4. SECURITY
Prof. Bob Taylor and Dr, Arvind Gurumurthy are analyzing the security intelligence of emerging healthcare technologies. It is essential to verify security intelligence of the technological innovation associated with cancer prevention collectively through rational threat analytics at five levels : L1, L2, L3, L4 and L5. At level L1, it is important to audit the access control mechanism for the biological system of cancer patients in terms of authentication, authorization, correct identification, confidentiality and data integrity. At level L2, it is required to verify fairness, robustness, correctness, transparency, accountability, trust and commitment. Next, it is required to verify the system performance at level L3 in terms of stability, robustness, reliability, consistency, resiliency, liveness, deadlock freeness, reachability, synchronization and safety. At level L4, it is required to assess the risks of various types of malicious attacks by adversaries on the human biological system such as Denial of Service (DoS), false data injection attack and sybil attack. At level L5, it is required to assess the risks of various types of corruptions such as agents, system administration and payment function associated with cancer treatment. It is rational to adopt an optimal mix of proactive and preventive i.e. sense-and-respond approaches to fight against cancer; the following section outlines a Deep Analytics based Cancer Prevention Mechanism (DACPM).
Deep Analytics based Cancer Prevention Mechanism [DACPM]
Agents: Defender (e.g. human agent, doctor), Attacker (e.g. malicious agent or adversary);
Model: Human biological system – (a) body, (b) mind;
Objectives: cancer prevention at optimal cost;
Constraints: budget or financial constraint, resources, time, knowledge;
Input: Perception of human agent, performance measures of biological system or test data;
Strategic moves:
-
- optimal mix of proactive and reactive approaches;
- deep learning algorithm;
- intelligent reasoning : case based reasoning (CBR), perception, analytical, logical, common sense, biomedical instrumentation;
- rational healthcare payment function and budget plan;
- adaptive secure multi-party computation;
Revelation principle: The agents preserve privacy of strategic data;
- Defender : The defenders share critical information collaboratively.
- Attacker: The adversaries do not reveal the plan of malicious attack, information of targets and weak links in advance.
 Cancer Prevention Approaches: Proactive approach:
Cancer Prevention Approaches: Proactive approach:
-
- Identify targets : computing, data, networking, security and application schema;
- Threat modeling
-
- Call threat analytics function (fa) and assess miscellaneous risk elements;
- Estimate probability (p) of occurrence along two dimensions : Low [L] and High [H];
- Estimate impact of risk i.e. sunk cost (c) along two dimensions : [L,H];
- Map threats into a set of risk profiles or classes : LL, LH,HL and HH;
- Estimate requirements of healthcare in terms of demand plan (Ppd);
- Explore risk mitigation plan (Ppm) : accept / transfer / remove / mitigate risks.
-
- Auto-immunity and vaccination;
 Optimal diet intake (e.g. fruits : amla, vegetables, nutrients) to fight against malnutrition;
Optimal diet intake (e.g. fruits : amla, vegetables, nutrients) to fight against malnutrition;
 Life-style : Avoid smoking and alcohols, food habit, drug addiction control, wild polygamy, obesity and overweight control through yoga and physical activities, stress control through meditation;
Life-style : Avoid smoking and alcohols, food habit, drug addiction control, wild polygamy, obesity and overweight control through yoga and physical activities, stress control through meditation;
 Self-healing mechanism through wearable computing based health monitoring devices which measure several health parameters in real-time such as pulse rate, temperature, blood pressure, respiration rate, heart bit and oxygen saturation rate;
Self-healing mechanism through wearable computing based health monitoring devices which measure several health parameters in real-time such as pulse rate, temperature, blood pressure, respiration rate, heart bit and oxygen saturation rate;
 Yoga for physical pain and treatment of psychological, social and spiritual trauma (as side effects of radiation and chemotherapy)
Yoga for physical pain and treatment of psychological, social and spiritual trauma (as side effects of radiation and chemotherapy)
-
- ‘Suryanamaskar’
- ‘Pranayam’ and deep breathing exercises for stress management
- Free hand exercises for muscle relaxation
o standing postures (e.g. ‘chakrasan’, ‘pada hastasan’)
o sitting postures (e.g. ‘ustrasan’ or camel pose, ‘shashangasan’ or rabit pose)
 Reactive approach:
Reactive approach:
- adopt sense-and-respond strategy.
- assess risks of single or multiple attacks on the human biological system; analyze performance, sensitivity, trends, exception and alerts.
-
- what is corrupted or compromised?
- time series analysis : what occurred? what is occuring? what will occur?
- insights : how and why did it occur? do cause-effect analysis.
- recommend : what is the next best action?
- predict: what is the best or worst that can happen?
- verify security intelligence of application, computing, networking, security and data schema of biological system.
-
- Level1: correctness, fairness, accountability, transparency, rationality, trust, commitment;
- Level2: authentication, authorization, correct identification, privacy, audit;
- Level3: safety, reliability, consistency, liveness, deadlock- freeness, reachability, resiliency;
- Level4: stability, system dynamics, quality of application integration.
- Explore risk mitigation plan (Prd and Prm).
-
- Do medical testing
 Data visualization (Refer Deep Leaning Algorithm of section 2.1)
Data visualization (Refer Deep Leaning Algorithm of section 2.1)
- Treating viral and bacterial infection, chronic inflammation, pain, diabetes, cholesterol and hormonal imbalance;
- Integrated medicine
- Regenerative medicine
- Chemotherapy and radiation
- Laser
 Fight against bad luck : Identify critical risk elements.
Fight against bad luck : Identify critical risk elements.
- Genetic disorder (sex, race, ethnicity, somatic mutation)
- Reproductive disorder (flaws in organ formation and development since birth, personal, hormonal and family history)
- Injuries from accidents, sports and games, war and crime
- Side effects of medical treatment ( e.g. hormone therapy)
- Occupational exposure (e.g. at nuclear power plant; alternative option : solar power)
- Environmental pollution (e.g. nuclear and thermal power plant)
- Hostile climate, weather and other locational disadvantages, exposure to sunshine
- Malnutrition due to poverty
- Develop risk mitigation plan in terms of organ transplantation, surgical operation, gene therapy, stem cell therapy and migration of human civilization from risky zone.
Payment function:
- Select dominant strategy of healthcare investment from the options of reinforcement on the weakest link, experimental treatment, process re- engineering, transformational and renewal.
- Estimate aspiration point, reservation point, strong, weak, indifference and veto thresholds in healthcare.
- Trade-off proactive vs. reactive security; assign weights to each approach.
- Cost of illness (COI) : health sector costs (direct cost) + decreased or lost productivity by the patient (indirect cost) + the cost of pain and suffering (intangible cost);
- Allocate healthcare budget in the ratio x:y:z where x: fund for proactive approach, y : fund for reactive approach and z: health insurance premium;
- Crowd funding campaign through social media (e.g. pediatric cancer treatment appeal at social networking site or crowd funding portal.
Output: Cancer prevention plan Deep Learning Algorithm
Objective: Computer aided cancer detection and diagnosis with improved accuracy;
Input : Medical images with optimal number of correct features;
Data preprocessing : Filter raw data from noise and incompleteness; System Architecture: Deep Convolution Neural Network (CNN); Training strategy : Ensemble learning
 Create multiple data sets from original training data;
Create multiple data sets from original training data;
 Build multiple base classifiers ( e.g. kNN, SVM, DT, RF, GBDT) for each data set;
Build multiple base classifiers ( e.g. kNN, SVM, DT, RF, GBDT) for each data set;
 Combine classifiers;
Combine classifiers;
Algorithm :
D: Original training data , n : no. of base classifiers, Dt: Test data;
for i = 1 to n do
create training data set Di from D;
build base classifier Ci on Di;
end for
for each test data x 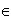 Dt
Dt
C*(x) = C1(x)  …
… Cn(x); /*
Cn(x); /*  : combination operator */
: combination operator */
end for
Testing strategy: Predictive accuracy analysis;
Output: Pattern recognition for cancer location identification, cancer tissue classification, cancer image segmentation, cancer image retrieval, big image data analysis
DACPM is basically a security game i.e. fight against cancer. It is defined by various types of elements: a group of agents, model, actions, a finite set of inputs of each agent, a finite set of outcomes as defined by output function, a set of objective functions and constraints, payments, a strategy profile, a dominant strategy which maximizes the utility of an agent for all possible strategies of other agents involved in the mechanism, security intelligence and revelation principle. There are two agents in the security game: a defender (D) and the attacker (A). Each agent adopts and executes a or a set of strategies. A pure strategy is a deterministic policy for a single move game. For many games, an agent can do better with a mixed strategy. The best strategy may depend on the knowledge of the defender about prospective attacks and the sunk costs incurred when upgrading information security schema reactively. The payment function of the mechanism estimates an optimal investment plan for the protection of human biological system. The mechanism verifies the security intelligence of human biological system; it is a multi-dimensional parameter which is defined in terms of rationality, fairness, correctness, resiliency, adaptation, transparency, accountability, trust, reliability, consistency, commitment; safety, liveness, synchronization, reachability, deadlock freeness; authentication, authorization, correct identification, non-repudiation, integrity, audit and privacy.
The DACPM mechanism evaluates security intelligence of the human biological system based on proactive and reactive approaches. The system is expected to be a resilient system. The resiliency measures the ability to and the speed at which the information system can return to normal performance level following a disruption. Adaptability is about responding to change effectively and decisively through reactive approach: the ability to identify the change in search space for the adversaries, understanding the probable impacts of the hit by the adversaries, rapid quantification what is under its control to compensate, identification what modifications to the environment are necessary and adoption of risk mitigation measures in time without any hesitation. The vulnerability of the system to a disruptive event such as cancer should be viewed as a combination of likelihood of a disruption and its potential severity. The defender must do two critical tasks: assess risks and mitigate the assessed risks. To assess risks, the defender should explore what can go wrong in the operation of the system? what is the probability of the disruption? how severe it will be? what are the consequences if the disruption occurs? A vulnerability map can be modeled through a set of expected risk metrics, probability of disruptive event and the magnitude of consequences.
The defender tries to define the payment function associated with healthcare in terms of aspiration point, reservation point and adjustment of various preferential thresholds (e.g. indifference, strong preference, weak preference, veto) and preferred solutions. Cost of illness may be estimated based on direct cost (e.g. health sector costs), indirect cost (e.g. loss of productivity of the patient) and intangible cost (e.g. cost of pain and suffering). Direct costs include hospitalization, medication, emergency transport, and medical care. Decreased or lost productivity may be the result of illness, premature death, side effects of illness or treatment or time spending receiving treatment. With premature death, the indirect cost is the loss in wage and benefits.
The computational cost of deep learning mechanism depends on the complexity of threat analytics function, deep learning algorithm and payment function. The cost of computation is a function of the complexity of threat analytics. The threat analytics analyze system performance, sensitivity, trends, exception and alerts along two dimensions: time and insights. Another major computational burden of the deep learning mechanism is the complexity of verification or model checking algorithms. The cost of computation also depends on the complexity of payment function. The appendix shows the application of DACPM for nine types of cancer as stated in scope (appendix).
It is essential to design biomedical devices in terms of security at various levels – L1, L2, L3, L4 and L5. Level L1 verifies system performance in terms of correctness of measurement of health parameters by sensors, safety, reliability, consistency, stability and robustness. The device should be safe. Safety is the most important consideration in the design of any biomedical device. Let us consider the safety aspects of artificial kidney in terms of biological, chemical, mechanical and human factors. The device should have high biocompatibility and blood compatibility; the device should not cause hemolysis i.e. destruction of red blood cells. Water quality is a major safety concern for dialysate fluid. The dialysis membrane should have high shear and ultimate strength. The device should be easy to operate and should be fool-proof. The design of artificial limbs is expected to satisfy several critical requirements such as subconscious control, user friendliness for simple learning and use, independence in multifunctional control, parallel control of multiple functions, direct access, speed of response, no sacrifice of human functional ability and natural appearance.
Security analytics for biomedical technology
 Level 1: System performance – correctness, reliability, consistency, stability, robustness, resiliency, liveness
Level 1: System performance – correctness, reliability, consistency, stability, robustness, resiliency, liveness
 Level 2 : Access control – authentication, authorization, correct identification, audit of quality control issues
Level 2 : Access control – authentication, authorization, correct identification, audit of quality control issues
 Level 3 : Design schema – safety, biological safety, mechanical safety, chemical safety, human factor safety, rationality, transparency, accountability, fairness, correctness
Level 3 : Design schema – safety, biological safety, mechanical safety, chemical safety, human factor safety, rationality, transparency, accountability, fairness, correctness
 Level 4 : Corruption – computing, data, application, networking schema
Level 4 : Corruption – computing, data, application, networking schema
 Level 5 : Malicious attack - false data injection attack, data traffic congestion, denial of service
Level 5 : Malicious attack - false data injection attack, data traffic congestion, denial of service
The other critical design issues are also associated with resiliency, deadlock- freeness, synchronization and interactive intelligent communication protocol. The safety of bio-medical devices depends on access control at level L2 in terms of authentication, authorization, correct identification of system components and audit of quality control issues. The security schema is also designed and verified at level L3 in terms of rationality, fairness, transparency, accountability, trust and commitment.
The safety of the bio-medical devices may be threatened at level L4 through corruption of computing, data, application and networking schema. The design of the bio-medical devices is also expected to assess and mitigate the risks of various types of attacks at level L5 such as false data injection, shilling and data traffic congestion. A biomedical device should be safe from the perspectives of biological, chemical, mechanical, human factor safety. Safety is one of the most important design criteria. A biomedical device should have high biocompatibility and blood compatibility. For example, an artificial kidney should not result hemolysis i.e. destruction of RBC; should not adsorb or filter blood cells; should not introduce any foreign toxic materials into blood; also remove toxic material. The quality of water is a major safety concern for dialysate fluid. The dialysis membrane should have high shear and ultimate strength and dimensional stability. A biomedical device should be easy to operate and should be fool-proof. Alarms should be incorporated into a biomedical device the dialysis machine to signal any malfunctioning of the system components.
What is bio-terrorism? This is a question of life and death in human society globally. Traditionally, it is the intentional use of biological or chemical agents to cause disease or destroy food and water supplies or capture and kill human agents for political or economic reasons to achieve malicious business intelligence [28]. Today, it is difficult to classify the illnesses caused by biological, chemical and radiological weapons from naturally occurring ailments. Our society is going through an excellent progress of life-science supply chain management and healthcare service and medical practice. But, there is threat of bio-terrorism on the soft targets such as life-science supply chain and healthcare service chain. Bio-terrorism is basically a management game in today’s business world. Bo-terrorism is generally related to the use of biological, chemical and radiological weapons in the battle fields. Most surprisingly, the definition of bio-terrorism has been changed from the use of bullets and explosives towards slow poisoning of the innocent public through innovation of new viruses, anti-viruses, drugs and toxic tasty junk food, soft drinks and beverages, flawed digital bio-medical instrumentation and unethical medical practice. It is a silent trap of death. The conflicts between security intelligence and business intelligence are inevitable. Today’s healthcare system must satisfy the basic requirements of security and safety for the benefits of the common people of the world. The analytics must explore the risk of all possible threats on the soft targets. Our society needs rational decision support system, microsoft healthcare policy and innovative medical practice to resist bio-terrorism. Is it a mission impossible? The following section outlines today’s bio-terrorism mechanism transparently.
Agents: Service provider (P), Service consumer (C), Partners of life-science supply chain, Adversaries;
Input: Data on agents, healthcare products and services;
Targets: Life-science supply chain, Healthcare service chain;
 Life-Science Supply Chain
Life-Science Supply Chain
o SCOR
-
-
- Planning: demand, inventory, production and capacity, packaging and labeling, MRP;
- Collaboration and sourcing;
- Execution -sales and distribution, order management, warehouse management, transportation management, reverse logistics;
o DCOR: innovation, product life-cycle management, pricing;
o CCOR: customer relationship management;
 Healthcare Service Chain: registration, consulting, testing, surgical operations, billing, payment processing and follow-up;
Healthcare Service Chain: registration, consulting, testing, surgical operations, billing, payment processing and follow-up;
Threats: call threat analytics and assess risks;
o Management Information System (MIS) corruption
-
-
- False data injection attack
- Sybil attack
- Private data leakage
- Flawed web security
- Flawed Knowledge Management System for creation, storage, transfer and application
o Broadcast corruption through shilling attack
o Technical snags, unreliability and inconsistency in digital bio-medical instrumentation
o Biotechnology based innovation of new germs, viruses and anti- viruses
o Life-science supply chain corruption
-
-
- Good Manufacturing Practice (GMP)
- Total Quality Management (TQM)
- Social Choice Problems ( e.g. crimes, kidnapping)
o Poor quality of service in healthcare service chain
-
-
- Transaction processing system
- Decision support system and GDSS
- Business intelligence system
-
- Malicious data mining
- Insecure data storage
- False data visualization
- Poor performance measurement
- Malicious business intelligence
-
- Greedy heuristics in payment function for revenue and profit optimization
- Economic pressure and incentive policy
- Fraudulent health insurance model
- Investment for technology management
- Irrational and dull HR policy in talent management
- Chaotics in formulation of public policy, mechanisms, regulatory compliance and corporate governance
Security intelligence verification: call intelligent threat analytics, verify security intelligence at multiple levels.
- Level 1: audit computational intelligence in terms of correctness of computation and rationality of filter configuration,
- Level 2: verify system performance of the adaptive filter in terms of reliability, consistency, resiliency and liveness;
- Level 3: malicious attacks – verify the risks of Denial of Service (DoS), false data injection, intrusion and Sybil attack on adaptive filter;
- Level 4: multi-party corruption – assess the risks of corruption of system administrator and filtering mechanism of adaptive filter;
- Level 5: verify the efficiency of access control of adaptive filter in terms of authentication, authorization, correct identification, privacy, audit, nonrepudiation, confidentiality and data integrity;
Strategic moves for risk mitigation: Scope, System, Structure, Security, Strategy, Staff-resources, Skill-Style- Support (governance and regulatory compliance, Shared vision, Service and Social networking);
Output: Plan to counter bio-terrorism
THREAT ANALYTICS
Theorem : The security intelligence is explored through threat analytics on bio- terrorism.
It is essential to verify the security intelligence of the target system (i.e. life-science supply chain and healthcare service chain) in terms of correctness, fairness, rationality, trust, transparency, accountability, reliability, consistency, confidentiality, data integrity, non-repudiation, authentication, authorization, correct identification, privacy, safety and audit. It defines the security intelligence of the system comprehensively with a novel concept of collective intelligence.
In bio-terrorism mechanism, the soft target points of adversaries may be life-science supply chain and healthcare service chain. An intelligent analytics explore miscellaneous types of threats on the targets such as information system corruption through false data injection attack, sybil attack, private