CHAPTER 11
Signing and Verifying Files
A digital signature has two purposes: to ensure the authenticity of the sender (and not someone impersonating him/her), and to ensure that the information is original and was not twisted along the way. In a way it is similar to a physical signature in a cheque or in a contract, but despite marking the sender's identity, it also marks the time the information was signed, thus offering double security.
As a good practice you should sign files every time you encrypt them.
11.1 – Making signatures
There are three ways to make signature with GnuPG: generating an unreadable signed file, generating a readable signature, and generating a detached signature. Each one has different uses and purposes:
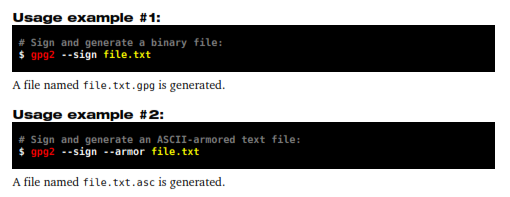
11.1.1 – Binary signature (unreadable)
This method generates a new file in binary format containing the original file (now compressed) plus the signature. This method is recommended to be used with nontext files.
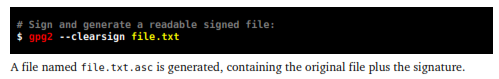
11.1.2 – Clear signature
This method generates a new file in text format containing the original file plus the clear signature in the end. This method is recommended to be used with email messages, online forum posts and discussion lists, since it does not compress or modify the original file, only the signature is added in the end.
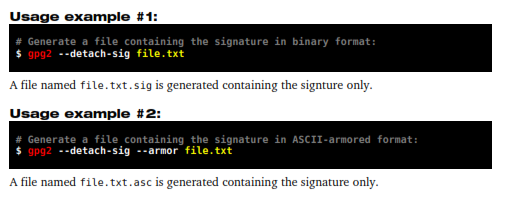
11.1.3 – Detached signature
This method generates a new file containing the signature only. This method is recommended to be used when the original file may be distributed through several different ways, such as for download on different websites, since the signature may be obtained apart.
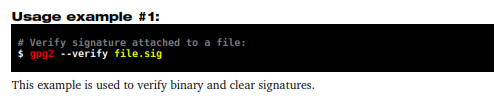
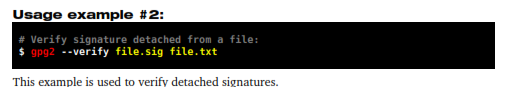
11.2 – Verifying signatures
This process is used to verify if the signature corresponds to the author of the original file. It can be done either for attached or detached signatures.
11.3 – Extracting files from signed files
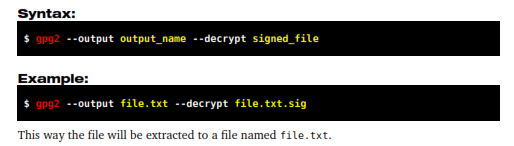
After you verify the file's signature you may want to extract the original
When you obtain a signed file and verify its signature you may want to extract the original file from it. Another reason for that is that signed files are often given encrypted. You can extract it using the --decrypt command, as shown below:
11.4 – Choosing between multiple keys
Check out chapter 10.4 for more information on this.









