5. SECURITY
Prof. Kalyan Som is analyzing the fourth element of deep analytics - security [Figure 1.5]. What do you mean by technology-security? A system may face various types of threats from both external and internal environments but it should be vigilant and protected through a set of security policies. An emerging technology demands the support of an adaptive security architecture so that the associated system can continuously assess and mitigate risks intelligently. Adaptive security is a critical feature of a technology that monitors the network or grid associated with a system in real time to detect any anomalies, vulnerabilities or malicious traffic congestion and. If a threat is detected, the technology should be able to mitigate the risks through a set of preventive, detective, retrospective and predictive capabilities and measures. Adaptive security analyzes the behaviors and events of a system to protect against and adapt to specific threats before the occurrence of known or unknown types of malicious attacks.
Let us explain the objectives of adaptive security architecture in depth. New threats are getting originated as an outcome of technology innovation and may cause new forms of disruptions with severe impact. Today, it is essential to deploy adaptive security architecture for the emerging technologies. The systems demand continuous monitoring and remediation; traditional ‘prevent and detect’ and incident response mindsets may be not sufficient to prevent a set of malicious attacks. It is required to assess as-is system administration strategies, investment and competencies; identify the gaps and deficiencies and adopt a continuous, contextual and coordinated approach.
How to verify the security intelligence of the system associated with an emerging technology? It is essential to verify security intelligence of a technological innovation collectively through rational threat analytics at five levels : L1, L2, L3, L4 and L5 (Figure 1.5). It is essential to assess risks associated with an emerging technology and mitigate the risks by adopting a set of countermeasures. The basic building blocks of the security element are an adversary model and an intelligent threat analytics. An adversary is a malicious agent who attacks a system or a protocol; the basic objectives are to cause disruption and malfunctioning of a secure system. The security element should be analyzed in terms of the assumptions, goals and capabilities of the adversary. It is also crucial to analyze the adversary model in terms of environment, location, network, resources, access privileges, equipments, devices, actions, results, risks, reasons and motivations of attacks and probable targets (i.e. why the adversary attacks and to obtain what data).
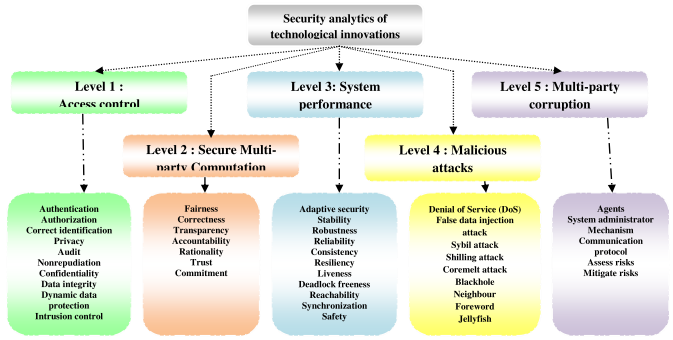
Figure 1.5 : Security analytics
Let us consider the security of an information system innovation. At level L1, it is required to verify the efficiency of access control in terms of authentication, authorization, correct identification, privacy, audit, confidentiality, non-repudiation and data integrity. For any secure service, the system should ask the identity and authentication of one or more agents involved in a transaction. The agents of the same trust zone may skip authentication but it is essential for all sensitive communication across different trust boundaries.
After the identification and authentication, the system should address the issue of authorization. The system should be configured in such a way that an unauthorized agent cannot perform any task out of scope. The system should ask the credentials of the requester; validate the credentials and authorize the agents to perform a specific task as per agreed protocol. Each agent should be assigned an explicit set of access rights according to role. Privacy is another important issue; an agent can view only the information according to authorized access rights. A protocol preserves privacy if no agent learns anything more than its output; the only information that should be disclosed about other agent’s inputs is what can be derived from the output itself. The agents must commit the confidentiality of data exchange associated with private communication.
Privacy is the primary concern of the revelation principle of an information system; the issue of secure private communication can be addressed through the concept of cryptography, digital signature, signcryption and secure multiparty computation.
The fundamental objectives of cryptography are to provide confidentiality, data integrity, authentication and non-repudiation. Cryptography ensures privacy and secrecy of information through encryption methods. Data integrity ensures that data is protected from unauthorized modifications or false data injection attack. The system should provide public verifiability so that anyone can verify the integrity of the data. Redundancy of data is a critical issue which is resulted through replication across the writers.
Traditionally, cryptographic solutions are focused to ensure information security and privacy. But there are other different types of security concerns. At level L2, it is required to verify the efficiency of secure multiparty computation associated with a technological innovation in terms of fairness, robustness, correctness, transparency, accountability, trust and commitment. A protocol ensures correctness if the sending agent broadcasts correct data and each recipient receives the same correct data in time without any change and modification done by any malicious agent. Fairness is associated with the commitment, honesty and rational reasoning on payment function, trust and quality of service. Fairness ensures that something will or will not occur infinitely often under certain conditions. The recipients expect fairness in private communication according to their demand plan, objectives and constraints. The sending agent expects fairness from the recipients in terms of true feedback and commitment on confidentiality of data. As per traditional definition of fairness of secure multi-party computation, either all parties learn the output or none. The system must ensure the accountability and responsibility of the agents in access control, data integrity and non-repudiation. In fact, accountability is also associated with collective intelligence. Transparency is associated with communication protocols, revelation principle and automated system verification procedures. For example, a mechanism should clearly state its goal to define a policy. There exist an inherent tension between transparency and privacy. A fully transparent system allows anyone to view any data without any provision of privacy. On the other side, a fully private system provides no transparency. Privacy can be achieved using cryptographic techniques at increased cost of computation and communication. Is it possible to trade-off privacy vs. transparency? Is it possible to provide public verifiability of its overall state without disclosing information about the state of each entity? Public Verifiability allows anyone to verify the correctness of the state of the system.
Next, it is required to verify the system performance at level L3 in terms of stability, robustness, reliability, consistency, resiliency, liveness, deadlock freeness, reachability, synchronization and safety. The performance of a system and quality of service is expected to be consistent and reliable. Reachability ensures that some particular state or situation can be reached. Safety indicates that under certain conditions, an event never occurs. Safety is a critical requirement of any system whether it may be mechanical, electrical, electronics, information technology, civil, chemical, metallurgical or instrumentation engineering. Liveness ensures that under certain conditions an event will ultimately occur. Deadlock freeness indicates that a system can never be in a state in which no progress is possible; this indicates the correctness of a real-time dynamic system. Another important issue is robustness of a system. The delivery of the output should be guaranteed and the adversary should not be able to threaten a denial of service attack against a protocol.
At level L4, it is required to assess the risks of various types of malicious attacks by adversaries on a system such as Denial of Service (DoS), false data injection attack, sybil attack, shilling attack, coremelt attack (or network traffic congestion), blackhole, neighbor, node deletion, rushing and jellyfish attacks. At level L5, it is required to assess the risks of various types of corruptions such as agents (e.g. sending agent, receiving agents), system administrator, communication protocol and payment function of a mechanism associated with a technological innovation.
For example, prevention and detection are traditional approaches to the security of a system. In today’s world of expanding threats and risks, real-time system monitoring is essential to predict new threats and automate routine responses and practices. The system should not only rely on traditional prevent-and-detect perimeter defense strategies and rule based security but should adopt cloud based solutions and open application programming interfaces also. Advanced analytics is the basic building block of next generation security protection which should be to manage an enormous volume, velocity and variety of data through AI and machine learning techniques. Intelligent analytics are expected to detect anomalous patterns by comparing with the normal profile and the activities of the users, peer groups and other entities such as devices, applications and smart networks and trigger alarms by sensing single or multiple attacks on the system. The security element must overcome the barriers among security, application development and operations teams and be integrated deeply into system architecture.
Next, it is essential to develop effective ways to move towards adaptive security architecture. The mechanism should surfaces anomalies and adjusts individualized security controls proactively in near real-time to protect the critical data of a system. Adaptive Security with dynamic data protection is expected to offer many benefits over traditional security platforms depending on the size of the system and complexity of networking schema – real time monitoring of events, users and network traffic; autonomous and dynamic resolutions; prioritization and filtering of security breaches; reduction of attack surface and impact or damage of a threat and reduction of resolution time. The emerging technology is expected to adapt to the needs of a system irrespective of the size of network, nature of operation or exposure of threats. It can assess the requirements of security with greater accuracy through a set of intelligent policies and procedures and can ensure better understanding of strength, weakness, opportunities and threats of the security architecture.
Security Analytics
Agents: System analysts, business analysts, technology management consultants;
Objects / entities: sustainable smart cities, smart villages, communities, smart world, smart universe;
Global security parameters: define a set of sustainable development goals. /* Refer to scope and system analytics, sections 1 and 2 */
Verification algorithm : audit security intelligence of emerging technology innovation.
- access control: verify authentication, authorization, correct identification, privacy, audit confidentiality, data integrity and non-repudiation;
- computational intelligence: verify rationality, fairness, correctness, transparency, accountability, trust and commitment;
- system performance of SOA: verify reliability, consistency, scalability, resiliency, liveness, deadlock freeness, reachability, synchronization, safety;
- malicious attacks: verify the risk of Sybil, false data injection, shilling: push and pull, denial of service (DoS), coercion or rubber hose attack, fault injection attack, node replication wormhole, blackhole, neighbor, jellyfish, coremelt attack;
- web security: session hijack, phishing, hacking, cross site request forgery, cross site script, broken authentication, improper error handling;
- multi-party corruption: system analysts, business analysts, system administrators, innovators; call threat analytics and assess risks of emerging technologies:
- what is corrupted or compromised (agents, computing schema, communication schema, data schema, application schema)? detect type of threat.
- time : what occurred? what is occuring? what will occur? assess probability of occurrence and impact.
- insights : how and why did it occur? do cause-effect analysis on performance, sensitivity, trends, exception and alerts.
- recommend : what is the next best action?
- predict : what is the best or worst that can happen?
Output: security intelligence
It is essential to verify security intelligence of emerging technologies for humanity collectively through rational threat analytics. The security intelligence is a multi- dimensional parameter which should be verified at multiple levels. Each emerging technology must be developed and audited by a group of authorized agents such as business analysts, system analysts and system administrators. The scope of BBIS should be correctly identified in terms of a set of corporate functions and performance metrics; relevant data should be sourced through authenticated raters. The system should preserve confidentiality and privacy of the raters and system administrators, nonrepudiation and integrity of data. For business performance measurement, the system should ask the identity and authentication of the raters. After correct identification and authentication, the system should address the issue of authorization. The system should be configured in such a way that an unauthorized agent cannot perform any task out of scope. The system should ask the credentials of the requester; validate the credentials and authorize the agents to perform a specific task. The raters and analysts should be assigned an explicit set of access rights according to role. Privacy is another important issue; the analysts and the raters can view only the information according to authorized access rights.
It is also crucial to verify the computational intelligence of BBIS in terms of fairness, correctness, rationality, transparency, accountability, trust and commitment. The raters are expected to provide fair and correct rating of each performance metric through proper justification, evidence, examples and case studies. The trust and commitment of the raters should be validated by the system administrator. The scorecard may be corrupted by dishonest raters, system administrators, business and system analysts, data visualization and data interpretation schema.
The web enabled scorecard must evaluate the corporate performance and the related financial impact in terms of reliability, consistency, resiliency, liveness and stability. The performance of the system is expected to be consistent and reliable. Reachability ensures that some particular state or situation can be reached. Safety indicates that under certain conditions, an event never occurs. Liveness ensures that under certain conditions an event will ultimately occur. Deadlock freeness indicates that the system should never be in a state in which no progress is possible. The scorecard should be protected from various types of malicious attacks such as false data injection attack, fault attack, denial of service attack, Sybil attack, shilling attack (push and pull attack). The raters should not be able to inject false data to push or pull the performance of an entity incorrectly. The BBIS system is expected to be an interactive system through which the raters can justify the quality of reasoning and decision making capabilities.
The scorecard is expected to be a resilient system. The resiliency measures the ability to and the speed at which the web enabled system can return to normal performance level following a disruption in survey. The system administrator face a set of challenges to solve the problem of resiliency: what are the critical issues to be focused on? what can be done to reduce the probability of a disruption? what can be done to reduce the impact of a disruption? How to improve the resiliency of the service oriented architecture? The critical steps of risk assessment are to identify a set of feasible risk metrics; assess the probability of each risk metric; assess severity of each risk metric and plot each risk metric in project vulnerability map. The critical steps of risk mitigation are to prioritize risks; do causal analysis for each risk metric; develop specific strategies for each cell of vulnerability map and be adaptive and do system monitoring.
Let us try to ask a set of basic questions to define security: what is poverty? what are the causes of poverty? what are the effects of poverty? How can we assess risks of poverty? How can we mitigate the risks of poverty? How can we create new jobs through business model innovation? How can we fight against environmental pollution? What should be rational public policy to ensure social security? Traditionally, poverty means not having enough money to satisfy the basic needs of life such as food, clothing, home, education, healthcare, energy and utilities. Many poor people may have jobs, but do not earn enough money to satisfy the aforesaid basic needs. The World Bank has defined poverty in absolute terms. The bank defines extreme poverty as living on less than US$1.90 per day and moderate poverty as less than $3.10 a day. It was as been estimated that in 2008, 1.4 billion people had consumption levels below US$1.25 a day and 2.7 billion lived on less than $2 a day. Rural poverty is often caused by poor infrastructure that hinders development, mobility and agricultural activities (e.g. access to agricultural inputs and markets). Without roads, the rural poor people are cut off from technological development and emerging markets in urban zones. The causes of child poverty may be poor parents, adult poverty, government policies, lack of education, unemployment, social services, disabilities and discrimination.
Poverty is not just lack of money; it is not having the capability to realize one’s full potential as a human agent. It is a multidimensional problem and each dimension requires a different solution. There is no one gun to shoot all the problems in a simple way: the problems of healthcare or food are different from those of education or energy. Monetary dole may work to reduce desperation to some extent. The poor people should have access to essential resources of living at optimum level. But, there are several other constraints. The rich and super rich people of urban zone are often involved in overconsumption of resources. There are threats of intrusion, infiltration and migration of refugees who may consume resources of a country or a state irrationally through various ways.
Let us consider an example. The refugees of country B are migrated to country I at mass scale. Those refugees try to capture the essential resources of life of the people of country I through strategic alliance and local colony development and try to capture job market aggressively. The local people of country I become the victims of poverty and get unemployed due to the economic stress caused by the intrusion and infiltration of the refugees from country B. The problem may be extended to the migration of people from a poor, underdeveloped and unfertile state to a developed state of a country. Therefore, irrational resource consumption by the rich and super rich classes and intrusion, migration and infiltration of the refugees may be critical causal factors of poverty. Existing works on poor economics and poverty should address these issues critically. What should be the strategy for the intruders or refugees? Country I should help country B for the economic and social development through collaborative planning, emerging technology transfer and effective rehabilitation programmes for the poor refugees. Border security force may not be able to control the intrusion correctly.
The innovation, adoption and diffusion of emerging technologies are expected to improve the growth rate of economy at macro level and profits and market shares of the firms at micro level. For developing countries, access to emerging technology should boost nation's economy by reducing the cost of production, saving of labour, automation, growth of new business models, intelligent communication system, optimal capacity utilization, allocation and distribution of various natural resources. It is hard to fight against climate change such as global warming Poverty increases health risks due to food insecurity; poor children may have lower birth weight and life expectancies. It is interesting to explore the scope of technology for humanity: how to create jobs through business model innovation and economic growth through industrial revolution. There are other various issues of human resource management such as minimum wage, pay equity, paid leave and paid sick days and rational work schedules. Social security is crucial for the poor people who are unable to satisfy the basic needs of life such as food, clothing, housing, education, healthcare, energy and utilities. The social development occurs if a society can apply technological advances and reflect the same to their social life. Economic development improves the standard of living and quality of life of a nation from low to high income economy. Science, Technology, Engineering and Mathematics (STEM) is important to ensure social, financial and information security globally today.
Emerging and innovative agriculture technologies should be applied to end hunger through food security, improved nutrition and sustainable agriculture. It is crucial to improve agricultural productivity and incomes of small-scale food producers through sustainable food production systems and improving land and soil quality. Agriculture is the single largest employer for 40% of the global population and largest source of income for poor rural households. Women make up about 43% of the agricultural labor force in developing countries and over 50% in Asia and Africa; but own only 20% of the land. It is possible to ensure food security through advanced agriculture and food processing technologies (e.g. maintaining genetic diversity of seeds, increasing access to land, preventing trade restriction and distortions in world agricultural markets to limit extreme food price volatility, eliminating waste through International Food Waste Coalition, and ending malnutrition and undernutrition of children).
Advanced effective life-science, healthcare, biomedical engineering and biotechnologies should be applied to ensure health security through universal health coverage, access to essential medicines and vaccines, to end the preventable death of newborns and children under 5 and to end epidemics (e.g. AIDS, tuberculosis, malaria, and water borne diseases) and prevention and treatment of substance abuse, deaths and injuries from traffic accidents and from hazardous chemicals and air, water and soil pollution and contamination. Global security policy should focus on good health and well-being for people for all at all ages by increasing life expectancy and reducing common killers of child and maternal mortality. Another critical area is cancercare.
Emerging digital technologies (e.g. Internet, TV, Radio) should be used to provide inclusive and equitable quality education and promote lifelong learning opportunities for all. Major progress is expected in access to education, specifically at the primary school level, for both boys and girls. The number of out- of-school children has reduced from 112 million in 1997 to 60 million in 2014. Still, at least 22 million children in 43 countries miss out on pre-primary education; 103 million youth worldwide still lack basic literacy skills and more than 60 percent of those are women. Massive open online courses (MOOCs) are free open education offered through online platforms to a wider audience. Education for Sustainable Development (ESD) is defined as education that encourages changes in knowledge, skills, values and attitudes to enable a more sustainable and equitable society. It aims to empower and equip current and future generations to meet the needs using a balanced and integrated approach to the economic, social and environmental dimensions of sustainable development.
Emerging technologies should be used to ensure energy security in terms of affordable, reliable and sustainable clean energy for all by increasing the share of renewable energy (e.g. solar power, wind power) in the global energy mix, improving energy efficiency and enhancing international cooperation to facilitate more open access to clean energy technology and more investment in clean energy infrastructure. Another challenge is to ensure drinking water supply, availability and sustainable management of water and sanitation for all. 6 out of 10 people lack safely managed sanitation services and 3 out of 10 lack safely managed water services globally. Safe drinking water and hygienic toilets can protect people from diseases due to water pollution.
Manufacturing is a major source of employment in our society. It is crucial to build resilient infrastructure, promote inclusive and sustainable industrialization and foster innovation in discrete, batch and continuous production technology, to improve manufacturing value added per capita in developing world and improve productivity and yield. Modern construction, mechanical, electrical and electronics engineering and nano-housing technologies must be applied to develop smart cities and villages and inclusive, safe, resilient, and sustainable human settlements. It is crucial to give access to safe and affordable housing in densely populated slum areas. ERP and SCM systems should be used to monitor responsible consumption and production of essential resources through various means such as eco- friendly production methods and reducing the amount of waste by recycling and reuse in developed and developing countries. We must take precautions and proper actions to combat against climate change, global warming and extreme weather conditions by regulating emissions and promoting developments in renewable energy such as solar and wind power.
Innovative biological technologies, rational and regulated business practice and advanced marine science should be used to protect life below water, to conserve and sustainably use the oceans, seas and marine resources for sustainable development, to mitigate adverse effects of increased ocean acidification, water pollution and negative impact on marine biodiversity. Oceans cover 71% of the Earth's surface making the planet livable. Rainwater, drinking water and global climate are regulated by ocean temperatures and currents. Over 3 billion people depend on marine life for their livelihood. Oceans absorb 30% of CO2 produced by humans. The oceans contain about 200,000 species. Oceans are the world's largest sources of protein. But, the marine world is facing various types of threats such as marine pollution at shocking levels (e.g. 15 tons of plastic are released into the oceans per minute), 26% increase in acidification, death of 30 percent of marine <




