz. For frequency range 2 (> 24 GHz), minimum channel bandwidth defined for FR2 is 50 MHz and the maximum is 400 MHz, From the perspective of performance analysis; 5G speed is expected to range from ~50Mbit/s to over 2Gbit/s even 100Gbit/s, 100x faster than 4G. The fastest 5G, known as mmWave, delivers speeds up to and over 2Gbit/s. The latency of 5G is 8 - 12 milliseconds. It is governed by International Telecommunication Union's IMT-2020 standards. Next, let us consider the deployment of 5G, nine companies sell 5G radio hardware and 5G systems for carriers - Altiostar, Cisco Systems, Datang Telecom, Ericsson, Huawei, Nokia, Qualcomm, Samsung and ZTE Large quantities of new radio spectrum (5G NR frequency bands) have been allocated to 5G. 5G devices include Samsung Galaxy S10 5G. The technology is getting adopted and diffused in Australia, Argentina, Bulgaria, Canada, China, Finland, Germany, India, Monaco, Netherlands, New Zealand, Norway, Pakistan, Philippines, Romania, Russian Federation, San Marino, South Africa, South Korea, Taiwan, Thailand, Uruguay, Vietnam, Qatar, Mexico, USA, Sweden and Panama.
Let us exercise scope and usage scenario analysis of 5G. ITU-R has defined three main uses for 5G as faster and reliable connection - Enhanced Mobile Broadband (eMBB), Ultra Reliable Low Latency Communications (URLLC), and Massive Machine Type Communications (mMTC). Only eMBB is deployed in 2019; URLLC and mMTC are several years away in most locations. eMBB uses 5G as a progression from 4G with faster connections, higher throughput, and more capacity; mMTC is expected to connect a large number of low power and low cost devices which have high scalability and increased battery lifetime in a wide area. 5G technology may connect some of 50 billion connected IoT devices. The other interesting uses are drones in disaster management through real-time data communication, smart cities for monitoring air and water quality through sensors, Vehicle-to-Vehicle (V2V) communication, public safety (e.g. Mission-critical push- to-talk (MCPTT) and mission-critical video and data), healthcare (Ultra-Reliable Low Latency Communications [URLLC] may improve telehealth, remote patient monitoring, remote surgery and wearable computing applications), fixed wireless connections, smart home (automated home equipped with lighting, heating, or other electronic devices that can be controlled remotely by smartphone or computer).
Most cars are expected to have a 4G or 5G cellular connection for many services. 5G Automotive Association have been promoting the C-V2X communication technology. It provides for communication between vehicles and communication between vehicles and infrastructures, leading to increase in autonomous self-driving cars and IOT (Internet of Things). The speed of 5G technology in upcoming self- driving cars may be vital in helping the capabilities of autonomous cars realize their full potential (Llanasas, 2019). Current 4G network doesn't possess the required speed needed to provide self-driving vehicles that could prevent catastrophic accidents or collision (Llanasas, 2019. 5G is expected to be the basic building block of anti collision system of next generation vehicles.
So far, we have discussed the strength of the emerging wireless technologies. But, there are various constraints such as interference, security, surveillance and health concerns. The spectrum used by remote sensing, weather and Earth observation satellites will be significant without effective controls. The technology has health concerns; the radiation could have adverse health effects. There are concerns of data security and privacy, surveillance concerns, threats of potential espionage of foreign users by 5G equipment vendors (e.g. Australia, UK and India have taken actions to restrict or eliminate the use of a vendor’s equipment in their 5G networks).
Cloud Computing, Cloud Streaming & Cloud Analytics : The technologies of cloud computing, cloud streaming and cloud analytics are closely associated. It is an interesting instance of technology association. With the significant advancement of information and communication technology, computing is perceived to be used as the next utility after water, electricity, gas and telecommunication. The concept can be extended to cloud computing and grid computing for a market oriented grid. Cloud computing uses the concept of utility computing, fog computing, grid computing and utility computing [1-24]. Utility computing is associated with a parallel and distributed system that enables the sharing, selection and aggregation of geographically distributed autonomous computational resources dynamically at runtime depending on their availability, capability, performance, cost and quality through web service. The computational resources include different types of sophisticated software applications such as data mining, scientific computing and image processing, data, CPU or processing power, servers, storage devices, scanners, UPS and network interfaces which can be shared through web service. The objective of utility computing is to provide computing power and storage capacity that can be used and reallocated for any application and billed on a pay- per-use basis. Utility computing consists of a virtualized pool of information systems and other IT resources that can be continually reallocated to meet changing business and service needs of the consumers. These resources can be located anywhere and managed internally or externally. The service provider tracks the usage of computational resources of the consumers and makes invoice based on predefined price setting and usage data. An efficient resource management system coordinates and monitors the complex operation.
Utility computing supports virtualization. Cloud computing is basically a distributed computing where dynamically scalable and virtualized resources are provided as a service over the internet to achieve cost saving, easy scalability and high availability. The services offered through cloud computing usually include Software-as-a-Service (SaaS), Infrastructure-as-a-service (IaaS), Platform-as-a- service (PaaS), data-Storage-as-a-Service (dSaaS) and database-as-a-service (DaaS). SaaS allows users to run applications remotely from the cloud. IaaS provides a set of computing resources as a service which includes virtualized computers with guaranteed processing power and reserved bandwidth for storage and Internet access. PaaS includes operating systems and required services for particular applications along with data security, backup and recovery, application hosting and scalable architecture. dSaaS provides data storage, data warehousing and data mining facilities. This is a cost effective, innovative IT infrastructure from which the consumers are able to access desired computational resources and from anywhere in the world on demand.
The key technologies that enable cloud computing are virtualization, web service, service oriented architecture, service flows and work flows. The trading in cloud computing depends on several technological issues such as high availability of service, business continuity, data lock-in, security and privacy of data, efficient data transfer, performance predictability, scalable storage, efficient bugs management in large distributed system, adaptive scaling of operation, innovative software licensing and reputation mechanisms. Strategic pricing considers all these QoS factors to define optimal price setting for cloud computing. In fact, an intelligent, innovative competitive pricing mechanism and highly secure QoS can make cloud computing an attractive IT business model as compared to traditional corporate computing model based on direct IT investment. Nowadays, pay-for-use or pay-as- you-go licensing are becoming popular in cloud computing market. Thus, the computing world is rapidly transforming towards developing information systems to be consumed as a service. Various service providers have started to build scalable data centers at various locations for hosting cloud computing.
The key players of the market of cloud computing are a set of service providers, service consumers and resource brokers. There are several challenges of trading in cloud computing : fair resource allocation protocols, optimal task scheduling, tendering, contract net protocols, auction, market clearing and negotiation mechanisms and pricing algorithms. The major threats are reduced contract duration, uncertainty, risk and variable duration of a portfolio of contracts, reduced switching costs and customer lock-in, uncertain customer demand, short life-cycle and high sunk cost. Cloud computing may require high development cost for instrumentation, provisioning and monitoring and start up costs in the face of uncertain demand. Cloud computing, web technologies and internet are expected to be extremely useful in higher education, R&D and efficient knowledge management (creation, storage, sharing, transfer and application of knowledge) in terms of innovative multi-dimensional education methodologies (e.g. projects, case discussion, consulting assignments), sources of high quality online education materials, provision of sophisticated softwares for data analysis and data visualization techniques (e.g. Youtube, online test and evaluation).
Cloud streaming: Cloud based mobile video streaming techniques are used in online gaming, videoconferencing, augmented reality and watching videos (e.g. movies, music) through smart phones (e.g. mobile visual search smart phones, Tablets). The scope of cloud streaming may be explored through a set of technologies such as mobile multimedia, wireless network, cloud computing, video streaming and video sharing technologies. In mobile communication network, video sharing is done through wireless link (e.g. 3G, 4G, Wi-Fi); on-demand, dynamic and easily accessible video data are provided through streaming protocols in cloud environment. Mobile devices have various constraints such as computation, memory and energy capacity. Mobile cloud computing paradigm is used in transmission of real-time data (e.g. audio, video, text, GPS) transmission; it is bridging the gap between the demand of the service consumers and capability of various mobile devices in terms of data storage and processing of video and audio data.
Edge Computing : Edge computing is a distributed computing paradigm which enables computation and data storage closer to the location where it is needed; improves response times and saves bandwidth. It supports data processing at or near the source of data generation. IoT connected devices interact with remote sensors and may generate data. Edge computing is a perfect fit for IoT - data is processed near the point of origin, the latency between devices and data processing layer is reduced and enable faster response and correctness in decision making. The increase of IoT devices at the edge of the communication network may generate massive amount of data to be computed to data centers and may result the constraints of network bandwidth. Data centers may not guarantee acceptable transfer rates and response times. The devices at the edge constantly consume data from the cloud and demand the development of content delivery networks to decentralize data and service provisioning.
The basic objective of edge computing is to move the computation away from data centers towards the edge of the network through a set of smart objects, smart phones and network gateways to perform various tasks such as service delivery, storage and IoT management and ensure improved response time and transfer rate. But there are various news issues in distributed computation such as security and privacy of data, scalability, resiliency, reliability and consistency of system performance. The data should be encrypted for the protection from hacking but it may result increased cost of computation and communication. Scalability in a distributed network should consider different constraints of system performance, energy constraints, dynamic data management and heterogeneity of IoT devices. The system should be protected in terms of liveness, fast fault detection and recovery and stability of the topology of entire distributed system. It is interesting to explore the applications of edge computing in cloud streaming, smart cities and villages and home automation systems.
Internet of Things (IoT), IIoT, RFID, Sensors : Internet of Things (IoT) is a system of interrelated computing devices, mechanical, electrical, electronics and biomedical machines, objects, animals and people with unique identifiers (UIDs) with the ability to transfer data over a network without human-to-human or human-to-computer interaction. IoT has been evolving due to the convergence of multiple technologies such as real-time analytics, machine learning, sensors, embedded systems, wireless sensor networks, control systems, automation (home and building automation), smart home (e.g. lighting fixtures, thermostats, home security systems, cameras), smart phones and smart speakers. But, there are constraints of information security and privacy. The technology has been evolving through R&D on RFID, sensor networks and Industrial IoT (IIoT). The technologies of RFID and sensors are applicable to real- time supply chain management, tracking and inventory management in logistics and retail sectors. Sensor networks can be used for real-time monitoring in defense sector and intelligent military applications. It is also interesting to deploy intelligent sensor networks (e.g. webcams, CCTVs) for real-time surveillance and development of smart cities and smart villages and intelligent transportation networks.
Information technology
Analytics: Analytics is one of the most promising digital technologies today. The technology is going through an evolution of various phases such as shallow, predictive, collaborative, big and deep analytics. Deep analytics is an intelligent, complex, hybrid, multi-phased and multi-dimensional data analysis system. The basic steps of computation are data sourcing, data filtering / preprocessing, data ensembling, data analysis and knowledge discovery from data. The authorized data






