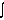4. SECURITY
Security Analytics Security schema :
 Snubber circuit for high dv/dt and di/dt protection
Snubber circuit for high dv/dt and di/dt protection
 Fuses for fault protection
Fuses for fault protection
 Heat sink for thermal runaway
Heat sink for thermal runaway
 Reverse recovery transients
Reverse recovery transients
 Supply and load side transients
Supply and load side transients
Emerging technologies:
 Digital relays for voltage, current and frequency protection;
Digital relays for voltage, current and frequency protection;
 Earthing system: Earthing rod, lightning arrester;
Earthing system: Earthing rod, lightning arrester;
 Switchgear : Fuse, MCB, Circuit breaker;
Switchgear : Fuse, MCB, Circuit breaker;
 Load manager for maximum power point tracking;
Load manager for maximum power point tracking;
Verification mechanism: audit security intelligence of solar power technology.
 system performance: verify reliability, consistency, scalability, resiliency, liveness, deadlock freeness, reachability, synchronization, safety;
system performance: verify reliability, consistency, scalability, resiliency, liveness, deadlock freeness, reachability, synchronization, safety;
 multi-party corruption in case of quality problem;
multi-party corruption in case of quality problem;
 access control in R&D: verify authentication, authorization, correct identification, privacy, audit confidentiality, data integrity and non- repudiation;
access control in R&D: verify authentication, authorization, correct identification, privacy, audit confidentiality, data integrity and non- repudiation;
 System design: verify rationality, fairness, correctness, transparency, accountability, trust and commitment;
System design: verify rationality, fairness, correctness, transparency, accountability, trust and commitment;
 malicious attacks: false data injection, shilling: push and pull, denial of service (DoS), fault injection attack;
malicious attacks: false data injection, shilling: push and pull, denial of service (DoS), fault injection attack; call threat analytics and assess risks of emerging solar technology :
call threat analytics and assess risks of emerging solar technology :
 what is corrupted or compromised (agents, technology schema)?.
what is corrupted or compromised (agents, technology schema)?.
 time : what occurred? what is occuring? what will occur? assess probability of occurrence and impact.
time : what occurred? what is occuring? what will occur? assess probability of occurrence and impact.
 insights : how and why did it occur? do cause-effect analysis on performance, sensitivity, trends, exception and alerts.
insights : how and why did it occur? do cause-effect analysis on performance, sensitivity, trends, exception and alerts.
 recommend : what is the next best action?
recommend : what is the next best action?
 predict : what is the best or worst that can happen?
predict : what is the best or worst that can happen?
Output: security intelligence
Prof. Bruno Platini is also presenting the security of solar power system : how to verify the security intelligence of solar power system? It is essential to verify security intelligence of this technological innovation collectively through rational threat analytics at five levels: L1, L2, L3, L4 and L5. The basic building block is an intelligent threat analytics. At level L1, it is required to verify the efficiency of access control in terms of authentication, authorization, correct identification and audit Only asset of authorized entities or agents are able to access the technology of solar power system through authenticated channels. The technical specifications od solar power system and the demand of the clients and consumers should be correctly identified bu the service providers and producers. At level L2, it is essential to evaluate rationality fairness, correctness and transparency of solar power technology management strategy through SWOT analysis, TLC analysis and also technology innovation, adoption and diffusion strategy, At level L3, it is rational to assess the risk of various types of malicious attacks on solar power technology such as fault attack, Denial of Service (DoS), Sybil, false data injection and shilling attacks. The adversaries may execute push and pull attack by other existing power generation and distribution technologies by adopting irrational, incorrect and biased analysis for technology diffusion strategy. An adversary is a malicious agent who attacks solar power system and the associated protocols; the basic objectives are to cause disruption and malfunctioning of a secure system. The security element should be analyzed in terms of the assumptions, goals and capabilities of the adversary. It is also crucial to analyze the adversary model in terms of environment, location, network, resources, access privileges, equipments, devices, actions, results, risks, reasons and motivations of attacks and probable targets. At level L4, it is required to assess the threats of multi-party corruptions on solar power system. The corrupted entities may be trading agents, producers of solar cells and panels, service providers, system administrators and support staff.
Finally, at level L5, it is crucial to audit the solar power system performance in terms of in terms of stability, robustness, reliability, consistency, resiliency, liveness, deadlock freeness, reachability, synchronization and safety. The performance of solar power system and quality of service is expected to be consistent and reliable. Safety indicates that under certain conditions, an event (e.g. electrical faults like overcurrent, overvoltage, short circuit, earth fault, under voltage, over frequency, under frequency) never occurs. Safety is a critical requirement of solar power system system whether it is mechanical, electrical, electronics, information technology, civil or instrumentation engineering. Liveness ensures that under certain conditions an event will ultimately occur. Deadlock freeness indicates that a system can never be in a state in which no progress is possible; this indicates the correctness of solar power system. Another important issue is robustness of a system. The delivery of the output should be guaranteed and the adversary should not be able to threaten a denial of service attack.
Another important issue is the protection of power electronic circuit used in solar power system. The threat analytics analyzes the power electronics circuit from five different perspectives: snubber circuit for high dv/dt and di/dt protection, fuses for fault protection, thermal runaway by heat sinks, reverse recovery transients, supply and load side transients. Voltage transients are caused in converter circuit due to reverse recovery process of power electronic devices and switching actions in the presence of circuit inductance. Short circuit faults may result excessive current flow in power electronic circuit.. Overheating may occur due to losses in semiconductor devices; it must be dissipated sufficiently and effectively for operating the device within upper temperature limit otherwise it may affect the reliability and consistency of power electronic circuit. Fuses are used for overcurrent protection. Power converters may develop short circuit or faults and the resultant fault currents must be cleared quickly. Fast acting fuses are normally used to protect semiconductor devices. As the fault current increases, the fuse opens and clears the fault current in few milliseconds. It is essential to select the location of fuse in the power electronic circuit; generally a fuse is connected in series with each device. A fuse is selected based on the estimation of fault current. A fuse must carry continuously the device rated current; it must be able to withstand voltage after arc extinction; peak arc voltage must be less than peak voltage rating of the device.
Next, let us consider cooling by heat sink. Heat is generated due to on state and switching losses in power electronic devices. The heat must be transferred from the power electronic devices to a cooling medium to maintain junction temperature within specified range. Convection cooling is commonly used in industrial applications. It is rational to consider a set of important design parameters of heat sink such as contact area between device and heat sink, correct mounting pressure of the device on the heat sink, material (e.g. Al), size, and thermal resistance of power devices. Let us consider a power electronic circuit where a voltage source is connected in series with three resistances. Tj = Pa(Rjc+ Rcs+Rsa); Tj : junction temperature, Pa :average power loss, Rjc : resistance from junction to case; Rcs : thermal resistance from case to sink, Rsa : resistance from sink to ambient; Ta : Ambient temperature
It is alos essential to consider the protection through snubber circuit. It limits di/dt and dv/dt; since transients may occur in power electronic circuit. di/dt = IL/tr = ICs/tr; during turn on collector current rises. dv/dt = Vs / tf = Vcc/tf, during turn off, collector emitter voltage must rise in relation to the fall of Ic. Snubber circuit protects the power electronic circuit within allowable limit of di/dt and dv/dt. Inductor Ls limits di/dt; it is a series snubber. RC snubber is normally connected across a semi-conductor device to limit dv/dt within maximum allowable rating. There are three types of snubber circuit : polarized (Resistance R limits forward dv/dt); reverse polarized (Resistance limits discharge current of the capacitor) and unpolarized (semiconductor devices are connected in parallel).
Finally, we consider the risk of transients. There are three types of transients - reverse recovery transients, supply side transients and load side transients. In case of supply side transients, a transformer is normally connected to the input side of converters. Under steady state conditions, an amount of energy is stored in the magnetizing inductance Lm of transformer and switching off the supply produces a transient voltage at the input of the converter. A capacitance C is connected across the secondary of a transformer to limit transient voltage and a resistance is connected in series with C to limit transient voltage oscillation. In case of load side transient voltage, under normal condition, an amount of energy is stored in the supply and leakage inductance of the transformers. When the load is disconnected, transient voltages are produced due to the energy stored in the inductance. In case of reverse recovery transients,
In a circuit, voltage source Vs is connected with an inductance L, capacitance C and resistance R and a diode Dm is connected across C and R. Due to reverse recovery time tr and recovery current Ir, an amount of energy is trapped in the circuit inductance and transient voltage appears across inductance. In addition to dv/dt protection, snubber circuit limits peak transient voltage across inductance. The snubber also limits peak transient voltage across device. The values of snubber circuit R and C are selected so that the circuit is slightly underdamped. The peak reverse voltage depends on damping ratio and current. The energy stored in inductance L is transferred to the snubber capacitance C and is mostly dissipated in snubber resistance. L.di/dt +R.i + (1/C). 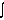 i dt +vc(t=0) = Vs;V= Vs – L.di/dt; i(t=0) =I; vc(t=0)=0
i dt +vc(t=0) = Vs;V= Vs – L.di/dt; i(t=0) =I; vc(t=0)=0
The intelligence in selection of protective system and load monitoring depends on the complexity of system topology, scalability of operation and cost. A standalone solar power system may be protected by a digital relay having features of over voltage, over current, over frequency, under voltage, under frequency, earth fault and short circuit protection. Additionally, the system should be equipped with switchgear devices like fuse, miniature circuit breaker (MCB), earthling system and simple switches. The power electronic circuit should be protected appropriately. Less harmonic should be injected by inverters to avoid heating, thermal losses and damage of consumer electronics and home appliances. Photovoltaic inverters must be able to withstand overloading for short term to take care of higher starting currents from pumps and refrigerators. The other protection issues are related to over/under voltage and frequency, short circuit, surge protection, low idling and no load losses, low battery voltage disconnect and low audio and radio frequency noise. A solar park should be protected by heavy duty equipments such as air circuit breakers (CB), MCCBs, isolators, lightning arresters (LA), power control panels and sophisticated digital relays. The cost of the protection system and load manager is a function of scalability of operation and complexity of the system configuration. Prevention and detection are traditional approaches to the security of power system. In the context of expanding threats and risks, real-time system monitoring is essential to predict new threats and automate routine responses and practices. The system should not only rely on traditional prevent-and-detect perimeter defense strategies and rule based security but should adopt adaptive security through intelligent analytics. Advanced analytics is the basic building block of next generation security protection of solar power system which should be able to manage an enormous volume, velocity and variety of data through AI and machine learning techniques. Intelligent analytics are expected to detect anomalous patterns by comparing with the normal profile and the activities of the users, peer groups and other entities such as devices, applications and smart networks and trigger alarms by sensing single or multiple attacks on the system. The security element must overcome the barriers among security, application development and operations teams and be integrated deeply into system architecture. Next, it is essential to develop effective ways to move towards adaptive security architecture. The mechanism should surfaces anomalies and adjusts individualized security controls proactively in near real-time to protect the critical data of a system. Adaptive Security with dynamic data protection is expected to offer many benefits over traditional security platforms depending on the size complexity of solar power system – real time monitoring of events, users and network traffic; autonomous and dynamic resolutions; prioritization and filtering of security breaches; reduction of attack surface and impact or damage of a threat and reduction of resolution time. The emerging solar power technology is expected to adapt to the needs of a system irrespective of the size of network, nature of operation or exposure of threats. It can assess the requirements of security with greater accuracy through a set of intelligent policies and procedures.
Solar power system may face various types of threats from both external and internal environments but it should be vigilant and protected through a set of security policies. An emerging technology demands the support of an adaptive security architecture so that the associated system can continuously assess and mitigate risks intelligently. Adaptive security is a critical feature of a technology that monitors the network or grid associated with a system in real time to detect any anomalies, vulnerabilities or malicious traffic congestion. If a threat is detected, the technology should be able to mitigate the risks through a set of preventive, detective, retrospective and predictive capabilities and measures. Adaptive security analyzes the behaviors and events of the solar power system to protect against and adapt to specific threats before the occurrence of known or unknown types of malicious attacks. Let us explain the objectives of adaptive security in depth. New threats are getting originated as an outcome of solar technology innovation and may cause new forms of disruptions with severe impact. The system demands continuous monitoring and remediation; traditional ‘prevent and detect’ and incident response mindsets may be not sufficient to prevent a set of malicious attacks. It is required to assess as-is system administration strategies, investment and competencies; identify the gaps and deficiencies and adopt a continuous, contextual and coordinated approach.