CHAPTER 10
Encrypting and decrypting
Encrypting and decrypting files is the main purpose of GnuPG, you can do it for yourself or for others. There are two ways to do it: using symmetric and asymmetric. Encryption.
10.1 – Encrypting files
In GnuPG you can encrypt files for yourself and for others. There are two ways to do this: using symmetric encryption and asymmetric encryption. For more information about these methods check out chapter 3.
10.1.1 – Through asymmetric encryption
This is the most common method of encrypting files for others. You need the other person's public key to do it. You can also use it to encrypt files for yourself.
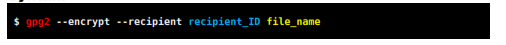
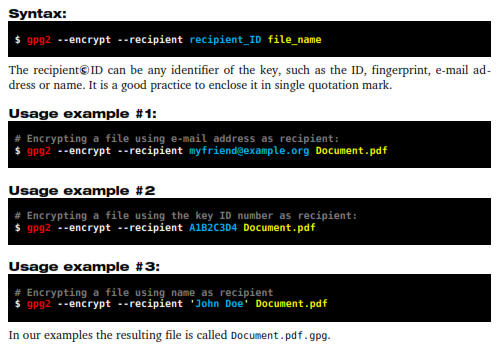
The recipient's ID can be any identifier of the key, such as the ID, fingerprint, email address or name. It is a good practice to enclose it in single quotation mark.
10.1.2 – Through symmetric encryption
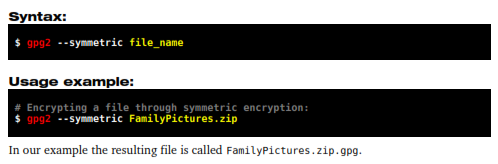
This method is recommended to encrypt files for yourself only, since it uses a single password and does not specify a receiver.
10.2 – Decrypting files
You may need to decrypt files from others or the ones you encrypted yourself. The syntax to do it is the same. It is necessary to have the sender's public key to decrypt files.
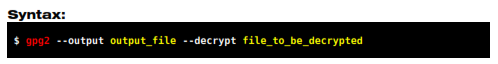
The recipient's ID can be any identifier of the key, such as the ID, fingerprint, email address or name. It is a good practice to enclose it in single quotation mark.
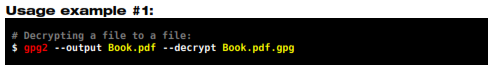
In this example the file is output to another file. It is the preferred method to decrypt files. In our example the resulting file is called Book.pdf.

In this example the file is output to the screen. This method should only be used for short text files, or when combined with more advanced piping commands.
10.3 – Changing the output filename
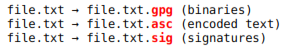
By default output files from GnuPG are named according to the original file, adding the adequate extension. For example:
You can easily change this behavior and choose the name you desire for the output file, as indicated in the examples below:
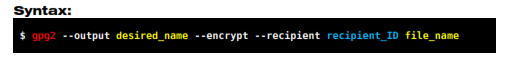
The recipient's ID can be any identifier of the key, such as the ID, fingerprint, email address or name. It is a good practice to enclose it in single quotation mark.
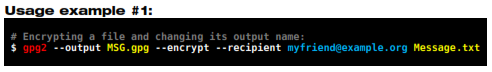
In this example the file Message.txt after being encrypted will be named MSG.gpg.
The output filename change also work with other GnuPG operations, such as signing, which is covered in the next chapter but can be seen in the example below:
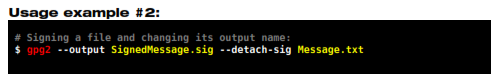
In this example it is generated a detached signature of the file Message.txt which is called SignedMessage.sig.
10.4 – Choosing between multiple keys
If you have multiple private keys in your keyring you will have to choose between them depending on the operation and the recipient you are working with, otherwise GnuPG will use the key that is set as default.
To choose a key between multiple private keys use the option --local-user after the desired operation, as shown in the examples below:
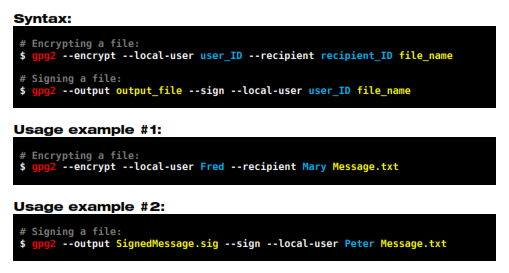
As you could notice, this step also works with other operations such as signing, covered in the next chapter.














