4. SECURITY
Security Analytics
Prof. Kamal Kumar, Prof. Simon Watson and Dr. Henry Plank are analyzing the security intelligence of emerging digital technologies. An information system (IS) may face various types of threats from both external and internal environments but it should be vigilant and protected through a set of security policies. Emerging digital technologies demand the support of adaptive security architecture so that the associated information systems can continuously assess and mitigate risks intelligently. Adaptive security is a critical feature of an emerging digital technology that monitors IS in real-time to detect any anomalies, vulnerabilities or malicious traffic congestion. If a threat is detected, IS should be able to mitigate the risks through a set of preventive, detective, retrospective and predictive capabilities and measures. Adaptive security analyzes the behaviors and events of an information system to protect against and adapt to specific threats before the occurrence of known or unknown types of malicious attacks.
The basic objective of emerging adaptive security architecture and dynamic data protection mechanism is to assess and mitigate the risks of enterprise information system rationally and intelligently. What constitutes an effective strategy of IS security schema? It is debatable whether the proactive approach to IS security is superior to reactive approach. It is possible to recommend an interesting strategy: reactive security may be competitive with proactive security as long as the reactive approach learns from past attacks instead of overreacting to the last attack on the information system. It is not a trivial problem and needs the support of an efficient security protocol from intelligent threat analytics and adaptive security architecture. The following section presents the construction of an adaptive security algorithm to ensure the security of an information system based on proactive and reactive approaches. The basic building blocks of the algorithm are intelligent threat analytics, cryptographic solutions and dynamic data protection. It is basically an attempt of the cross fertilization of algorithmic game theory and cryptography. It is essential to verify the security intelligence of a smart grid at various levels : L1, L2, L3, L4 and L5. At level L1, the system performance of the grid is verified in terms of reliability, consistency, stability, robustness, safety, liveness and resiliency. Resiliency measures how fast a system can return to the normal operation following a disruption. The other critical factors are deadlock-freeness and synchronization.
The next level is L2 wherein it is required to audit the access control policy of the grid in terms of authentication, authorization, correct identification, privacy, confidentiality, commitment and trust of the users and the system administrator. At level L3, the security schema is verified in terms of fairness and correctness (e.g. accuracy of measurement of data in meter reading). At level L5, it is crucial to assess the risks of various types of malicious attacks on a smart grid such as denial of service (DoS), Sybil and false data injection attack.
At level L4. it is essential to verify the efficiency of digital relay protection of the transmission lines, generators and motors connected to the power grid such as overcurrent, earth fault, short circuit, voltage and reactive power control and distance protection. Digital relays protect the power system from the adverse effects of a fault which occurs as a random event. The fault current is always greater than the normal load current. If the faulty power system component is not isolated from the grid in time, it may lead to instability. A protection system may consist of CT / PT, CVT, battery, circuit breaker, transducers and protection relays. Overcurrent relays can be used to protect transmission lines, transformers, generators and motors. Reliability and consistency are expected in power system protection. A relay must be dependable and secure; it should operate for specific operating conditions; it should not operate for any other power system disturbance. The responsibility and accountability is defined by a zone of protection. A protection system is responsible for all types of faults occurring within the zone of protection.
Let us present the SWOT analysis on digital power system protection. Smart power grid protection is going through a diffusion of technology from electromagnetic and static relays towards computer enabled digital relays; digital computers have been replacing traditional tools used for short circuit, load flow and stability analysis. Power system protection relays are the next promising scope of computerization based on improved computer hardware, efficient algorithms and programming codes. Digital relays offer the best economic and technical solutions for real-time monitoring and control of power systems today.
Digital relay protection provides several benefits in terms of cost, self-checking reliability, consistency, system integration, adaptive relaying and functional flexibility. The cost of a relay is the main consideration in its acceptability. The cost of digital relays has been declining steadily; the cost of conventional electromagnetic and static relays has been increasing due to change in design, inflation and declining sales and production. A digital relay can be programmed to monitor its hardware and software schema continuously and can detect any malfunctions. It fails in a safe mode and sends a service request alarm to the system center. Digital computers and digital technology have become the basis of measurements, communication, and control of a smart grid. Digital relays can accept digital signals from transducers and fiber optic channels and can be integrated with the control and monitoring system efficiently. Digital computer can be programmed to perform several functions such as measuring and monitoring flows and voltages in transformers and transmission lines, controlling the opening and closing of circuit breakers and switches and providing necessary backup. The relaying function calls for intensive computational activity at no extra cost when a fault occurs on the system. It is an interesting innovation agenda how AI algorithms, heuristics and computing techniques can be applied in various roles of digital power system protection: (Level A) relaying, switch yard protection, measurements, control, diagnostics, communication with levels B and C; (Level B) man machine interface, data acquisition and storage, sequence of events analyses, coordination, back-up protection, communication with level A and B and (Level C) system control, event analyses, communication with levels A & B, adaptive relaying and system performance analysis.
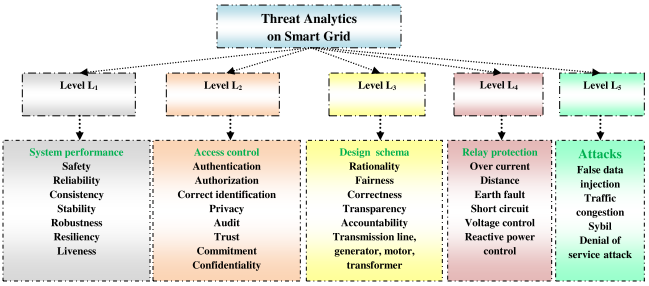
Figure 10.11: Threat Analytics of a Smart Grid
Adaptive security and dynamic data protection : Let us consider the technology associated with adaptive security and dynamic data protection of a smart grid operated through solar computing. New threats are getting originated as an outcome of technology innovation and may cause new forms of disruptions with severe impact. Today, it is essential to deploy adaptive security architecture for solar computing. A smart grid demands continuous monitoring and remediation; traditional ‘prevent and detect’ and incident response mindsets may be not sufficient to prevent a set of malicious attacks. Adaptive security is an essential part of solar computing. It is required to assess as-is system administration strategies, investment and competencies; identify the gaps and deficiencies and adopt a continuous, contextual and coordinated approach.
For example, prevention and detection are traditional approaches to the security of a smart grid. In today’s digital world of expanding threats and risks, real-time system monitoring is essential to predict new threats and automate routine responses and practices. Advanced analytics is the basic building block of next generation security protection which should be to manage an enormous volume, velocity and variety of data through AI and machine learning techniques. User Entity Behavior Analytics detect anomalous patterns by comparing with the normal profile and the activities of the users and trigger alarms by sensing single or multiple attacks on solar computing system. The security must overcome the interorganizational barriers among security, application development and operations teams and be integrated deeply into solar computing architecture.
Dynamic data protection is an effective way to move towards adaptive security architecture. DDP surfaces anomalies and adjusts individualized data security controls proactively in near real-time to protect the critical data of an enterprise. Adaptive Security with dynamic data protection is expected to offer many benefits over traditional security platforms depending on the size of organization and networking schema – real time monitoring of events, users and network traffic; autonomous and dynamic resolutions; prioritization and filtering of security breaches; reduction of attack surface and impact or damage of a threat and reduction of resolution time. This technology is expected to adapt to the needs of solar computing system irrespective of the size of network, nature of operation or exposure of threats. It can assess the requirements of information security with greater accuracy through a set of intelligent policies and procedures and can ensure better understanding of strength, weakness, opportunities and threats of the security architecture.
A system may face various types of threats from both external and internal environments but it should be vigilant and protected through a set of security policies. An emerging technology demands the support of an adaptive security architecture so that the associated system can continuously assess and mitigate risks intelligently. Adaptive security is a critical feature of a technology that monitors the network or grid associated with a system in real time to detect any anomalies, vulnerabilities or malicious traffic congestion. If a threat is detected, the technology should be able to mitigate the risks through a set of preventive, detective, retrospective and predictive capabilities and measures. Adaptive security analyzes the behaviors and events of a system to protect against and adapt to specific threats before the occurrence of known or unknown types of malicious attacks. Adaptive security monitors a solar computing system in real time to detect anomalies, malicious traffic and vulnerabilities. If a threat is detected, it is essential to counter the threat in various ways. Preventive capabilities allow the system to create products, processes, and policies that counter-attack malicious attack (e.g. web security) on the solar computing system. The detective capabilities should identify those attacks in time at minimum impact and not detected by preventative capabilities. Retrospective capabilities should perform in-depth analysis of threats not detected by the detective layer to avoid such types of attacks in future. Predictive capabilities provide alerts about external events and anticipates new types of threats.
Abnormal operating conditions and faults may cost a smart grid significantly but may be prevented through intelligent prediction and control mechanism of knowledge based expert system. An expert system is expected to monitor, detect and diagnose abnormal conditions of solar power system and provides safeguards against unexpected process conditions. It is possible to model faults and instability in a complex smart grid through expert system which is basically a knowledge based real-time fault diagnostics. The expert system uses the valuable knowledge from the experts, operators and real-time data from various sensors, measuring instruments and various electrical and electronic devices connected to a smart grid. Soft computing algorithms (e.g. fuzzy logic and ANN) may be used for mining acquired real time data and knowledge discovery from data.
There are two methods of fault diagnosis : model based approach and knowledge based approach. Model based approach adopts quantitative models to estimate states and parameters of system. But, it is almost impossible to obtain a model that exactly matches the process behavior of a smart grid in practice. The mismatch between the behavior of the model and the plant or smart grid may lead to large error signals. Abnormal operation may cause false alarms unless appropriate thresholds are used. It may be impossible to model non-linear systems by analytical equations. These negative aspects demand the support of alternative knowledge based methods in fault diagnosis such as ANN, fuzzy logic and CBR. Knowledge based fault diagnosis is done based on the evaluation of real-time monitored data according to a set of rules which human experts (e.g. operators, engineers, support staff) have learnt from past experience. The knowledge may be input and output process variables, patterns of abnormal process conditions, fault symptoms, operational constraints and performance criteria. Knowledge based approach automates human intelligence for smart grid supervision. Knowledge based approach is suitable for large and complex, nonlinear smart grid. Linear approximation of nonlinear system may result significant errors. The combined approach of knowledge based fault diagnosis with real-time process variables improves the reliability, consistency and efficiency of the system. Knowledge based fault diagnosis has three basic steps: (a) acquire real time process data from sensors and intelligent electrical and electronic devices; the sensed process variables indicate problem of safety and stability of smart solar grid. (b) make inferences or diagnosis based on acquired process data and (c) take actions based on inferences such as raising alarms, informing operators and automated on/off operation of connected equipments for resiliency of the smart grid. Please refer to section 9 which has analyzed the case of a self- healing smart grid through verification of security intelligence at levels L1,L2,L3,L4 and L5.
The next element of the deep analytics is security. The basic building block of security of IIoT enabled ICS and SCADA technology is an intelligent threat analytics. The threats to a plant may be method, target, protocol and identity specific. Insider attacks are more malicious than outsider attacks as the adversaries may have more knowledge about the internal architecture of SCADA & ICS. Method specific threats define how active or passive threats are executed. The method specific threats can be either passive or active. In passive attack, the adversary monitors and analyzes the data captured from SCADA & ICS. In active method, the adversary may send false data to the components of SCADA system.. Target specific threats attack specific component of SCADA network such as PLC, relays and smart meters. The adversaries may try to exploit the vulnerabilities associated with the networking protocols (e.g. DNP3, Modbus).
Please refer to section 9 which outlines security intelligence verification mechanism (SIVM) and also shows its application in three different cases: (a) SCADA for a smart power grid, (b) adaptive industrial control system and (c) defense for border security surveillance. SIVM is the backbone of the security of IIoT enabled SCADA and ICS technology. Table 4.1 summarizes the major findings of an intelligent threat analytics for the protection of SCADA & ICS in terms of target, risks assessment and mitigation strategies and verification mechanisms. A verification mechanism is expected to provide one or more services by detecting, preventing or recovering from one or more security attacks. We have found that no single verification algorithm can provide adequate security to ICS & SCADA.
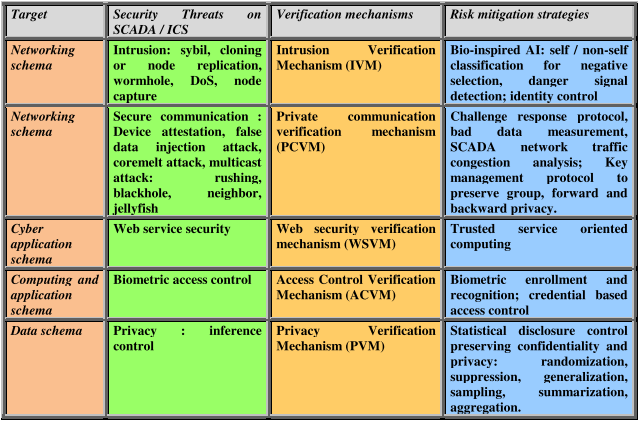
Table 10.1: Threat Analytics
An intelligent threat analytics should perform various type of vulnerabilities analysis as follows :
Vulnerability analysis 1: Domain (configuration, design specification, implememtation) vs. weakness (account mgmt, poor coding practice, poor authentication, interface programmimg, malfunctioning devices, poor logging, inefficient monitoring);
Vulnerability analysis 2 : Risk elements ( purpose of attacks [ information capture, sabotage], lateral movement [ automatic], location command and control server [Insider and outsider attack], initial attack vector [Automatic]) vs. types of attacks (e.g. capture information from target through industrial espionage, identity theft, IP theft, spearphishing, drive-by-download attack);
Vulnerability analysis 3 : Classification of vulnerabilities (buffer outflow, forced browsing, code injection, access control, input validation, resource exhaustion, authentication attack, path traversal, resource allocation, weak password, DLL hijacking, SQL injection, cryptographic failure, CSRF, weak encryption) vs. history of occurence;
Vulnerability analysis 4 : metrics (physical, information, cognitive, social) vs. risk mitigation practice (plan, absorb, recover, adapt);
It is essential to define an optimal set of security metrics in terms of risk and resilience. The metrics are the measurable properties of ICS that quantify the degree to which objectives have been achieved and provide vital information of system performance. Security metrics are associated with critical business functions such as incident, vulnerability, patch, configuration, security and change management. The metrics should be linked to a strategy, can be quantified, comprehensive, and measurable and indicates the right behavior of a system. Relevant Metrics are directly linked to decision making goals, objectives and relevant attributes of a system.
Adaptive security and dynamic data protection
The expert panel are interaction on the technology associated with adaptive security and dynamic data protection of ISI analytics. New threats are getting originated as an outcome of technology innovation and may cause new forms of disruptions with severe impact. Today, it is essential to deploy adaptive security architecture for SCADA & ICS which demands continuous monitoring and remediation; traditional ‘prevent and detect’ and incident response mindsets may be not sufficient to prevent a set of malicious attacks. Adaptive security is an essential part of ISI analytics. It is required to assess as-is system administration strategies, investment and competencies; identify the gaps and deficiencies and adopt a continuous, contextual and coordinated approach.
For example, prevention and detection are traditional approaches to the security of SCADA & ICS. In today’s digital world of expanding threats and risks, real-time system monitoring is essential to predict new threats and automate routine responses and practices. Advanced analytics is the basic building block of next generation security protection which should be to manage an enormous volume, velocity and variety of data through AI and machine learning techniques. User Entity Behavior Analytics detect anomalous patterns by comparing with the normal profile and the activities of the users and trigger alarms by sensing single or multiple attacks on SCADA & ICS. The security must overcome the inter- organizational barriers among security, application development and operations teams and be integrated deeply into ISI analytics architecture.
Dynamic data protection is an effective way to move towards adaptive security architecture. DDP surfaces anomalies and adjusts individualized data security controls proactively in near real-time to protect the critical data of an enterprise. Adaptive Security with dynamic data protection is expected to offer many benefits over traditional security platforms depending on the size of organization and networking schema: real time monitoring of events, users and network traffic, autonomous and dynamic resolutions, prioritization and filtering of security breaches, reduction of attack surface and impact or damage of a threat and reduction of resolution time. This technology is expected to adapt to the needs of ISI analytics irrespective of the size of network, nature of operation or exposure of threats. It can assess the requirements of information security with greater accuracy through a set of intelligent policies and procedures and can ensure better understanding of strength, weakness, opportunities and threats of security architecture.
A system may face various types of threats from both external and internal environments but it should be vigilant and protected through a set of security policies. An emerging technology demands the support of an adaptive security architecture so that the associated system can continuously assess and mitigate risks intelligently. Adaptive security is a critical feature of a technology that monitors the network or grid associated with a system in real-time to detect any anomalies, vulnerabilities or malicious traffic congestion. If a threat is detected, the technology should be able to mitigate the risks through a set of preventive, detective, retrospective and predictive capabilities and measures. Adaptive security analyzes the behaviors and events of a system to protect against and adapt to specific threats before the occurrence of known or unknown types of malicious attacks. Adaptive security feature of ISI analytics monitors SCADA & ICS in real-time to detect anomalies, malicious traffic and vulnerabilities. If a threat is detected, it is essential to counter the threat in various ways. Preventative capabilities allow enterprises to create products, processes, and policies that counter-attack malicious attack (e.g. web security) on SCADA &/ ICS. The detective capabilities should identify those attacks in time at minimum impact and not detected by preventative capabilities. Retrospective capabilities should perform in-depth analysis of threats not detected by the detective layer to avoid such types of attacks in future. Predictive capabilities provide alerts about external events and anticipates new types of threats.
Adaptive Security Algorithm [ASA]
Agents: Defender (e.g. system administrator), Attacker (e.g. malicious agent or adversary);
System : Enterprise information system;
Objectives: optimize enterprise IS security investment;
Constraints: budget, resources, time;
Input: Enterprise information system performance parameters and architecture;
Strategic moves:
 Adaptive security
Adaptive security
 Dynamic data protection
Dynamic data protection
 Self-healing mechanism
Self-healing mechanism
 Crash proof code
Crash proof code
 Real-time fault diagnostics
Real-time fault diagnostics
 Adoption of hybrid strategy i.e. an optimal mix of proactive and reactive approaches.
Adoption of hybrid strategy i.e. an optimal mix of proactive and reactive approaches.
Revelation principle: The agents preserve privacy of strategic data;
 Defender : The defender does not disclose the proactive and reactive approach of information security to the adversaries.
Defender : The defender does not disclose the proactive and reactive approach of information security to the adversaries.
 Attacker : The adversaries preserve the privacy of the plan of malicious attack, information of targets and weak links.
Attacker : The adversaries preserve the privacy of the plan of malicious attack, information of targets and weak links.
 Security intelligence verification: Proactive approach:
Security intelligence verification: Proactive approach:
-
- Threat modeling
-
- Call threat analytics function (fa);
- Estimate probability (p) of occurrence along two dimensions : Low [L] and High [H];
- Estimate impact of risk i.e. sunk cost (c) along two dimensions : [L,H];
- Map threats into a set of risk profiles or classes : LL, LH,HL and HH;
- Estimate security requirements in terms of demand plan (Pd);
- Develop risk mitigation plan (Pm) : accept / transfer / remove / mitigate risks.
- Identify targets : computing, data, networking and application schema;
- Verify security intelligence of information system in real-time.
- Data schema :
-
- Dynamic data protection :
-
- check data integrity;
- assess the risks of false data injection and shilling attacks by the intruders;
- verify access control efficiency in terms of authentication, authorization, correct identification, privacy, audit, confidentiality and nonrepudiation;
- Computing schema: verify fairness, correctness, accountability, transparency, rationality, trust and commitment in multi-party computation;
- Networking schema :
-
- Verify system performance in terms of reliability, consistency, stability, liveness, deadlock-freeness, reachability, safety, resiliency;
- assess the risks of intrusion, denial of service (DoS), coremelt, Sybil, node replication and wormhole attacks;
- Application schema
-
- do penetration testing;
- audit user acceptance, system performance and quality of application integration.
 Reactive approach:
Reactive approach:
-
- adopt sense-and-respond strategy.
- assess risks of single or multiple attacks on the information system; analyze performance, sensitivity, trends, exception and alerts.
- what is corrupted or compromised?
- time series analysis : what occurred? what is occuring? what will occur?
- insights : how and why did it occur? do cause-effect analysis.
- recommend : what is the next best action?
- predict: what is the best or worst that can happen?
-
Payment function:
 Estimate aspiration point, reservation point, strong, weak, indifference and veto thresholds in the security requirements.
Estimate aspiration point, reservation point, strong, weak, indifference and veto thresholds in the security requirements.
 Trade-off proactive vs. reactive security: assign weights to each risk profile.
Trade-off proactive vs. reactive security: assign weights to each risk profile.
 Do portfolio rationalization of the security schema.
Do portfolio rationalization of the security schema.
 Select dominant strategy of IS investment from the options of process re- engineering, transformational, renewal, experiment and reinforcement on the weakest link.
Select dominant strategy of IS investment from the options of process re- engineering, transformational, renewal, experiment and reinforcement on the weakest link.
Output: Optimal security investment plan Real-time Fault Diagnostics
An intelligent adaptively secure system for monitoring, supervisory control, and diagnosis of complex operations of a smart plant may adopt data driven or analytical or knowledge based approach and is expected to have following capabilities [45-51] : (a) coordinate various tasks of process control such as monitoring, diagnosis and supervisory control; (b) integrate the solution approaches of data driven, analytical and knowledge based intelligent systems; (c) the ability to coordinate di







