CHAPTER 4
Anatomy of a key
A key pair consists of a public key and a private key. The public key is the key that you dis tribute to others, and the private key is the key that you keep with yourself. Keys are basically a stream of text that contains all the necessary information that identify them. Here we provide text and graphical representations of keys. Keys are always stored in key rings.
-
Keys can realize up to 4 different operations:
In this book we cover the first two operations, which are discussed with more details in their respective chapters.
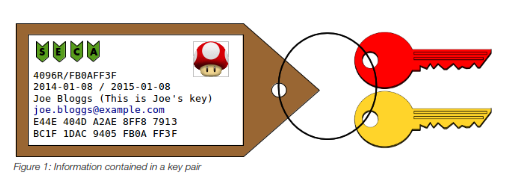
The example below illustrates the basic information contained in a key pair. The private key is the red one, and the public key is the yellow one.
4.1 – A key pair
Here you can see a key pair containing a private key and a public key.
4.2 – Parts of a key
Below is explained what means each part of the key.
These letters are called 'flags' and they represent the operations the key is able to realize, as described in the beginning of the chapter. In our example the key can realize all the four operations, but not all keys can realize them all.
4096 is the length of the key in bits, which normally varies between 1024 and 4096.
R is the type of the key, in this case RSA. FB0AFF3F is the key identifier (ID).
Those are the creation date and expiry date (if exists) respectively. They are presented in the format YYYYMMDD.
-
Joe Bloggs (This is Joe's key) joe.bloggs@example.com
The key owner's full name, comment and email address.
-
E44E 404D A2AE 8FF8 7913 BC1F 1DAC 9405 FB0A FF3F
This is the key fingerprint. This is a unique hexadecimal number with 40 digits and every key has one. Every time you receive a key you have to confirm it with the key's owner, because it is the only guarantee you have that the key is in fact of the person who claims to be its owner, and was not twisted or modified along the way.
It is possible to add an image to your key, but this is not recommended for three reasons: it makes your key heavier, some programs have problems to deal with them, and it presents a false sense of security.
All these attributes are present in keys, so you can check them every time you obtain a key, as well as others can check them with your key.
4.3 – Keys in a keyring (graphical visualization)
Keys are always stored in key rings., which are managed by GnuPG. You can easily backup or export your whole keyring to use it in another machine that you own. Below there are 3 keys from different owners in a keyring, which were obtained from the owners' respective websites. Since the keys are not ours, only their public part are available.
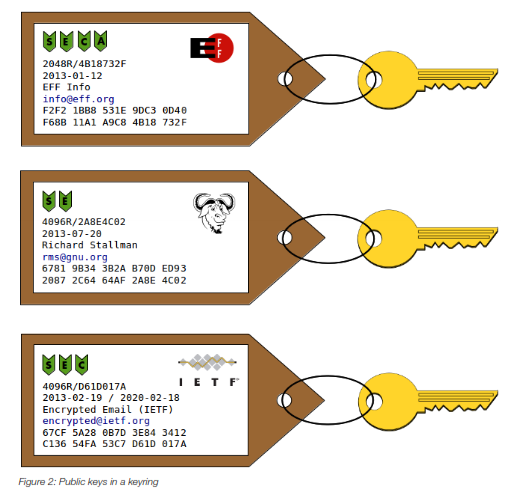
This is how keys would look graphically in our example. All these keys do not have image, they were added only to make comprehension easier.
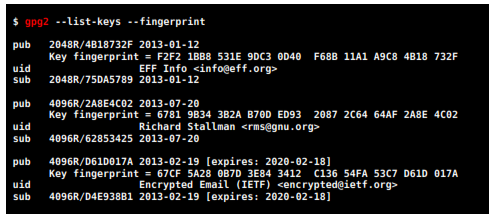
4.4 – Keys in a keyring (text visualization)
Here are the same keys displayed in command line:
4.5 – How a key looks like
A key is just a file that contains all the attributes mentioned above. Below is an example of how a key looks like in ASCIIarmored format:

This is how a key looks like in ASCIIarmored format. If you open any key with a text editor you will see a similar result (unless the key is in binary format).
The term ASCII, when used throughout this guide, simply means text or in text format (actually it's more complex than that, you can check this Wikipedia article for more information: https://en.wikipedia.org/wiki/ASCII).
The key in this example is the same key used in section 7.1. If you copy and save it in a text file, you can import it to your keyring as described in chapters 12, 15 and 16. You can also check that the fingerprint is the same. However our example key does not have image, the image was only added to the figure for illustrative purposes.
4.6 – Conclusion
Keys are the basic component of asymmetric. cryptography, also know as public key cryptography. They store information about the key's owner that allows users to identify the owner, as well as other technical aspects regarding its security and capabilities.
Keys are editable, so some of their attributes can be further changed after creation. To be used they must be stored in key rings., which GnuPG creates automatically. They can also be transported to other machines or exported as backup copies.







