CHAPTER 3
How cryptography works?
The basic idea is to shuffle the original information with the secret code, resulting in the encrypted information. The power, strength and security of encryption lies exactly in how these parts are shuffled. The diagram below illustrates this process:
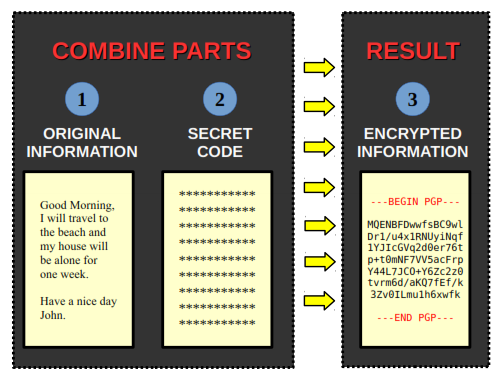
That's it, your message is now encrypted and ready to be sent. For the person be able to decrypt it he will need to posses the secret code, which will be covered in the next section.
Now let's see the two main types of encryption methods: symmetric and asymmetric.
3.1 Symmetric Cryptography
Symmetric cryptography is the simplest of all and you probably have used it many times.
The word symmetric means “equal”, which means that to encode and decode a file the password is the same.
The most basic example is when you save a file with password. It doesn't matter if you save it for yourself or for others, the password to open it is always the same.
Symmetric cryptography is faster, simpler and more economic than asymmetric cryptography because it does less mathematical calculations, which in turn uses less machine resources (e.g.: electricity). It is also more compatible with other systems and it is very secure.
However its main problem lies not in strength, but in the transmission of the secret code.
When you send an encrypted file to another person you also have to send the password so the person can open it, and symmetric cryptography does not provide any means to send the password in a secure way.
You cannot send the encrypted file through email and the password wrote in the message body because that is too obvious and risky. You could send the password by phone, SMS or letter, but these methods are also insecure and could be easily intercepted. You could deliver the password personally, but this is very inconvenient and sometimes inviable.
So how do you do it? As you see the major problem of symmetric cryptography is to transmit the password in a convenient and secure way. If the password is compromised, anyone can access the file and even modify it.
Another disadvantage is that if you use a password, you automatically know it, and others could coerce you to reveal it, as in the customs, through a law order or under interrogation.
It is because of these reasons that symmetric cryptography is recommended for local files that stay stored locally (such as backup copies) or files to be transfered through physical media.
3.2 Asymmetric or public key cryptography
Asymmetric cryptography, also known as public key cryptography, was created to solve the problem of transmitting the secret code that symmetric cryptography poses.
Simply speaking, in public key cryptography instead of using a single code equal for all, it is used a code with two parts: your part and the other person's part. This way only her will be able to decrypt the information you send to her. If someone intercept this information along the way he will not be able to do anything because he does not have the necessary part of the code.
These “parts” are actually called keys, which are public and private. The example below illustrates this more easily:
Let's imagine that John wants to send an encrypted file to Mary using public key cryptography. Here are the steps they have to follow to accomplish this:
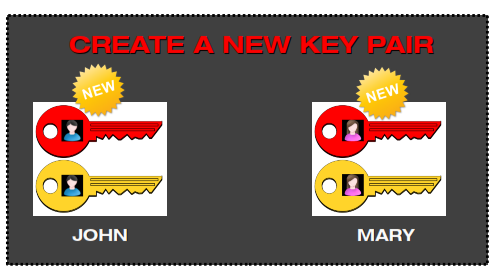
1 – Create a key pair
First each one of them creates a key pair containing a private key (red) and a public key (yellow). This step is covered with details on chapter 6.
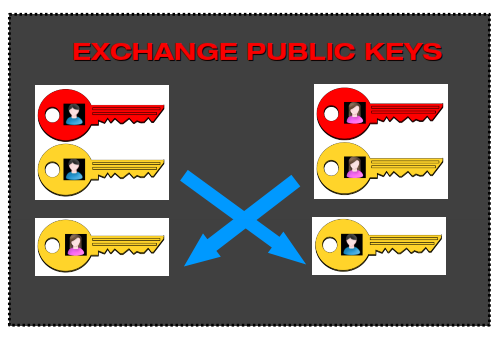
2 – Exchange public keys
Each one of them sends a copy of their public key to the other, since the purpose of the public key is to give it to others. There are several ways to do it, the most common is to send it via email (discussed in chapter 8.4), but it is also possible to publish the key in a key server, in a personal website, or deliver it through physical media (such as a CDROM).
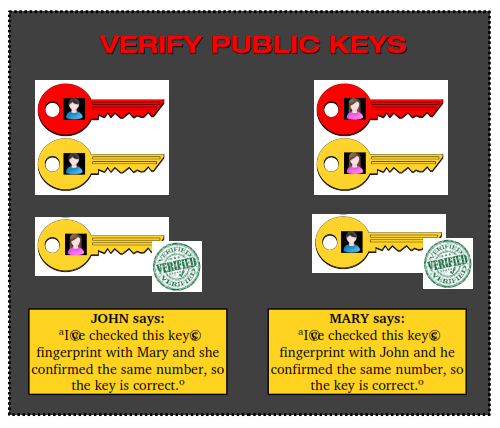
3 – Verify the received key
Now each one of them possesses their own key pair and a copy of the other person's public key. They must verify the other's public key to confirm they received it correctly. This is the most important step because it ensures that the key they received was not twisted or modified along the way.
Verifying is a simple process: every key comes with a number (a digital fingerprint) and all they have to do is to check this number with the sender to ensure it is correct.
4 – Encrypt a file and send it
To encrypt a file to another person John just chooses the file he wants to send and the file will be encrypted exclusively to that person.
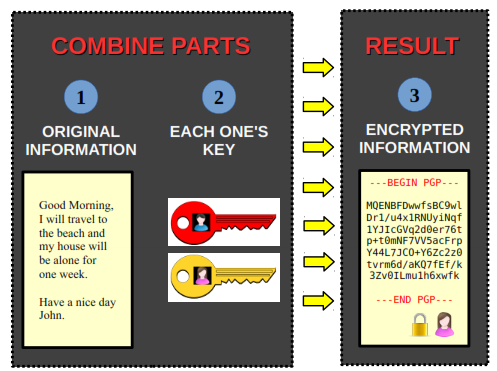
The original message is combined with the sender's private key (John's) and the receiver's public key (Mary's), resulting in an encrypted file that only the receiver (Mary) can decrypt.
Now the resulting file can be sent to Mary through any means (such as email) because only her can decrypt it, because to do it she needs her private key and the sender's public key.








