3. STRUCTURE
Structure Analytics
Dr. Aziz is analyzing the structure of the systems associated with emerging digital technologies. There are various types of deployment models in cloud computing such as private cloud, public cloud and hybrid cloud. Private cloud is operated solely for a single organization managed internally or by a third party and hosted internally or externally. Public cloud offers a set of services over a network that is open for public use. Hybrid cloud offers the benefits of public and private cloud. In cloud architecture, multiple cloud components communicate with each other over a loose coupling mechanism (e.g. messaging queue). Cloud computing service models are arranged as layers in a stack : Infrastructure-as- a-Service (IaaS), Platform-as- a-Service (PaaS), Software-as-a-Service (SaaS), Database-as-a-Service (DaaS), Datastorage-as-a-Service (dSaaS), Mobile-backend-as-a-Service (MBaaS), serverless computing and Function-as-a-Service (FaaS) [1-20].
IaaS provides online services of network infrastructure such as physical computing resources, location, data partitioning, scaling, security and backup from data centers. PaaS offers a development environment to application developers through programming languages, libraries, services and various tools. The service consumer does not manage or control the underlying cloud infrastructure (e.g. network, servers, operating systems or data storage) but has control over deployed applications and possibly configuration settings for the application hosting environment. SaaS permits a service consumer to use the software applications of the service provider running on a cloud infrastructure. The applications are accessible from various client devices through web browser or a program interface. The consumer does not manage or control the underlying cloud infrastructure but can access to application software and databases. Cloud providers manage the infrastructure and platforms that run the applications. MBaaS permits web app and mobile app developers linking their applications to cloud storage and cloud computing services through application programming interfaces (APIs). Serverless computing permits cloud provider fully manageing starting and stopping virtual machines. FaaS is a service hosted remote procedure call that leverages serverless computing to enable the deployment of individual functions in the cloud that run in response to events.
IIoT: IoT is the network of physical objects embedded with sensors, software and network connectivity that enables the objects to monitor, collect, exchange and analyze data. Industrial Internet of Things (IIoT) is a set of hardware and software components (e.g. smart sensors and actuators) enabled by IoT to support manufacturing and industrial processes. IIoT leverages the power of smart machines and real-time analytics across several industries such as manufacturing (Industry 4.0), logistics, oil, gas, transportation, energy, utilities, mining, metals and aviation. The benefits of IIoT may include better connectivity, scalability, cost savings, improved productivity and better analytics for predictive maintenance.
Pervasive & wearable computing : One of the most promising emerging digital technology is health monitoring smart wearable systems (SWS) through advances of micro-electro-mechanical systems, electrical simulation, mechatronics, sensors, actuators, biomedical instrumentation and nanotechnology. SWS is an interesting cost-effective solution which can monitor a patient’s health status in real-time and support complex healthcare applications for disease prevention, symptom detection and medical diagnosis. Let us consider the structure of smart wearable system (SWS). The system may have various types of digital and mechatronics components such as sensors, actuators, power supplies, wireless communication units, processing units, algorithms, software, user interfaces and smart fabrics to capture and process data and make intelligent decisions based on the measurement of various parameters of human body such as temperature, blood pressure, heart rate, respiration rate, blood oxygen saturation and ECG. The measured data are sent to a central node (e.g. PDA, medical centre) through wireless communication system. SWS is expected to monitor the state of the health of human agents (e.g. patients, athletes, issue alerts and send feedback to the medical staff in real-time. The healthcare experts and consultants can take rational decisions on patient care accordingly. There are various issues and challenges in telecare, telehealth and telemedicine through new models, prototypes, test beds and industrial products to enhance the performance of healthcare system and minimize the risk of illness, injury, inconvenience and rehabilitation. But, there are various constraints such as high cost, size, weight, energy consumption, complexity of sensor implementation and connectivity, ethics, laws, information security and privacy, freedom, autonomy, reliability, consistency, safety and service issues.
Edge computing needs the support of a distributed and open IT architecture having decentralized processing power, mobile computing and IoT technologies. Data is processed by the device itself or by a local computer or server, rather than being transmitted to a data center. Edge structure consists of servers, applications, content distribution network and small clouds at the edge. An edge gateway is a virtual router in either a compact or a full configuration. Edge devices are used by enterprises and service providers through cloud computing and IoT technologies for more intelligence, computing power and advanced services at the network edge. Edge structure uses cloud infrastructure but keeps assets at the edge of the network. A version of the client's apps may run locally to allow ready use without latency, with another versions residing in the regional and central data centers for data warehousing and mining.
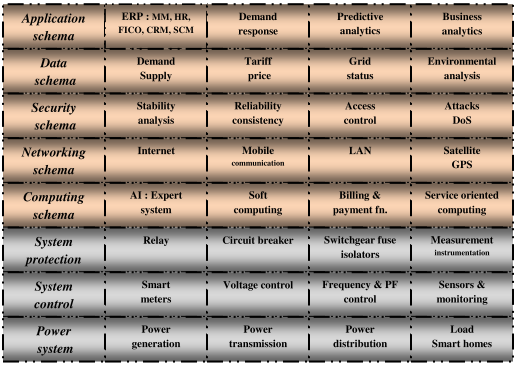
Figure 10.3 : Information System Structure for Solar Computing
Dr. Aziz is analyzing a smart grid in terms of various system components such as power generation, transmission and distribution system, generators, transformers, transmission lines, loads, switchyards, microgrids comprising of AC/DC sources and loads, renewable energy sources and energy storage system. Figure 10.3 shows the layered structure of a smart power grid having two core layers: (a) physical and (b) information. The physical layer consists of bottom three layers. The first layer connects various components of a power system such as power generation, transmission, distribution and loads. The next layer is system control which consists of smart meters, voltage, frequency and power factor controllers, sensors and monitoring instruments. Smart meters are able to support exchange of real-time information on demand and supply of electrical power from a smart grid. The meter reading may be communicated to the consumers through SMS and e-mail. The third layer protects the smart grid through various types of relays, circuit breakers, switchgears, fuses and isolators.
The next layer of the smart grid structure is information layer which is associated with computing, networking, security, data and application schema. This layer aggregates information from the physical layer and analyzes data intelligently. The computing schema uses knowledge based expert system and various soft computing tools for automated system control of the smart grid. It is also necessary to compute bills or invoices for the consumers based on consumption of energy; The basic building blocks of networking schema are internet and mobile communication systems. The data schema manages data on demand and supply, tariff and pricing plans. The application schema has various components such as ERP, SCM, CRM, DSS and business analytics; the ERP system may have materials management, finance and cost control, HR and maintenance modules.
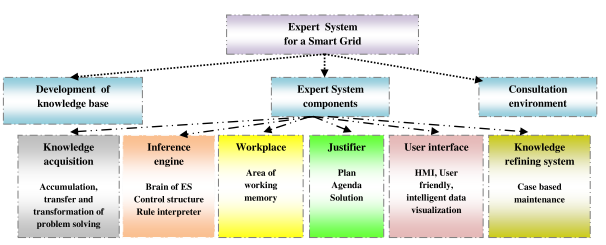
Figure 10.4 Expert System for a Smart Grid
The solar computing system should be able to interact with the consumers on various issues such as demand response schemes, current energy sources, information on availability of power, peak load, energy consumption, payments, discounts, variable pricing mechanisms and charging of electrical and hybrid vehicles. The objective of demand response schemes is to accommodate variable supply of renewable energy sources and high frequency monitoring of demand and supply for smart homes, buildings and micro-grids. Solar computing considers the scope of various types of emerging applications such as internet of energy, smart homes and autonomous micro-grids to manage and monitor the use, storage and production of electrical energy though a network of automated modules.
Expert systems are computer based information systems that use expert knowledge to attain high level decisions performance in a specific problem domain [Figure 10.4]. The basic principles of ES include how to determine who experts are, the definition of expertise, how expertise can be transferred from an agent to a computer, how the system works. An expert is an agent who has special knowledge, judgement, experience and methods to give advice and solve problems. The knowledge is basically a set of facts and rules. An ES is expected to recognize and formulate a problem, solve a problem quickly and correctly, explain a solution, learn from experience, restructure knowledge, breaking rules if necessary, determining relevance and degrading gracefully. Expertise is extensive task specific knowledge that use expert process. The level of expertise determines the performance of a decision. Expertise is obtained in various ways ; implicit knowledge is gained from experience; explicit knowledge is gained through supervised learning. Expertise is associated with high degree of intelligence, learning from past success and mistakes, well stored, organized and quickly retrievable knowledge from an expert who has excellent recall of patterns from previous experience. The knowledge is related to a specific problem domain, rules and procedures, heuristics about what to do in a given problem situation, global strategies for solving a problem, meta knowledge (knowledge about knowledge) and facts about problem areas.
Dr. Aziz is presenting the complexity analysis on the structure of IIoT enabled ICS and SCADA technology in terms of various components such as PLC, RTU, field devices, intelligent electrical and electronic devices, workstations, human machine interface, communication gateways, data historians, controllers and software applications; their functions, topology, connectivity and communication protocols. The configuration and scope of an ICS may be simple, medium or highly complex; may be fully or semi-automated. There are various types of ICS like SCADA, process control system (PCS), distributed control system (DCS), safety (SIS), building automation system (BAS), energy management system (EMS) and embedded system (ES).
A Process Control System (PCS) controls an automation process in an industrial plant (e.g. steel, chemical, life-science). SIS monitors an automation process and prevents an unsafe plant operation through a set of sensors and controllers. DCS controls multiple automation processes at a plant (e.g. oil refineries, water treatment plant). BAS monitors and controls a building’s infrastructure services such as heating, ventilation, air conditioning, cooling, lighting, elevators, fire protection, energy management etc. through intelligent Internet Protocol (IP). EMS monitors and controls a smart power grid.
SCADA is a type of ICS which collects data and monitors an automated power plant. SCADA control center monitors and manages RTUs and IEDs; the human operators or supervisors use HMI or a supervisory control software to control the power plant by changing set points. A SCADA system may supervise one or more DCSs or PCSs at distant locations, through intelligent communication protocols wherein bandwidth, reliability, latency and jitter are critical success factors. A SCADA system is a process automation system; it is used to gather data from the sensors and the instruments distributed at remote sites and to transmit the data into a central system for controlling or monitoring the basic mechanism. The system controller can view the data collected from the sensors on SCADA host computers located at master site. Automated or operator driven supervisory commands are transmitted to the control system based on the data received from the remote sensors.
Generally, a SCADA system is composed of five basic components [1]: (i) a sensor network that senses process variables at remote site, (ii) a set of operating instruments connected to the sensors, (iii) a set of local processors that collect data and communicate with programmable logic controllers (PLC), RTU, intelligent electronic devices (IED), transducers, relays and process controllers; (iv) SCADA servers / host computers / master terminal units (MTU) as central point of process control, performance monitoring, data warehousing and data mining and (v) wired / wireless communication channels between local processors and host computers.
Let us do the technical analysis on various components of an industrial control system &/ SCADA. A PLC is a microprocessor controlled electronic device that reads input data from sensors, executes programmed instructions based on input and supervisory control, generate output signals for change of switch settings or actuators. A PLC has CPU, communication interface, input and output modules and power supply and executes various types of programming languages such as ladder diagram, block diagram, structured text, instruction list and sequential function chart. A RTU is a microprocessor controlled electronic device and of two types such as station and field RTUs. Intelligent Electronic Devices (IED) may have one or more processors and can interact with various external entities like digital relays and meters.
A workstation is typically a computer or server running a standard operating system; hosts the programming software for making changes in the logic of the controllers and other applications. HMI is a software application which provides alarms, process status and data trends of an automated processes to a plant supervisor. An HMI can operate on various platforms such as desktop computers, tablets, smart phones or SCADA panel screens. Data Historian is a software application for time series analysis of real-time data. Communication Gateway enables two devices to communicate with each other. A Front End Processor is a dedicated communications processor. There may be various types of field devices like sensors, transducers and actuators which directly interface with a controller through digital or analog I/O module or industrial protocol (e.g. Modbus). The typical architecture of SCADA supports TCP, IP, UDP and wireless communication protocols as well as Modbus TCP, private radio, cellular or satellite networks [6]. The selection of appropriate communication schema depends on various factors such as data rate, polling frequency, distance, area, budget and future needs. A SCADA system can monitor and control thousands of input / output (I/O) points. This is a complex integrated system: a SCADA network may be integrated with other different types of information and communication systems such as web enabled enterprise applications and business intelligence solutions [3,4]. This architecture provides a real-time, fault-tolerant and intelligent distributed computing platform.
Let us do system audit analysis on digital transformation of ICS / SCADA [ Figure 10.5]. In many plants, ICS and SCADA were installed a long time back. It is possible to improve the system performance and productivity of various old plants through system audit grid analysis : divest the dead, old and obsolete technologies (e.g. electromagnetic relays, PLCs) and invest on emerging technologies (e.g. digital relay protection, sensor networks, Internet communication protocols, self healing system, AI based plant) for digital transformation.
What are the benefits of deploying wireless communication schema in ICS and SCADA? It is a costly strategic option; it requires high capital allocation and technological skill for the replacement of wired networking schema with wireless schema and extensive upgrading efforts. This initiative of digital transformation also requires the replacement of critical electrical and electronic equipments such as digital relays, digital smart meters and sensors which should be fit for operation in wireless environment. It is also important to look into security and privacy of critical data in wireless environment against malicious cyber and physical attacks. It is really challenging to select appropriate wireless technologies for multi-tiered ICS & SCADA architecture. A typical wired ICS infrastructure may be damaged due to natural disaster or act of terrorism. However, there are several benefits of wireless schema in terms of network bandwidth, high speed, reliability, adaptability, availability, safety, scalability, reduced cost of cabling and installation, flexible installation, adhoc ondemand deployment, providing redundancy and efficient integration among different components of plant.
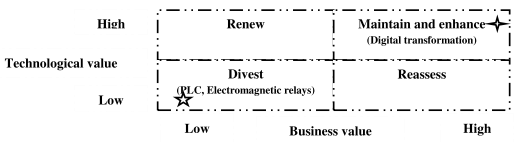
Figure 10.5 : System Audit Grid for IIoT enabled SCADA / ICS
Let us explore the structure of quantum computing model in terms of quantum bits, quantum gates, quantum algorithms and quantum circuit. What are the basic elements of secure multi-party quantum computing model : computing schema, data schema, networking schema and application schema?
Quantum bits: A bit is the fundamental building block of classical computation and information. Secure Multi-party Quantum Computation (SMQC) is built upon an analogous concept quantum bit or qubit. Qubit is a mathematical object with specific properties. Qubits are abstract mathematical objects to construct a general theory of SMQC. A bit has two possible states – 0 and 1. Like classical bit, qubit has two possible states |0 and |1
and |1 where |
where | is Diract notation. The difference between bits and qubits is that a qubit can be in a state other than |0
is Diract notation. The difference between bits and qubits is that a qubit can be in a state other than |0 and |1
and |1 . It is also possible to form linear combination of states known as superposition. |
. It is also possible to form linear combination of states known as superposition. |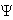
 =
= 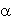 .|0
.|0 +
+
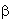 .|1
.|1 ; where
; where 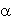 and
and 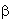 are complex numbers. The state of Qubit is a vector in 2- dimensional complex vector space. The special states |0
are complex numbers. The state of Qubit is a vector in 2- dimensional complex vector space. The special states |0 and |1
and |1 . are known as computational basis states and form a orthogonal basis for vector space. In classical computation, a bit is examined whether it is in a state 0 or 1. We can not examine a qubit to determine its quantum state i.e. the values of
. are known as computational basis states and form a orthogonal basis for vector space. In classical computation, a bit is examined whether it is in a state 0 or 1. We can not examine a qubit to determine its quantum state i.e. the values of 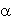 and
and 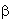 . We can only acquire much more restricted information about the quantum state. When we measure Qubit, we get either the result 0 with probability
. We can only acquire much more restricted information about the quantum state. When we measure Qubit, we get either the result 0 with probability 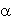 2 or result 1 with probability
2 or result 1 with probability 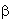 2. In general, a qubit’s state is a unit vector in 2D cvomplex vector space. Another important issue is multiple qubits : if there are two bits, there will be four possible states – 00,01,10 and 11. If there are 2 qubits, there will be 4 computational basis states |00
2. In general, a qubit’s state is a unit vector in 2D cvomplex vector space. Another important issue is multiple qubits : if there are two bits, there will be four possible states – 00,01,10 and 11. If there are 2 qubits, there will be 4 computational basis states |00 , |01
, |01 . |10
. |10 and |11
and |11 . The state vector describing 2 qubits is |
. The state vector describing 2 qubits is |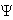
 =
= 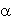 00.|00
00.|00 +
+ 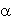 01.|01
01.|01
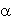 10.|10
10.|10
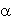 11.|11
11.|11 .
.
Quantum computation : A classical computer is built from an electrical circuit containing wires and logic gates. A quantum computer is built from a quantum circuit and elementary quantum gfates to execute secure multi-party quantum computation. Let a system has two states |0 and |1
and |1 . Then quantum NOT gate :
. Then quantum NOT gate :
|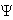 ’
’ =
= 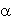 .|1
.|1 +
+ 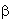 .|0
.|0 .
.
Quantum NOT gate , X = [0, 1; 1, 0]; Quantum state 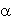 .|0
.|0 +
+ 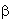 .|1
.|1 = [
= [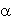 ,
, 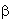 ]; X. [
]; X. [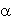
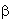 ]
]
= [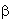 ,
, 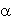 ]
]
Z 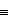 [1 0;0 -1], H = 1 / root 2 [1, 1; 1, -1]
[1 0;0 -1], H = 1 / root 2 [1, 1; 1, -1]
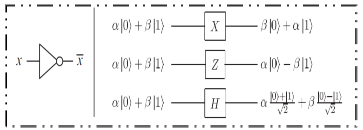
Figure 10.6 : Qubit logic gates (a)NOT gate, (b) Z gate; (c) H gate
There are various types of quantum gates such as AND, NAND,OR,NOR,XOR, Z gate and H gate; H gate reprents Hadamand operation, a rotation of a space about y axis by 900 followed by a rotation of X axis by 1800.
Quantum circuit : It is made of quantum gates and wire. Let a circuit swaps the states of two qubits.
|a,b
 |a, a
|a, a b
b ; |a
; |a (a
(a b), a
b), a b
b = |b, a
= |b, a b
b ; |b
; |b (a
(a b)
b)  b
b = |b,a
= |b,a

Figure 10.7 : Qubit circuit swapping 2 qubits
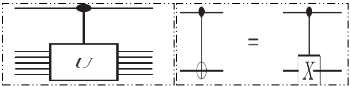
Figure 10.8 : Controlled U gate and NOT gate
Quantum algorithms : What class of computation can be performed using quantum circuit? How to compute SMQC with computation using classical logic circuits ?
Toffoli gate : It has 3 input bits and 3 output bits. It is a reversible gate. Two bits are controlled bits that are unaffected by the action of Toffoli gate. The third bit is a target bit that is flipped if both control bits are set to 1 and otherwise left alone.
(a, b, c)  (a,b, c
(a,b, c a.b)
a.b)  (a, b, c)
(a, b, c)
Truuth table of Toffoli gate :
Input - [0,0,0;0,0,1;0,1,0;0,1,1;1,0,0;1,0,1;1,1,0;1,1,1];
Output – [0,0,0;0,0,1;0,1,0;0,1,1;1,0,0;1,0,1;1,1,1;1,1,0];
Quantum parallelism : It is a fundamental feature of many quantum algorithms. It allows quantum computers to evaluate a function f(x) for any different values of x simultaneously.
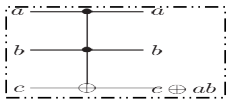
Figure 10.9: Tofolli gate
Structure Analytics
 Bloom filter
Bloom filter
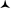 Adaptive Bloom Filter /
Adaptive Bloom Filter /
 Cuckoo filter
Cuckoo filter
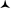 Adaptive Cuckoo Filter /
Adaptive Cuckoo Filter /
 Parallel pipeline
Parallel pipeline
Data structure is the basic building block of efficient algorithms. It is used to organize a large amount of data which can be queried efficiently. Randomized data structure assumes that inputs and queries are independent of its internal randomness. For any sequence of inputs, an efficient data structure yields a correct answer with high probability ove








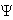
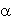







 Adaptive Bloom Filter
Adaptive Bloom Filter