c. Lead Company Movement. The lead company or advance guard on an axis moves using traveling overwatch or bounding overwatch, depending on the situation. It normally is assigned an axis of advance or a zone of action and a march objective on which to orient its movement. Phase lines and checkpoints also can help control movement.
(1) The company commander selects the movement technique and formation based on the likelihood of enemy contact and the speed of movement desired by the battalion commander. Bounding overwatch provides the best security, but traveling overwatch is faster. If the company uses traveling overwatch, the lead platoon may use bounding overwatch for added security.
(2) The company commander must retain the freedom to maneuver his platoons and weapons. He analyzes the terrain, anticipates where he might make contact, and plans fires on those locations. He should avoid terrain that restricts maneuver, such as draws, ravines, narrow trails, and steep slopes.
d. Other Companies. A company not in the lead uses traveling or traveling overwatch. It must be ready to fire or maneuver in support of the lead company, or to assume the lead company's mission.
4-28
FM 3-21.11
e. Contact. Once the company makes contact with the enemy, the company commander maintains that contact until ordered to do otherwise by the battalion commander. The following actions must take place at once:
(1) When there is an unexpected contact, the platoon in contact returns fire at once and takes cover. If the enemy is unaware, the platoon making contact reports and deploys to prevent detection. The maneuver to a position of advantage by this platoon (or other units) should maintain the element of surprise until the company completes preparation for the hasty attack. If detected, or once the company commander decides to initiate the hasty attack, the platoon leader attempts to fight through, destroying the enemy with the resources that are immediately available. His FIST should begin calling for fire. The platoon leader then reports to the company commander and develops the situation. The overwatch element immediately fires at the enemy position. Trail platoons that are not able to fire take cover and wait for orders.
(2) The squad or platoon that initially received direct fire immediately executes the attack drill (FM 3-21.9 [FM7-5]). The intent is to use aggressive small-unit actions to seize the initiative rapidly and at the lowest echelon possible. The unit in contact attempts to achieve fire superiority to fix or suppress the enemy with the resources that are immediately available. The unit then executes a flank attack directed against an identified enemy weakness. If this is not possible, the unit develops the situation to identify the enemy's flanks, any covered and concealed routes around the enemy position, possible supporting positions (both friendly and enemy), and any protective obstacles that the enemy has constructed. It then reports this information to the company commander.
(3) Upon receipt of this information, the company commander determines the proper action to take. The XO reports the situation to battalion. The company commander may conduct, or direct his units to conduct, additional reconnaissance. The company FSO
requests and coordinates indirect fires to support the company's maneuver. Possible actions include the following.
(a) Conduct a Hasty Attack. If the company commander feels he can defeat the enemy force and an attack supports the battalion commander's concept, he conducts a hasty attack immediately, before the enemy can react.
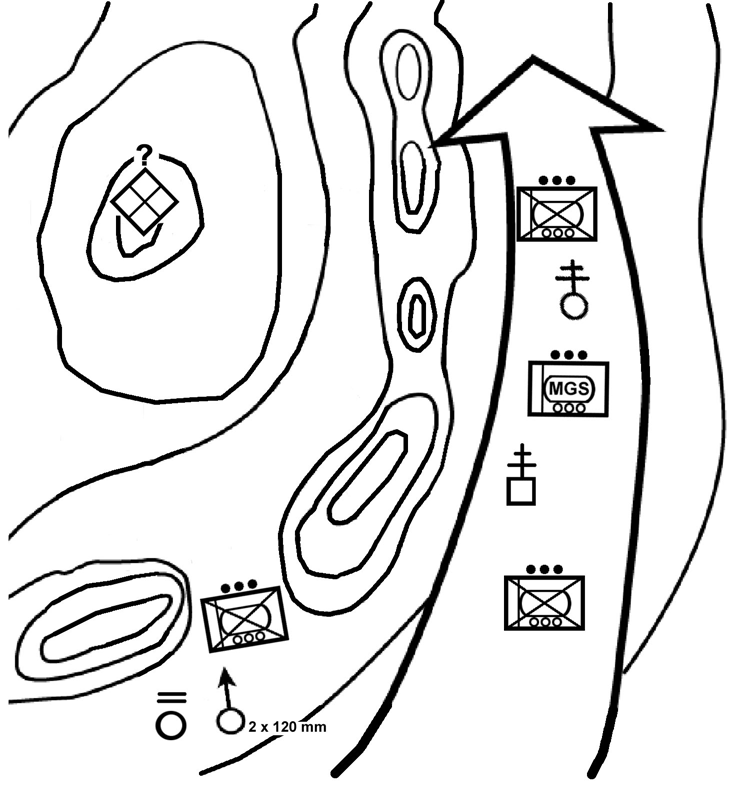
(b) Bypass the Enemy. The company commander, with battalion permission, may bypass an enemy force. He may bypass the enemy with one platoon at a time or with the entire company at once (Figure 4-9, page 4-30).
4-29
FM 3-21.11
Figure 4-9. Bypass.
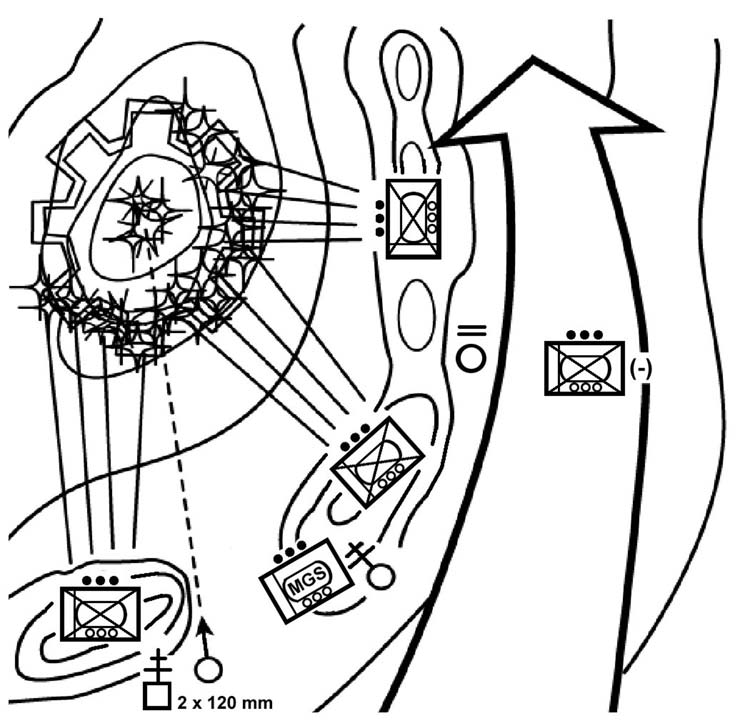
(c) Fix or Suppress the Enemy. When the enemy cannot be bypassed and a hasty attack by the company would be too costly, the battalion normally directs the company to fix or suppress the enemy (Figure 4-10). This ensures that the enemy does not have the freedom to fire or maneuver against the main body of the battalion while the battalion moves to attack the enemy. The company commander supports the battalion commander's planning by reconnoitering to identify the enemy's disposition, strengths, and weaknesses. The company identifies covered and concealed routes, good support positions, and enemy obstacles and reports these to battalion.
4-30
FM 3-21.11
Figure 4-10. Fix or suppress.
(d) Establish a Hasty Defense. Although this action tends to give the initiative to the enemy force, it might provide a needed advantage. This might be required in a meeting engagement with a superior force. The company may establish a hasty defense to protect itself while the remainder of the battalion maneuvers against the enemy.
(e) Disengage. This action is not preferred unless disengaging is the only way to ensure preservation of the force. Use of indirect fires and bounding and overwatch elements is essential in disengaging from a superior force. The company may disengage while another unit maintains contact, or the company may disengage by moving back through the battalion to draw the enemy into an ambush.
4-26. CONSIDERATIONS
The battalion may direct the company's technique (search-and-attack or approach-march).
If not, the SBCT infantry rifle company commander considers his mission and the battalion concept as he conducts his estimate to select the best technique. Normally, when operating as part of a battalion movement to contact, the company employs the same technique as the battalion. The commander must consider the mounted capabilities of his company during both techniques. The following considerations may also assist the commander in developing his concept.
4-31
FM 3-21.11
a. Time Available. The time available for planning, coordinating, and rehearsing may affect the decision. The approach-march technique generally requires much less time for preparation. The company may require only a brief FRAGO assigning the movement formation or technique and some simple graphic control measures to begin movement.
The search-and-attack technique may require more preparation time because the platoons and squads have more planning responsibilities (such as patrol base, linkups, and casualty evacuations).
b. Speed of Movement. The speed the company must move is a major factor. With either technique, the faster the company moves, the less effective its R&S efforts are.
Thus, it becomes more likely that the enemy will initiate fires at the time and place he selects. The approach-march technique is normally more effective for quickly reacting to enemy contacts.
c. Enemy. The company commander considers the clarity of the enemy situation. If the enemy situation is vague then a movement to contact is required; however the SBCT
company commander should have some information via analog activities or digital information. Knowing where the enemy will probably locate and in what strength is key to developing a concept. The company commander considers the enemy's probable locations and strength when planning the company's movement and security needs, and he analyzes the risks for each technique. The company commander also considers the expected enemy action upon contact. If he expects the enemy to fight, then the approach march may be the more effective technique. If the enemy will attempt to avoid detection or quickly disengage, the search-and-attack technique may be the better method.
d. Security. Preparation time, required movement speed, and the enemy situation have a direct impact on the company's security requirements. The company commander also considers the terrain, the adjacent units, the available combat support, and the present status of his unit to determine how to provide security for his company.
Successful movements to contact depend on locating the enemy without being detected.
This provides the company commander the initiative to develop the situation by fully coordinating and supporting the attack with all available resources.
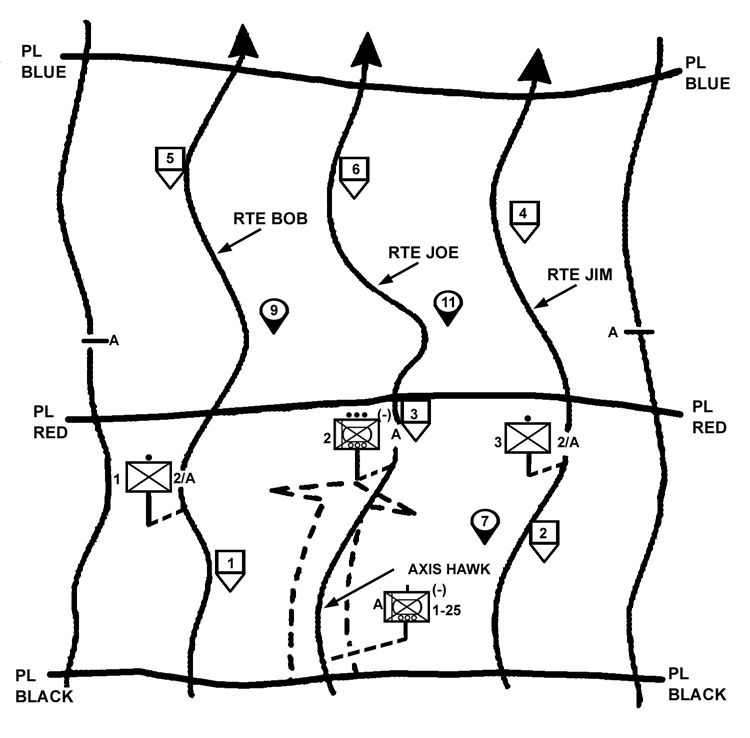
e. Combined Technique. An effective option may be to combine the techniques by having the lead platoon use the search-and-attack technique while the rest of the unit uses the approach-march technique. The lead platoon is assigned reconnaissance missions to find the enemy. In the example illustrated in Figure 4-11, the company commander assigns route reconnaissance tasks to the 2d Platoon. He assigns checkpoints and named areas of interest (NAIs) to focus the subordinate elements on specific locations. He can also use phase lines (PLs) to control the lead platoon by directing that PLs be crossed on order. The company main body follows the reconnaissance at a distance that allows it to rapidly maneuver based on reports from the lead platoon. The formation and movement techniques for the main body vary but generally apply the fundamentals for the approach-march technique.
4-32
FM 3-21.11
Figure 4-11. Combined techniques.
4-27. EXPLOITATION
A company normally takes part in exploitations as part of a larger force; however, the company should exploit tactical success at the local level within the higher commanders'
concept of the operation.
4-28. PURSUIT
The objective of the pursuit phase of an operation is the total destruction of the enemy force. The SBCT infantry rifle company may take part in a pursuit as part of a larger force or, because of its organic transportation, may act as the pursuit force that can close with and destroy the remnants of the enemy force.
Section VII. SPECIAL PURPOSE ATTACKS
The company conducts a special purpose attack at the direction of the battalion commander. The commander bases his decision on the factors of METT-TC. Special purpose attacks are subordinate forms of an attack and they include--
• Ambush.
• Raid.
• Counterattack.
4-33
FM 3-21.11
• Spoiling attack.
• Feint.
• Demonstration
As forms of the attack, they share many of the same planning, preparation, and execution considerations of the offense. Feints and demonstrations are also associated with military deception operations.
4-29. AMBUSH
An ambush is a surprise attack, from concealed positions, on a moving or temporarily halted enemy. It may take the form of an assault to close with and destroy the enemy, or it may be an attack by fire only, executed from concealed positions. An ambush does not require that ground be seized or held. Infantry forces normally conduct ambushes. (For a more detailed discussion of ambushes, refer to FM 7-10.)
a. Purposes. Ambushes are generally executed to reduce the enemy force’s overall combat effectiveness. Destruction is the primary reason for conducting an ambush. Other reasons to conduct ambushes are to harass the enemy, capture the enemy, and destroy or capture enemy equipment and supplies.
b.
Operational Considerations. The execution of an ambush is offensive in nature.
The company, however, may be directed to conduct an ambush in a wide variety of situations. For example, it may stage the ambush during offensive or defensive operations, as part of SBCT battalion rear area operations, or during retrograde operations. The commander must consider the capabilities of his company in the mounted and dismounted role. Operational security is critical to the success of an ambush and is a major reason the operation normally is conducted only by infantry forces. The company must take all necessary precautions to ensure that it is not detected during movement to or preparation of the ambush site. The company must also have a secure route of withdrawal following the ambush.
c. Actions. An ambush normally consists of the following actions:
• Tactical movement to the ORP.
• Reconnaissance of the ambush site.
• Establishment of ambush site security.
• Preparation of the ambush site.
• Execution of the ambush.
• Withdrawal.
d. Task Organization. The company normally is task-organized into assault, support, and security forces for the execution of the ambush.
(1) Support Force. The support force fixes the enemy force and prevents it from moving out of the kill zone, allowing the assault force to conduct the ambush. The support force generally uses direct fires in this role, but it also may be responsible for calling for indirect fires to further fix the ambushed force.
(2) Assault Force. The assault force executes the ambush. It may employ an attack by fire, an assault, or a combination of those techniques to destroy the ambushed force.
(3) Security Force. The security force provides protection and early warning to the ambush patrol and secures the ORP. It isolates the ambush area both to prevent the ambushed enemy force from moving out of the ambush site and to keep enemy rescue 4-34
FM 3-21.11
elements from reaching the site. The security force also may be responsible for securing the company’s withdrawal route.
e.
Types of Ambushes. Once the company receives an order to conduct an ambush, the commander must determine which of the two types of ambush operations is best suited to the situation and the capabilities of his company. In a point ambush, the patrol deploys to attack an enemy force in a single kill zone. In an area ambush, the patrol is deployed to conduct several related point ambushes throughout an ambush area.
4-30. RAID
A raid is a limited-objective form of attack entailing swift penetration of hostile terrain. A raid operation always ends with a planned withdrawal to a friendly location upon the completion of the assigned mission. It is not intended to hold territory. The company can conduct an independent point raid or it can participate in a battalion area raid. A point raid attacks the enemy force in a single kill zone; an area raid encompasses several related point raids or other related operations. It is unlikely that a company would conduct an area raid independently.
a. Company Role. The company conducts raids to accomplish a number of missions, including the following:
• Capture prisoners.
• Capture or destroy specific command and control locations.
• Destroy logistical areas.
• Obtain information concerning enemy locations, dispositions, strength, intentions, or methods of operation.
• Confuse the enemy or disrupt his plans.
b. Task Organization. Task organization of a raiding force is based on the purpose of the operation. It normally consists of the following elements:
• Support force (with the task of support by fire).
• Assault force (with the task of destroy).
• Breach force (if required).
c. Conduct of the Raid. The main differences between a raid and other attack forms are the limited objectives of the raid and the associated withdrawal following completion.
Raids may be conducted in daylight or darkness, within or beyond supporting distance of the parent unit. When the area to be raided is beyond supporting distance of friendly lines, the raiding party operates as a separate force. An objective, usually very specific in nature, normally is assigned to orient the raiding unit. During the withdrawal, the attacking force should use a route or axis different from that used to conduct the raid itself.
4-31. SPOILING
ATTACK
A spoiling attack is a limited-objective attack to delay, disrupt, or destroy the enemy's capability to attack. SBCT infantry commanders mount spoiling attacks from defensive postures to disrupt expected enemy attacks. A spoiling attack attempts to strike the enemy while he is most vulnerable--during his preparations for attack in assembly areas and attack positions or while he is on the move prior to crossing his line of departure. In most respects, commanders conduct spoiling attacks like any other attack. They may be either
4-35
FM 3-21.11
hasty (when time is short) or deliberate (when the command has adequate forewarning).
When the situation permits, commanders exploit a spoiling attack like any other attack.
4-32. COUNTERATTACK
A counterattack is an attack by defensive forces to regain the initiative or to deny the enemy success with his attack. Commanders conduct counterattacks either with a reserve or with lightly committed forward elements. They counterattack after the enemy launches his attack, reveals his main effort, or creates an assailable flank. SBCT infantry commanders conduct counterattacks much like other attacks but synchronizing them within the overall defensive effort requires careful timing.
a. Commitment of Combat Power. Counterattacks afford the defender the opportunity to create favorable conditions for the commitment of combat power. If it can fix the enemy, then the company can rehearse counterattacks, control their timing, and prepare the ground to be traversed. Counterattacks are most useful when they are anticipated, planned, and executed in coordination with other defending, delaying, or attacking forces and in conjunction with a higher commander's plan.
b. Exploit Success. As in spoiling attacks, commanders prepare to seize the opportunity to exploit success by the entire force. However, counterattacks may be limited to movement to better terrain in order to bring fires on the enemy. Given the same forces on both sides, counterattacks can achieve greater effects than other attacks because the defender can create more favorable conditions through rehearsal and control of the timing.
4-33. FEINT
The feint is in many ways identical to other forms of the attack. Its purpose is to cause the enemy to react in a particular way, such as by repositioning forces, committing its reserve, or shifting fires. The key difference between the feint and other attack forms is that it is much more limited in scope and has an extremely specific objective. The scale of the operation, however, usually is apparent only to the controlling headquarters. For the element actually conducting the feint, such as an SBCT infantry company or battalion, execution is just as rapid and violent as in a full-scale attack.
a. Company Role. The company normally participates in a feint as part of a larger element. Among the planning considerations for the company commander are the following:
• The higher commander’s intent regarding force preservation.
• Disengagement criteria and plans.
• Assignment of limited depth and attainable objectives.
• Clear follow-on orders that ensure the feinting force is prepared to exploit the success of the main attack if necessary.
b.
Making Feints Believable. Feints are successful only if the enemy believes that a full-scale attack operation is underway. To be believable, they must be conducted with the same violence and the same level of precision as any attack. The controlling headquarters must issue a clear task and purpose to the unit conducting the feint. This should include identification of the specific enemy action the feint is supposed to trigger (or deny), such as forcing the commitment of an enemy reserve force or preventing an 4-36
FM 3-21.11
enemy element from repositioning against the main effort attack. Feints are most effective under the following conditions:
• When they reinforce the enemy’s expectations.
• When the attack appears to present a definite threat to the enemy.
• When the enemy has a large reserve that he has consistently committed early in the battle.
• When the attacker has several feasible COAs, any of which the enemy could mistake for the main effort.
4-34. DEMONSTRATION
The demonstration is an attack whose purpose is to deceive the enemy about the location of the main attack. This purpose is similar to that of a feint, but the friendly force does not make contact with the enemy. For example, the SBCT infantry company’s role might entail establishing an attack-by-fire position beyond the enemy’s direct fire engagement range; the purpose would be to cause the enemy to commit a specific element simply by virtue of the positioning of the demonstration force. In preparing to participate in a demonstration as part of a larger force, the company commander should keep in mind the following planning considerations.
a. Limit of Advance. The limit of advance must be carefully planned so the enemy can "see" the demonstration force but cannot effectively engage it with direct fires. The force must also take any other security measures necessary to prevent engagement by the enemy.
b. Contingency Plans. The demonstration force must make contingency plans so it can respond effectively to enemy direct or indirect fires while avoiding decisive engagement.
c.
Follow-on Orders. Clear, specific follow-on orders must ensure that the demonstration force is prepared to exploit the success of the main attack, if necessary.
Section VIII. ATTACK TECHNIQUES
The assault on an enemy strongpoint and a limited visibility attack are the two most demanding attacks an SBCT company conducts. The fundamentals and techniques discussed in this section will assist the SBCT infantry commander in planning, preparing, and conducting all attacks.
4-35. ASSAULT OF A STRONGPOINT
The most difficult objective for a light infantry force is to seize or clear an enemy strongpoint complete with obstacles and fortifications. The commander employs techniques that avoid attacking the enemy's main strength. Instead, he tries to identify and attack a weakness in the defense. The SBCT infantry commander deceives the enemy as to the point of the main attack; he uses surprise to take advantage of his initiative in determining the time and place for the attack. He attempts to strike the enemy on exposed flanks or the rear. A deliberate attack of a strongpoint is usually conducted in the following steps:
• Reconnoiter the objective and develop the concept.
• Move to the objective.
• Isolate the objective and the selected breach site.
4-37
FM 3-21.11
• Attack to seize a foothold.
• Exploit the penetration and clear the objective.
a. Reconnoiter and Develop the Concept. The commander conducts reconnaissance of the objective himself or has someone else do it. The reconnaissance should identify the positions on the objective (crew-served weapons, C2 locations, and vehicles), the level of preparation, the gaps in the defense, and other potential weaknesses. The SBCT infantry commander may conduct reconnaissance of the objective to determine any changes from previous information.
(1) The reconnaissance may be done many different ways. An effective technique is to task-organize a reconnaissance patrol with leaders from the assault, support, and breach elements. There should be sufficient personnel to establish surveillance on the objective and to secure the ORP. The reconnaissance patrol either returns to the company's location or meets the company at a designated linkup point and guides it into the ORP. At times, the scout platoon or other battalion assets may be tasked to conduct reconnaissance in support of the company's mission.
(2) After the commander develops his concept, he often task-organizes his unit into a breach element, a support element, an assault element, and possibly a reserve. The reserve is normally under his control and is positioned where it can best exploit the success of the attack or increase combat power as necessary. The reserve should not be so close that it loses flexibility during the assault. The reserve leader must know where he will locate throughout the attack.
(a) The breach force is usually formed around an infantry unit. Engineers, if available, are also part of the breaching element. Any mechanical or explosive breaching assets are attached to this element. The breach force makes the initial breach and passes the assault element through. It may have to organize its own assault element (to secure the breach), support element (to provide close-in suppression), and breach element (to actually breach the obstacles).
(b) The support element is organized to provide supporting (indirect or direct) fires initially to the breach element, then to the assault element. The support element may consist of any combination of infantry squads, the 120-mm/60-mm mortar section, the machine-gun teams, M203 gunners, the MGS platoon, or the ICVs. Their primary responsibilities are to suppress enemy forces that may engage the breach element and to isolate the objective from enemy reinforcement or escape.
(3) The assault element is usually one or two infantry platoons, depending on the enemy situation (number of personnel, level of preparation, and complexity of fortifications) and the size and composition of the breach and support elements. Often, a small assault element supported by a large volume of accurate suppressive fires is effective in clearing the objective. The assault element may also need to breach enemy protective obstacles on the objective.
(4) The commander determines the best task organization for the entire mission. It should be simple and maintain unit integrity whenever possible. At times, the company moves to the ORP task-organized as usual (no cross attachments), changes task organization in the ORP for the conduct of the assault,






