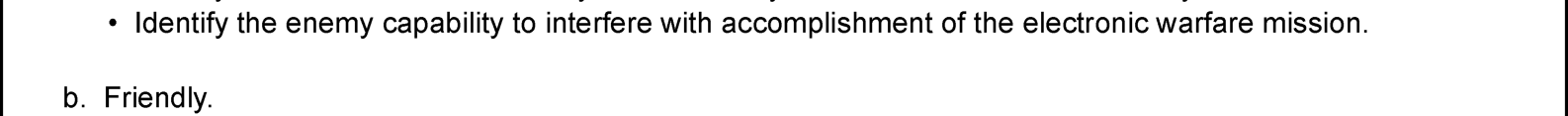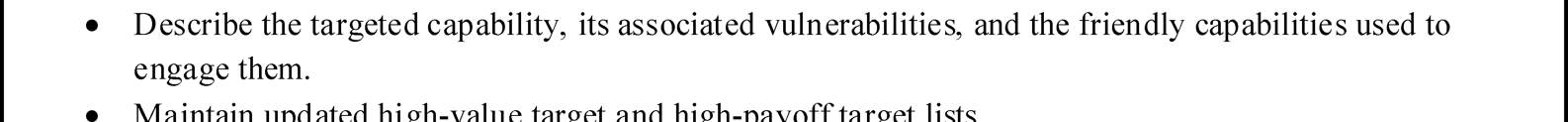7-1
Chapter 7
JOINT COMMUNICATIONS SECURITY MONITOR ACTIVITY
7-5. The Joint Communications Security Monitor Activity was created in 1993 by a memorandum of agreement between the Services’ operations deputies, Directors of the Joint Staff, and the National Security Agency. The Joint Communications Security Monitor Activity monitors (collects, analyzes, and reports) communications security of DOD telecommunications and automated information systems as well as related noncommunications signals. Its purpose is to identify potentially exploitable vulnerabilities and to recommend countermeasures and corrective actions. The Joint Communications Security Monitor Activity supports real world operations, joint exercises, and DOD systems monitoring.
JOINT INFORMATION OPERATIONS WARFARE COMMAND
7-6. The Joint Information Operations Warfare Command (JIOWC) was activated in 2006 as a functional component to the United States Strategic Command (USSTRATCOM). JIOWC integrates joint information operations into military plans, exercises, and operations across the spectrum of conflict. It is a valuable resource for commanders during the planning and execution of joint information operations.
JIOWC deploys information operations planning teams when the commander of USSTRATCOM approves a request for support. This center delivers tailored, highly skilled support and sophisticated models and simulations to joint commanders and provides information operations expertise in joint exercises and contingency operations.
7-7. JIOWC also fields the Joint Electronic Warfare Center. This center provides specialized expertise in EW. It is an innovation center for existing and emerging EW capabilities and tactics, techniques, and procedures via a network of units, labs, test ranges, and academia. The Joint Electronic Warfare Center also has EW reprogramming oversight responsibilities for the Joint Staff. This oversight includes organizing, managing, and exercising joint aspects of EW reprogramming and facilitating the exchange of joint EW reprogramming data. The actual reprogramming of equipment, however, is a Service responsibility.
JOINT SPECTRUM CENTER
7-8. The Joint Spectrum Center was activated in 1994 under the direction of the joint staff’s J-6. The Joint Spectrum Center assumed all the missions and responsibilities previously performed by the Electromagnetic Compatibility Center plus additional responsibilities. Personnel in the Joint Spectrum Center are experts in spectrum planning, electromagnetic compatibility and vulnerability, electromagnetic environmental effects, information systems, modeling and simulation, operations support, and system acquisition. The Joint Spectrum Center provides complete, spectrum-related services to combatant commanders, Services, and other government agencies. The Joint Spectrum Center deploys teams in support of the combatant commanders and serves as the DOD focal point for supporting spectrum supremacy aspects of information operations. It assists Soldiers in developing and managing the joint restricted frequency list and helps to resolve operational interference and jamming incidents. The Joint Spectrum Center can also provide databases of friendly force command and control systems for use in planning electronic protection. The Joint Spectrum Center is a field office within the Defense Spectrum Organization under the Defense Information Systems Agency.
JOINT WARFARE ANALYSIS CENTER
7-9. The Joint Warfare Analysis Center is a Navy-sponsored joint command under the J-3 established in 1994. The Joint Warfare Analysis Center assists the Chairman of the Joint Chiefs of Staff and combatant commanders in preparing and analyzing joint operational plans. It provides analysis of engineering and scientific data and integrates operational analysis with intelligence.
MARINE CORPS INFORMATION TECHNOLOGY AND NETWORK OPERATIONS CENTER
7-10. The Marine Corps Information Technology and Network Operations Center is the Marine Corps’
enterprise network operations center. The Marine Corps Information Technology and Network Operations Center is the nerve center for the central operational direction and configuration management of the Marine 7-2
FM 3-36
25 February 2009
Electronic Warfare Capabilities
Corps enterprise network. It is co-located with the Marine Corps forces computer network defense, the component to the joint task force for computer network operations, and the Marine Corps computer incident response team. This relationship provides a strong framework for integrated network management and defense.
NATIONAL SECURITY AGENCY
7-11. The National Security Agency/Central Security Service is America’s cryptologic organization. This organization protects U.S. government information systems and produces foreign signals intelligence information. Executive Order 12333, 4 December 1981, describes the responsibility of the National Security Agency/Central Security Service in more detail. The resources of National Security Agency/Central Security Service are organized for two national missions:
z
The Information Assurance Mission provides the solutions, products, and services, and conducts defensive information operations, to achieve information assurance for information infrastructures critical to U.S. national security interests.
z
The Signals Intelligence Mission allows for an effective, unified organization and control of all the foreign signals collection and processing activities of the United States. The National Security Agency is authorized to produce signals intelligence in accordance with objectives, requirements, and priorities established by the Director of National Intelligence in consultation with the President's Foreign Intelligence Advisory Board.
7-12. The Director, National Security Agency is the principal signals intelligence and information security advisor to the Secretary of Defense, Director of National Intelligence, and the Chairman of the Joint Chiefs of Staff. The Director, National Security Agency provides signals intelligence support to combatant commanders and others in accordance with their expressed formal requirements.
SUMMARY
7-13. This chapter and appendix E provide a sampling of available joint and Service EW capabilities, activities, and agencies that support ground force commanders in full spectrum operations. To leverage these capabilities for EW support, Army EW officers acquire a working knowledge of the capabilities available and the procedures for requesting support. Additionally, appendix F provides information on available EW related tools and other resources.
25 February 2009
FM 3-36
7-3
This page intentionally left blank.
Appendix A
The Electromagnetic Environment
Electromagnetic energy is both a natural and manmade occurrence. This energy, in
the form of electromagnetic radiation, consists of oscillating electric and magnetic fields and is propagated at the speed of light. Electromagnetic radiation is measured by the frequency of its wave pattern’s repetition within a set unit of time. The
standard term for the measurement of electromagnetic radiation is the hertz (Hz), the number of repetitions (cycles) per second. The electromagnetic spectrum refers to the range of frequencies of electromagnetic radiation.
OVERVIEW OF THE ELECTROMAGNETIC ENVIRONMENT
A-1. The electromagnetic environment is the resulting product of the power and time distribution, in various frequency ranges, of radiated or conducted electromagnetic emission levels. Within their intended operational environment, a military force, system, or platform may encounter these emissions while performing tasks during operations. The electromagnetic environment is the sum of—
z
Electromagnetic interference.
z
Electromagnetic pulse.
z
Hazards of electromagnetic radiation to personnel, ordnance, and volatile materials.
z
Natural phenomena effects of lightning and precipitation static. ( Precipitation static is charged precipitation particles that strike antennas and gradually charge the antenna, which ultimately discharges across the insulator, causing a burst of static [JP 3-13.1]).
25 February 2009
FM 3-36
A-1








Appendix A
THE ELECTROMAGNETIC SPECTRUM
A-2. The electromagnetic spectrum is the range of frequencies of electromagnetic radiation from zero to infinity. It is divided into 26 alphabetically designated bands (JP 1-02). The spectrum is a continuum of all electromagnetic waves arranged according to frequency and wavelength. The electromagnetic spectrum extends from below the frequencies used for modern radio (at the long-wavelength end) through gamma radiation (at the short-wavelength end). It covers wavelengths from thousands of kilometers to a fraction of the size of an atom. Figure A-1 shows the spectrum regions and wavelength segments associated with the electromagnetic spectrum.
Figure A-1. The electromagnetic spectrum
A-3. Included within the radio and microwave regions of the electromagnetic spectrum are the radio frequency and radar bands. These bands are routinely referred to by their band designators. For example, high frequency radios are HF radios and K-band radars are radars that operate between 18 and 27
gigahertz. Civilian agencies and military forces throughout the world use several different designator systems, which can result in confusion. Table A-1 shows the radio frequency band designators and their associated frequency ranges. It also shows radar band designators, associated frequency ranges, and typical usage. These are standard designations used by the United States.
A-2
FM 3-36
25 February 2009











The Electromagnetic Environment
Table A-1. Radio and radar designators and frequency bands
MILITARY OPERATIONS AND THE ELECTROMAGNETIC
ENVIRONMENT
A-4. The impact of the electromagnetic environment upon the operational capability of military forces, equipment, systems, and platforms is referred to as electromagnetic environmental effects. Electromagnetic environmental effects encompass all electromagnetic disciplines, including—
z
Electromagnetic compatibility and electromagnetic interference.
z
Electromagnetic vulnerability.
z
Electromagnetic pulse.
z
Electronic protection.
z
Hazards of electromagnetic radiation to personnel, ordnance, and volatile materials (such as fuels).
z
Natural phenomena effects of lightning and precipitation static.
A-5. Electromagnetic vulnerability consists of the characteristics of a system that cause it to suffer a definite degradation (incapability to perform the designated mission) as a result of having been subjected to a certain level of electromagnetic environmental effects (JP 3-13.1). Electronic warfare support plays a key role in identifying the electromagnetic vulnerability of an adversary’s electronic equipment and systems.
Friendly forces take advantage of these vulnerabilities through electronic warfare operations.
25 February 2009
FM 3-36
A-3
Appendix A
DIRECTED ENERGY
A-6. Directed energy refers to technologies that produce of a beam of concentrated electromagnetic energy or atomic or subatomic particles (see chapter 1). Directed-energy warfare is military action involving the use of directed-energy weapons, devices, and countermeasures to either cause direct damage or destruction of enemy equipment, facilities, and personnel, or to determine, exploit, reduce, or prevent hostile use of the electromagnetic spectrum through damage, destruction, and disruption. It also includes actions taken to protect friendly equipment, facilities, and personnel and retain friendly use of the electromagnetic spectrum (JP 1-02). A directed-energy weapon is a system using directed energy primarily as a direct means to damage or destroy enemy equipment, facilities, and personnel (JP 1-02). In addition to destructive effects, directed-energy weapons can also support area denial, crowd control, and obscuration.
A-7. The application of directed energy includes lasers, radio-frequency weapons, and particle-beam weapons. As directed-energy weapons evolve, the tactics, techniques, and procedures for their use also evolve to ensure their safe, effective employment. In electronic warfare, most directed-energy applications fit into the category of electronic attack. However, other applications can be categorized as electronic protection or even electronic warfare support. Examples include the following:
z
Applications used for electronic attack, which may include—
A laser designed to blind or disrupt optical sensors.
A millimeter wave directed-energy weapon used for crowd control.
A laser-warning receiver designed to initiate a laser countermeasure to defeat a laser weapon.
A millimeter wave obscuration system used to disrupt or defeat a millimeter wave system.
A device used to counter radio-controlled improvised explosive devices.
z
A laser-warning receiver designed solely to detect and analyze a laser signal is used for electronic warfare support.
z
A visor or goggle designed to filter out the harmful wavelength of laser light is used for electronic protection.
A-8. As the use of destructive directed-energy weapons grows, Army forces require the capability to collect information on them. Additionally, Army forces require tactics, techniques, and procedures to mitigate directed-energy weapon effects. Currently, the definitions and terms relating to directed energy are articulated within electronic warfare doctrine. As the technologies related to directed energy expand, joint and Army doctrine may discuss employing directed energy under other doctrinal subjects.
A-4
FM 3-36
25 February 2009
Appendix B
Electronic Warfare Input to Operation Plans and Orders
This appendix discusses electronic warfare input to Army and joint plans and orders.
ARMY PLANS AND ORDERS
B-1. This paragraph lists the electronic warfare (EW) information required for Army operation plans and orders. (See figure B-1 on page B-2 for the EW appendix format.) This discussion is based on current doctrine from FM 5-0. When it is republished, FM 5-0 will state where to place EW-related information in the revised plans and orders format. In addition to the appendix 4 (Electronic Warfare) to Annex P
(Information Operations), the following components of operation plans and orders may require EW input: z
Base order or plan:
Sub-subparagraph (2) (Fires) to subparagraph a (Concept of Operations) to paragraph 3
(Execution).
Sub-subparagraph (7) (Information Operations) to subparagraph a (Concept of Operations) to paragraph 3 (Execution).
z
Annex D (Fire Support):
Sub-subparagraph (4) (Electronic Warfare) to subparagraph b (Air Support) to paragraph 3
(Execution)
Appendix 1 (Air Support).
z
Annex L (Intelligence, Surveillance, and Reconnaissance):
Sub-subparagraph (2) (Fires) to subparagraph a (Concept of Operations) to paragraph 3
(Execution).
Sub-subparagraph (7) (Information Operations) to subparagraph a (Concept of Operations) to paragraph 3 (Execution).
z
Annex N (Space): Sub-subparagraph (10) (Electronic Warfare) to subparagraph b (Space Activities) to paragraph 3 (Execution).
z
Annex P (Information Operations):
Sub-sub-subparagraph (d) (Electronic Warfare) to sub-subparagraph (8) to subparagraph a (Concept of Support) to paragraph 3 (Execution).
Sub-subparagraph (3) (List of Tasks to Electronic Warfare Units) to subparagraph b (Tasks to Subordinate Units) to paragraph 3 (Execution).
25 February 2009
FM 3-36
B-1



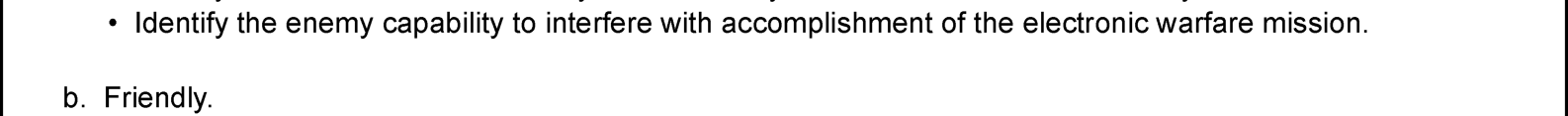











Appendix B
Figure B-1. Appendix 4 (Electronic Warfare) to annex P (Information Operations) instructions JOINT PLANS AND ORDERS
B-2. If required to provide EW input to portions of a joint order, the primary areas for input are the following:
z
Paragraph 3 (Execution) to appendix 3 (Information Operations) to Annex C (Operations).
z
Tab B (Electronic Warfare) to appendix 3 (Information Operations) to Annex C (Operations).
B-3. See CJCSM 3122.03C for the Joint Operations Planning and Execution System format.
B-2
FM 3-36
25 February 2009
Appendix C
Electronic Warfare Running Estimate
This appendix discusses the electronic warfare running estimate. A running estimate is a staff section’s continuous assessment of current and future operations to
determine if the current operation is proceeding according to the commander’s intent and if future operations are supportable (FM 3-0).
C-1. The electronic warfare (EW) running estimate is used to support the military decisionmaking process during planning and execution. During planning, the EW running estimate provides an assessment of the supportability of each proposed course of action from an EW perspective. The format of the EW running estimate closely parallels the steps of the military decisionmaking process. It serves as the primary tool for recording the EW officer’s assessments, analyses, and recommendations for EW operations. The EW
officer and staff in the EW working group are responsible for conducting the analysis and providing recommendations based on the EW running estimate.
C-2. A complete EW running estimate should contain the information necessary to answer any question the commander may pose. If there are gaps in the EW running estimate, the staff identifies the gaps as information requirements and submits them to the intelligence cell. The EW running estimate can form the basis for EW input required in other applicable appendixes and annexes within operation plans and orders.
Figure C-1 on page C-2 provides a sample EW running estimate for use during planning.
25 February 2009
FM 3-36
C-1














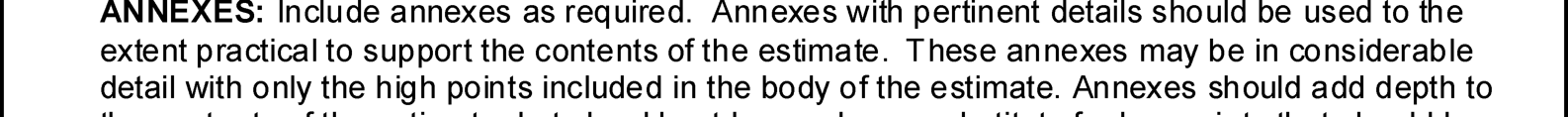

Appendix C
Figure C-1. Example of an electronic warfare running estimate
C-3. Once the commander approves the order, the EW running estimate is used to inform current and future operations. During execution the EW running estimate is used to help determine if current EW
operations are proceeding according to plan and if future EW operations are supportable. Figure C-2, page C-3, shows a sample of the information that might be used to update the EW running estimate during execution. The EW officer and supporting staff members within the EW working group produce and update the running estimate.
C-2
FM 3-36
25 February 2009










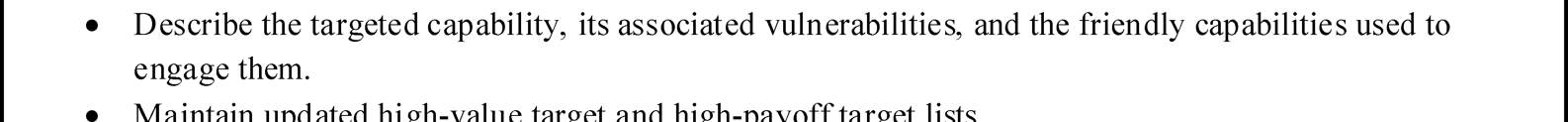




Electronic Warfare Running Estimate
Figure C-2. Sample update information to the electronic warfare running estimate 25 February 2009
FM 3-36
C-3
This page intentionally left blank.
Appendix D
Electronic Warfare-Related Reports and Messages
This appendix provides information and ref