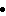4. SECURITY
Security Analytics
Organization : global earth science organizations;
Verification mechanism: audit security intelligence.
 security policy: verify rationality, fairness, correctness, transparency, accountability, trust and commitment;
security policy: verify rationality, fairness, correctness, transparency, accountability, trust and commitment;
 system performance: verify reliability, consistency, scalability, resiliency, liveness, deadlock freeness, reachability, synchronization, safety;
system performance: verify reliability, consistency, scalability, resiliency, liveness, deadlock freeness, reachability, synchronization, safety;
 multi-party corruption: do surveillance through security council of global organization, police, army, detectives, journalists ;
multi-party corruption: do surveillance through security council of global organization, police, army, detectives, journalists ;
o Safety from natural disaster
o Safety from war, bioterrorism and acts of terrorisms
 access control: verify authentication, authorization, correct identification, privacy, audit confidentiality, data integrity and non-repudiation;
access control: verify authentication, authorization, correct identification, privacy, audit confidentiality, data integrity and non-repudiation;
 malicious attacks: verify the risk of false data injection, denial of service (DoS) and fault injection attack;
malicious attacks: verify the risk of false data injection, denial of service (DoS) and fault injection attack; call threat analytics and assess risks of emerging technologies:
call threat analytics and assess risks of emerging technologies:
 what is corrupted or compromised (agents, computing schema, communication schema, data schema, application schema)?
what is corrupted or compromised (agents, computing schema, communication schema, data schema, application schema)?
 time : what occurred? what is occuring? what will occur? assess probability of occurrence and impact.
time : what occurred? what is occuring? what will occur? assess probability of occurrence and impact.
 insights : how and why did it occur? do cause-effect analysis on performance, sensitivity, trends, exception and alerts.
insights : how and why did it occur? do cause-effect analysis on performance, sensitivity, trends, exception and alerts.
 recommend : what is the next best action?
recommend : what is the next best action?
 predict : what is the best or worst that can happen?
predict : what is the best or worst that can happen?
Output: security intelligence
Dr. Kalin Croft and Dr. Han are debating on the security intelligence of emerging technologies against natural disasters. The security of the technological innovation related to artificial rainfall and multi-agent collaborative resource sharing mechanism should be analyzed from the perspectives of fairness, correctness, transparency, accountability, reliability, consistency, resiliency, authorization and authentication in access control, trust and commitment. It is really a hard task to estimate the resource to be allocated and shared fairly and correctly in time. The resource sharing mechanism should be transparent to all the stakeholders through intelligent broadcast communication. The operators and the administrators of the system should be accountable for any mishap due to the natural disaster such as timely release of water from the dam during heavy rainfall in the rainy season or proper storage of water in the dam during the summer and the winter for proper irrigation to the fields of agriculture. The performance of the system is expected to be evaluated in terms of reliability and consistency. Who will take the decision of artificial rain? The system should be operated by the authenticated and authorized decision making agents only since it is a very sensitive issue, which is related to the safety and security of a large number of human beings, plants and animals over a specific zone (e.g. it may be a district or a state or even a country).
A group of authorized agents should be able to access the technology of artificial rainfall. They should be able to communicate through authenticated channels for taking important decisions on artificial rainfall. They should be able to identify correctly the demand of artificial rainfall based on evaluation of drought and flood in a country. The decisions should be evaluated and justified based on fairness, correctness, transparency of resource sharing policy, accountability of DMA, rationality, trust and commitment. Rationality is the most important decision making factor of artificial rainfall.. There are threats of multi-party corruptions and various types of malicious attacks on the technology of artificial rainfall and cloud seeding technology. The system should be free of denial of service attack, false data injection, Sybil, shilling and fault attack. The system performance should be verified in terms of reliability, consistency, resiliency, liveness, safety, deadlock freeness and reachability. Flaws in rational decision making may result flood or drought in critical zones globally.
Test case : Water Riot
Prof. Hariharan is presenting a case of water sharing conflict between two states U (upstream state) and D (downstream state) associated with a river (R). There is lack of mutual cooperation and trust between two states in the context of water sharing of river R. Initially, the Supreme Court (SC) orders the state government of U to release water of 15000 cusec / day; then 12000 cusec / day; then 6000 cusec water / day to the state D. There was a water riot in state U; the mob torched 42 buses; a leader was killed. Inlow from U was 15000 cusecs/ day last week. 12000 cusecs was being released everyday from Dam X from 20.9.2016. Release amounts to 1 tmcft; paddy raised in 14.9 L acres. Then, the inflow from U was reduced to 3000 cusecs on Wednesday evening; 21.9.2016. SC orders U to release 6000 cusec water / day for rest of September’2016. The State Govt. of U called all party meeting and had taken decision collectively; a legislative resolution was taken to defy SC order; stop release of water for agriculture (e.g. samba cropping) and water to be released only for drinking purpose.
The State Govt. of D did not call any all party meeting. This is a fresh controversy. Defiant U triggers a constitutional crisis since it is defying SC order to release 6000 cusecs per day to TN. The special legislature session is expected to adopt a resolution that SC order cannot be implemented as it is contrary to the public interest in the state U. U does not have adequate drinking water. By projecting it a legislature-judiciary confrontation, the state Govt. of U hopes to escape the charge of commitment to the court.
Many in U are concerned with the silence of the central government. The centre can not be a bystander since the issue is with the Supreme Court (SC). The PM should take initiatives to prevent a constitutional crisis. It is his duty to protect the federal structure. The decision of the Govt. of U cannot be seen as an act of defiance but as the helplessness of a state ravaged by a court order that cannot be implemented. If U defies SC order, then there are serious risks for river sharing agreements. The tension between U and D will grow since both states are feeling pressure. Outright defiance of SC may boomerang and set an extremely dangerous precedent. SC directs to form river R board having representatives from four neighboring states U,D, Y and Z. Even in the absence of state representative, the board can take decisions by majority option. So, it is in the interest of the riparian states to nominate the members otherwise they will lose the opportunity to protect their rights.
The output of the analytics is as follows: Irrigation in state D is more than 20L acres which is now 18L acres; the same in state U is 6.5L acres which is now 15 L acres. About 80% of the annual yield from river R is utilized by the farmers of D. It has now come down to 57%. The state U was using 16% now gets 37%. The water received from U by D is 4.57 tmcft during 2010-11; 28.06 during 2011-2012; 135.77 during 2013-2014 and 76.31 during 2014-15. The major cities of U consume drinking water as 26 tmcft by city B; 6 tmcft by city E; the city C of state D consumes 7 tmcft. Present water level at X Dam : 86.94 ft; storage now 44.21 tmcft. Sharp increase in irrigated farm acreage and drinking water use in the state U has deprived D of what it considers its right share. Rainfall in D in September’2016 is high. What should be the water sharing mechanism among states U, D, Y and Z?

Figure 2.4 : Deep Barringer Crater, Winslow, Arizona; Meteriotes

Figure 2.5 : Asteroids, Comets
Test Case : Astronomical Hazards
Prof. Nancy Regon is presenting a test case of astronomical hazards and explores the scope of the aforesaid probabilistic search mechanism (RPSM) to assess and mitigate those threats. The universe is basically a computer, its history is being computed continuously (Zuse,1967). It is not possible to restrict the occurrence of astronomical hazards; but we have try to protect our earth from total destruction. The astronomical hazards may be really dangerous threats against the sustainability of today’s human civilization and the existence of a safe earth. This type of probabilistic search problem is really hard to solve, it is not a trivial problem. Let us discuss the motivation of this threat in details based on the information and images given in figures (2.4,2.5) .
Asteroids are the largest of space rocks; most of them circle the Sun in the asteroid belt. Many of 3000 known asteroids are only a few miles across and all of them together would weigh much less than the Moon. Ceres, the largest asteroid, is about 600 miles across; Pallas and Vesta are about 350 miles in diameter. Bright comets are visible in the sky only once or twice in a century and stay for many days or weeks. Meteors flash in the sky every night or day. Meteor flashes are known as shooting stars. But meteors are not stars. Meteors begin as meteoroids in the form of rock or metal that orbit around the Sun. But, sometimes meteoroids plunge into Earth's atmosphere at speeds faster than a bullet. The friction with air particles makes them glow red hot and is called meteors. The bright flash is seen for only a few seconds. Perhaps as many as 100 million meteoroids enter the Earth's atmosphere every day. Most are just small pieces of rock and burn in an instant; some become dazzling fireballs and fall to the earth surface called meteorite.
Figure 2.6 : Structure - Astronomical Hazards Detection System
Problem of astronomical hazards : Will an or large number of asteroids or a large meteorites ever hit Earth? Many large objects had hit our earth in the past and resulted huge hollows in the ground known as impact craters. The largest is the 4150 foot wide and 600 foot deep Barringer Crater near Winslow, Arizona. Is there any probability of mass destruction of human civilization and the earth due to the strike of a comet or the shower of numerous large meteorite or asteroids in future? How to protect our earth from the threat of such type of astronomical hazards? One possible solution may be the real-time probabilistic search. The basic objective of the search is to detect the motion of the asteroids, meteors and comet moving dangerously towards the earth in terms of distance, time and size of the objects. The target’s position may be uncertain or there may be incomplete information about its size and location. The automated light beam search is expected to be conducted with various types of sensors such as telescopes and satellites. The detection function gives the probability of detection for a search as a function of effort (e.g. search area, distance, time) and evaluates the effectiveness of search efforts in terms of probability of detecting the incoming objects.
Real-time Probabilistic Search Mechanism (RPSMah) :
Agents : System administrator (Space Research Organization), Human agents;
Input: Data stream sensed by the sensors, Rough definition of target, Detection function;
Output: Identify objects or moving targets such as asteroids and meteors coming very near to the earth within threshold distance;
Moves: Real-time search, group testing, adaptive secure multi-party computation, automated data stream mining by intelligent threat analytics;
Procedure:
Divide the search space into a set of private blocks;
Assign resources (sensors, satellites, earth station) to each private block; each block is monitored independently; /* the resources of different blocks interact with each other through coordination mechanism and secure broadcast communication protocol (Internet) */;
Project light beam from the sensors on private search space  move forward and backward repeatedly;
move forward and backward repeatedly;
Filter data stream;
Detect target  verify correctness to avoid false alarm
verify correctness to avoid false alarm  call threat analytics
call threat analytics 
 give alert.
give alert.
Risk Mitigation Strategies:
- Proactive security (Before astronomical hazards):
 Learn drop-cover-hold
Learn drop-cover-hold
 Have an emergency kit ready and always carry (if possible).
Have an emergency kit ready and always carry (if possible).
 Build a disaster proof house as per the advice of structural or civil engineering consultant; repair deep cracks on ceilings and walls of the house; fix shelves securely to the walls, avoid heavy loading of the rooms.
Build a disaster proof house as per the advice of structural or civil engineering consultant; repair deep cracks on ceilings and walls of the house; fix shelves securely to the walls, avoid heavy loading of the rooms.
 Safe shelter : (a) build artificial caves at critical locations in urban and rural zone; (b) build robust shed on the roof made of steel (Fe) / Al / Tin (Sn) structure;
Safe shelter : (a) build artificial caves at critical locations in urban and rural zone; (b) build robust shed on the roof made of steel (Fe) / Al / Tin (Sn) structure;
 Wear robust helmets and jackets
Wear robust helmets and jackets
 Give alert through broadcast communication -
Give alert through broadcast communication - take safe shelter in time;
take safe shelter in time;
 Laser beam projection for object decomposition after detection of incoming objects through probabilistic real-time search;
Laser beam projection for object decomposition after detection of incoming objects through probabilistic real-time search;
 Artificial collision of asteroids and meteors, network traffic congestion or
Artificial collision of asteroids and meteors, network traffic congestion or traffic diversion in space
traffic diversion in space
 Activate Antenna for blocking and throttling (i.e. slowing speed) of incoming objects entered into the earth based on the principle of electromagnetic induction;
Activate Antenna for blocking and throttling (i.e. slowing speed) of incoming objects entered into the earth based on the principle of electromagnetic induction;
 Divert the traffic to the desert or remote zone to minimize the negative impact of astronomical hazards.
Divert the traffic to the desert or remote zone to minimize the negative impact of astronomical hazards.
 During astronomical hazard
During astronomical hazard
 Remain calm and do not panic.
Remain calm and do not panic.
 Take shelter under a table, cover head with hands and hold the table till the hazards last;
Take shelter under a table, cover head with hands and hold the table till the hazards last;
 If you are outside, move towards buildings, trees, walls and poles and take shelter;
If you are outside, move towards buildings, trees, walls and poles and take shelter;
 I you are inside a vehicle; pull over in a covered place and remain inside.
I you are inside a vehicle; pull over in a covered place and remain inside.
 After astronomical hazards
After astronomical hazards
 Avoid entering damaged civil infrastructure (residential flats, office buildings, industrial plants).
Avoid entering damaged civil infrastructure (residential flats, office buildings, industrial plants).
 Use stairs instead of lifts and elevators.
Use stairs instead of lifts and elevators.
 If trapped in rubble or damaged infrastructure, sound whistle, clap or shout, avoid lighting matchstick, turn on search lights of mobile phones, tap on a pipe or a wall safely.
If trapped in rubble or damaged infrastructure, sound whistle, clap or shout, avoid lighting matchstick, turn on search lights of mobile phones, tap on a pipe or a wall safely.
Adaptive security & dynamic data management : Our earth may face various types of threats from both external and internal environments but it should be vigilant and protected through a set of intelligent security policies, protocols and mechanisms. An emerging technology demands the support of an adaptive security architecture so that the associated system can continuously assess and mitigate risks intelligently. Adaptive security is a critical feature of a technology that monitors the space in real- time to detect any anomalies, vulnerabilities or malicious traffic congestion. If a threat is detected, the technology should be able to mitigate the risks through a set of preventive, detective, retrospective and predictive capabilities and measures. Adaptive security analyzes the behaviors and events of the space to protect against and adapt to specific threats before the occurrence of known or unknown types of astronomical hazards. Adaptive security monitors the space in real time to detect anomalies, malicious traffic and vulnerabilities. If a threat is detected, it is essential to counter the threat in various ways. Preventative capabilities allow to create infrastructure, products, processes and policies that can mitigate the astronomical hazards. The detective capabilities should identify those threats in time at minimum impact and not detected by preventative capabilities. Retrospective capabilities should perform in-depth analysis of threats not detected by the detective layer to avoid such types of attacks in future. Predictive capabilities provide alerts about external events and anticipates new types of threats.
Let us consider the technology associated with adaptive security and dynamic data management for the protection of our earth. Today, it is essential to deploy adaptive security architecture for real-time moving target search. A smart grid demands continuous monitoring and remediation; traditional ‘prevent and detect’ and incident response mindsets may be not sufficient to prevent astronomical hazards. Adaptive security is an essential part of solar computing. It is required to assess as-is system administration strategies, investment and competencies; identify the gaps and deficiencies and adopt a continuous, contextual and coordinated approach. For example, prevention and detection are traditional approaches to the security of our earth. In today’s universe of expanding threats and risks, real-time system monitoring is essential to predict new threats and automate routine responses and practices. Advanced analytics is the basic building block of next generation security protection which should be to manage an enormous volume, velocity and variety of data through AI and machine learning techniques for the protection against astronomical hazards.
Dynamic data management is an effective way to move towards adaptive security architecture. DDM surfaces anomalies and adjusts security controls proactively in near real-time to protect our earth. Adaptive Security with dynamic data management is expected to offer many benefits over traditional security platforms : real-time monitoring of events and traffic; autonomous and dynamic resolutions; prioritization and filtering of security breaches; reduction of attack surface and impact or damage of a threat and reduction of resolution time. This technology is expected to adapt to the needs of the system irrespective of the size of network, nature of operation or exposure of threats. It can assess the requirements of the security of our earth with greater accuracy through a set of intelligent policies and procedures and can ensure better understanding of strength, weakness, opportunities and threats of the security architecture.